Configuring an ike proposal, Table 5 – H3C Technologies H3C SecPath F1000-E User Manual
Page 137
125
Table 5 Configuration items
Item
Description
IKE Local Name
Enter a name for the local security gateway.
If the local device acts as the IKE negotiation initiator and uses the ID type of Fully
Qualified Domain Name (FQDN) or the user FQDN of the security gateway for IKE
negotiation, you need to configure this argument on the local device. Then, the local
device sends its gateway name as identification to its peer and the peer uses the locally
configured remote gateway name to authenticate the local device. Make sure that the
local gateway name configured here is identical to the remote gateway name configured
on its peer.
By default, the device name is used as the local gateway name.
NAT Keepalive
Interval
Set the interval at which the ISAKMP SA sends NAT keepalive packets to its peer.
NAT mappings on a NAT gateway may get aged. If no packet traverses an IPsec tunnel
in a certain period of time, the NAT mapping will be deleted, disabling the tunnel beyond
the NAT gateway from transferring data. To prevent NAT mappings from being aged, an
ISAKMP SA sends to its peer NAT keepalive packets at a certain interval to keep the NAT
session alive.
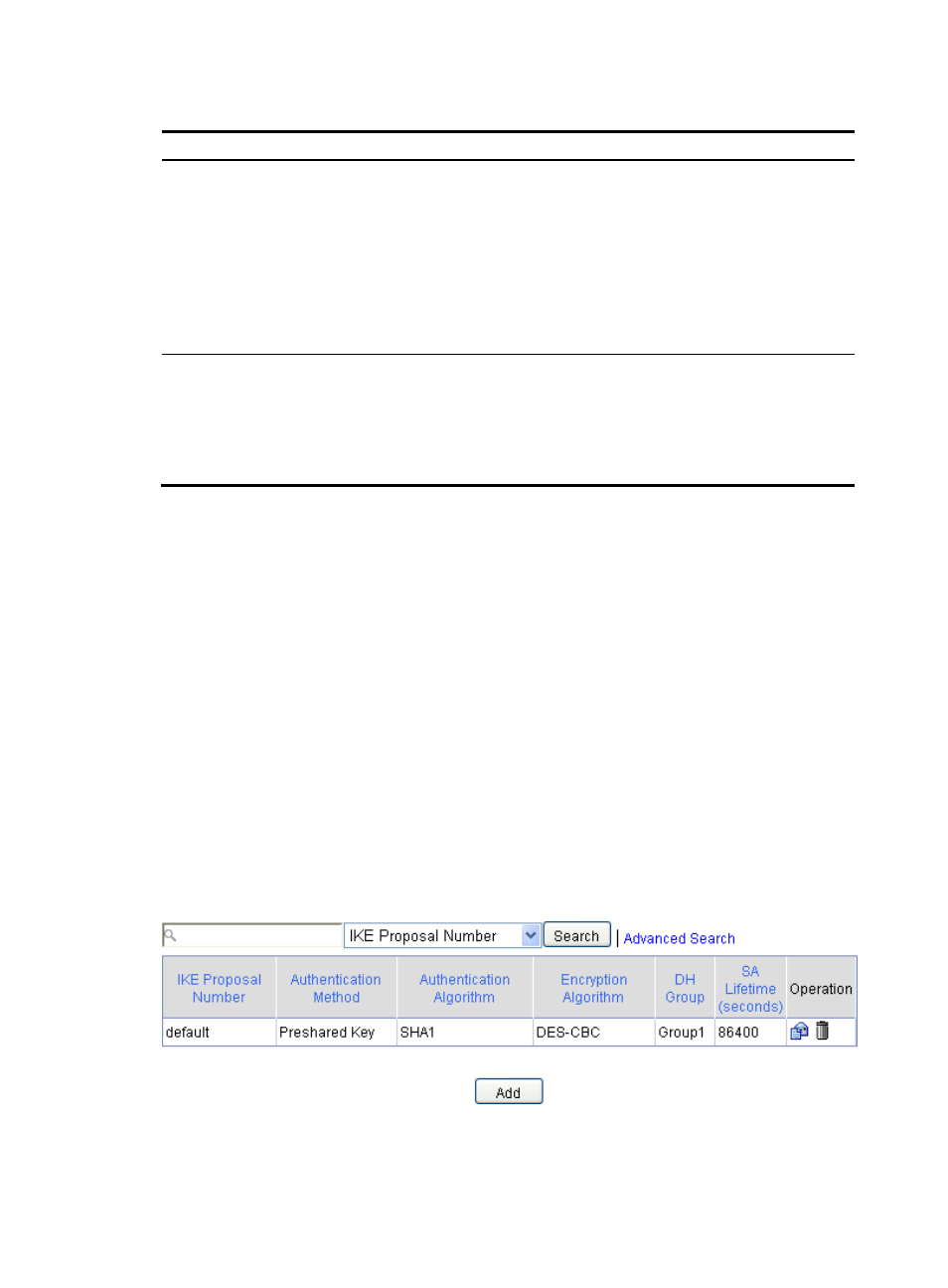
Configuring an IKE proposal
An IKE proposal defines a set of attributes describing how IKE negotiation should take place. You may
create multiple IKE proposals with different preferences. The preference of an IKE proposal is represented
by its sequence number, and the smaller the sequence number, the higher the preference.
Two peers must have at least one pair of matched IKE proposals for successful IKE negotiation. During
IKE negotiation, the negotiation initiator sends its IKE proposals to the peer. The peer will match the IKE
proposals against its own IKE proposals, starting with the one with the smallest sequence number. The
match goes on until a match is found or all IKE proposals are found mismatched. The matched IKE
proposals will be used to establish the security tunnel.
Two matched IKE proposals have the same encryption algorithm, authentication method, authentication
algorithm, and DH group. The ISAKMP SA lifetime will take the smaller one of the two matched IKE
proposals.
To configure an IKE proposal:
1.
Select VPN > IKE > Proposal from the navigation tree.
Figure 83 IKE proposal list
2.
Click Add.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
