Ike configuration examples at the cli, Network requirements, Configuring secpath a – H3C Technologies H3C SecPath F1000-E User Manual
Page 153
141
Task Command
Remarks
Clear SAs established by IKE.
reset ike sa [ connection-id ]
Available in user view
IKE configuration examples at the CLI
Main mode IKE with pre-shared key authentication
configuration example
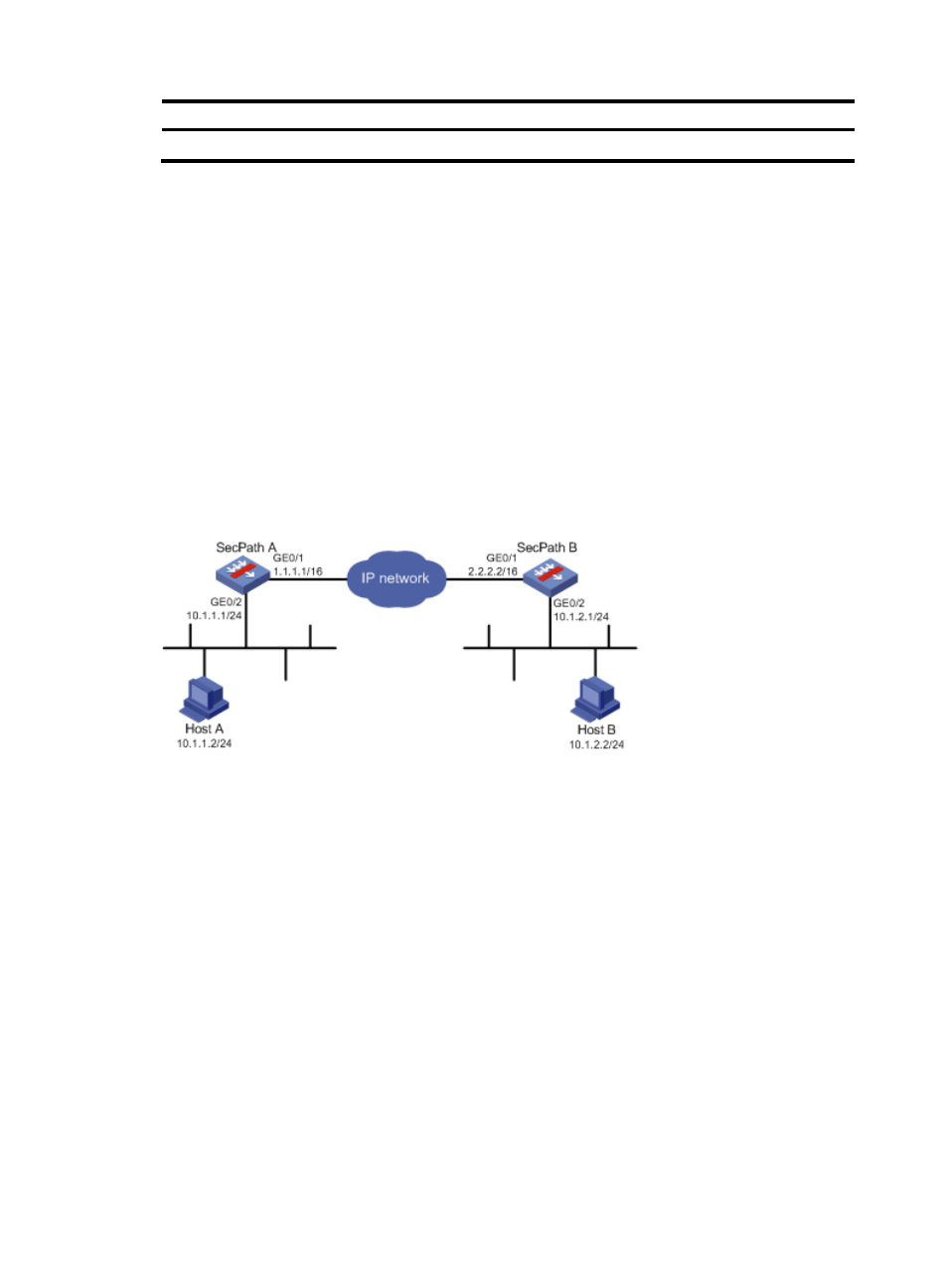
Network requirements
As shown in
, configure an IPsec tunnel that uses IKE negotiation between SecPath A and
SecPath B to secure the communication between subnet 10.1.1.0/24 and subnet 10.1.2.0/24.
For SecPath A, configure an IKE proposal that uses the sequence number 10 and authentication
algorithm MD5. Leave SecPath B with only the default IKE proposal. Configure the two firewalls to use the
pre-shared key authentication method.
Figure 93 Network diagram
Configuring SecPath A
Make sure that SecPath A and SecPath B can reach each other.
# Configure ACL 3101 to identify traffic from subnet 10.1.1.0/24 to subnet 10.1.2.0/24.
[SecPathA] acl number 3101
[SecPathA-acl-adv-3101] rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0
0.0.0.255
[SecPathA-acl-adv-3101] quit
# Create IPsec proposal tran1.
[SecPathA] ipsec proposal tran1
# Set the packet encapsulation mode to tunnel.
[SecPathA-ipsec-proposal-tran1] encapsulation-mode tunnel
# Use security protocol ESP.
[SecPathA-ipsec-proposal-tran1] transform esp
# Specify encryption and authentication methods.
[SecPathA-ipsec-proposal-tran1] esp encryption-algorithm des
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
