Managing public keys, Feature and hardware compatibility, Overview – H3C Technologies H3C SecPath F1000-E User Manual
Page 338: Basic concepts, Key algorithm types
326
Managing public keys
NOTE:
The public key configuration is available only at the CLI.
Feature and hardware compatibility
Feature F1000-A-EI/E-SI/S-AI
F1000-E
F5000-A5 Firewall
module
FIPS No
No
No
Yes
Overview
Basic concepts
•
Algorithm—A set of transformation rules for encryption and decryption.
•
Plain text—Information without being encrypted.
•
Cipher text—Encrypted information.
•
Key—A string of characters that controls the transformation between plain text and cipher text. It is
used in both the encryption and decryption.
Key algorithm types
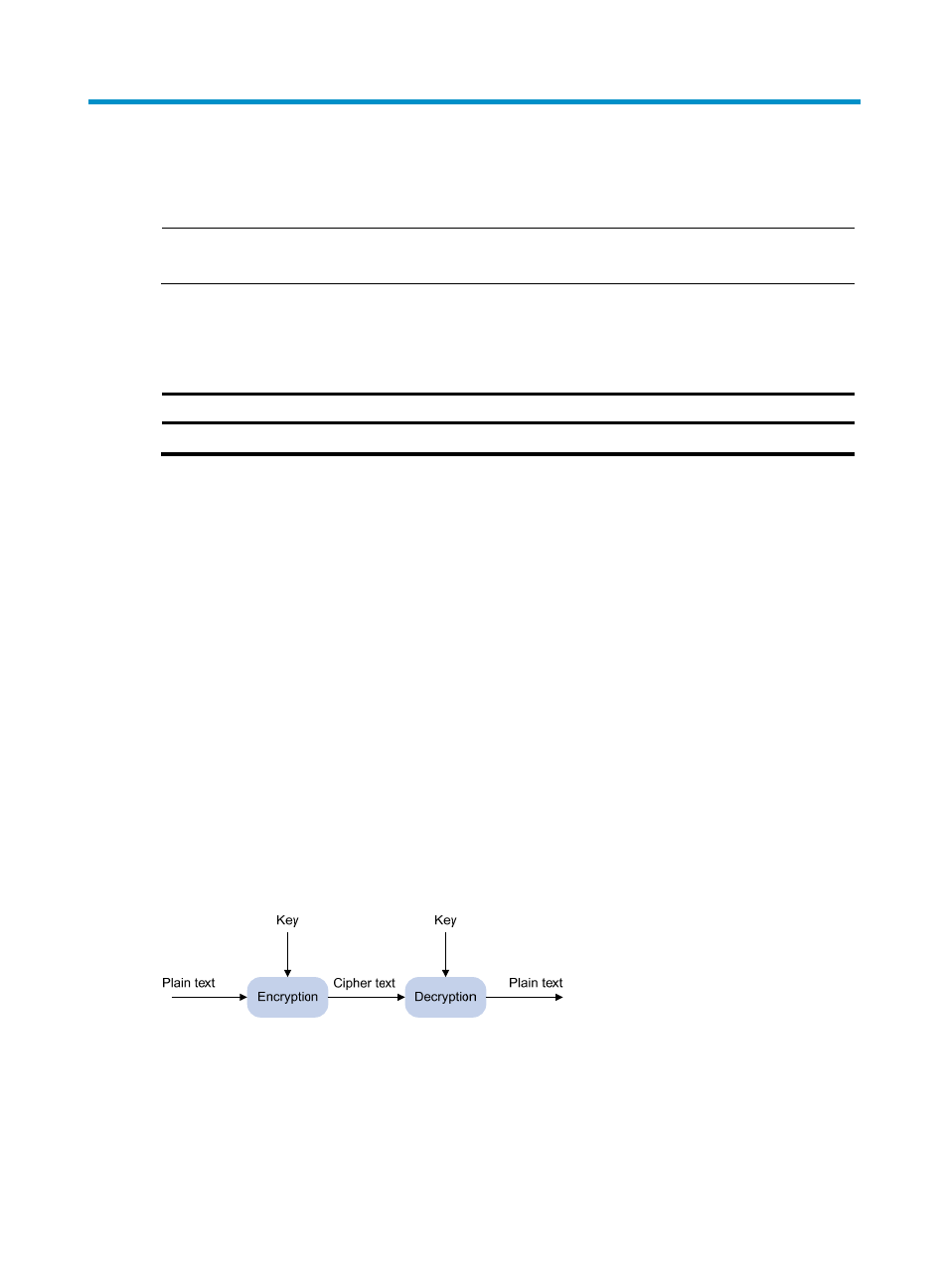
As shown in
, the information in plain text is encrypted by an algorithm with the help of a key
before being sent. The resulting cipher text is transmitted across the network to the receiver, where it is
decrypted by the same algorithm also with the help of a key to obtain the original plain text.
Figure 211 Encryption and decryption
The following types of key algorithms are available, based on whether the keys for encryption and
decryption are the same:
•
Symmetric key algorithm—The keys for encryption and decryption are the same. Commonly used
symmetric key algorithms include Advanced Encryption Standard (AES) and Data Encryption
Standard (DES).
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
