Basic p2mp gre tunnel configuration example, Network requirements – H3C Technologies H3C SecPath F1000-E User Manual
Page 41
29
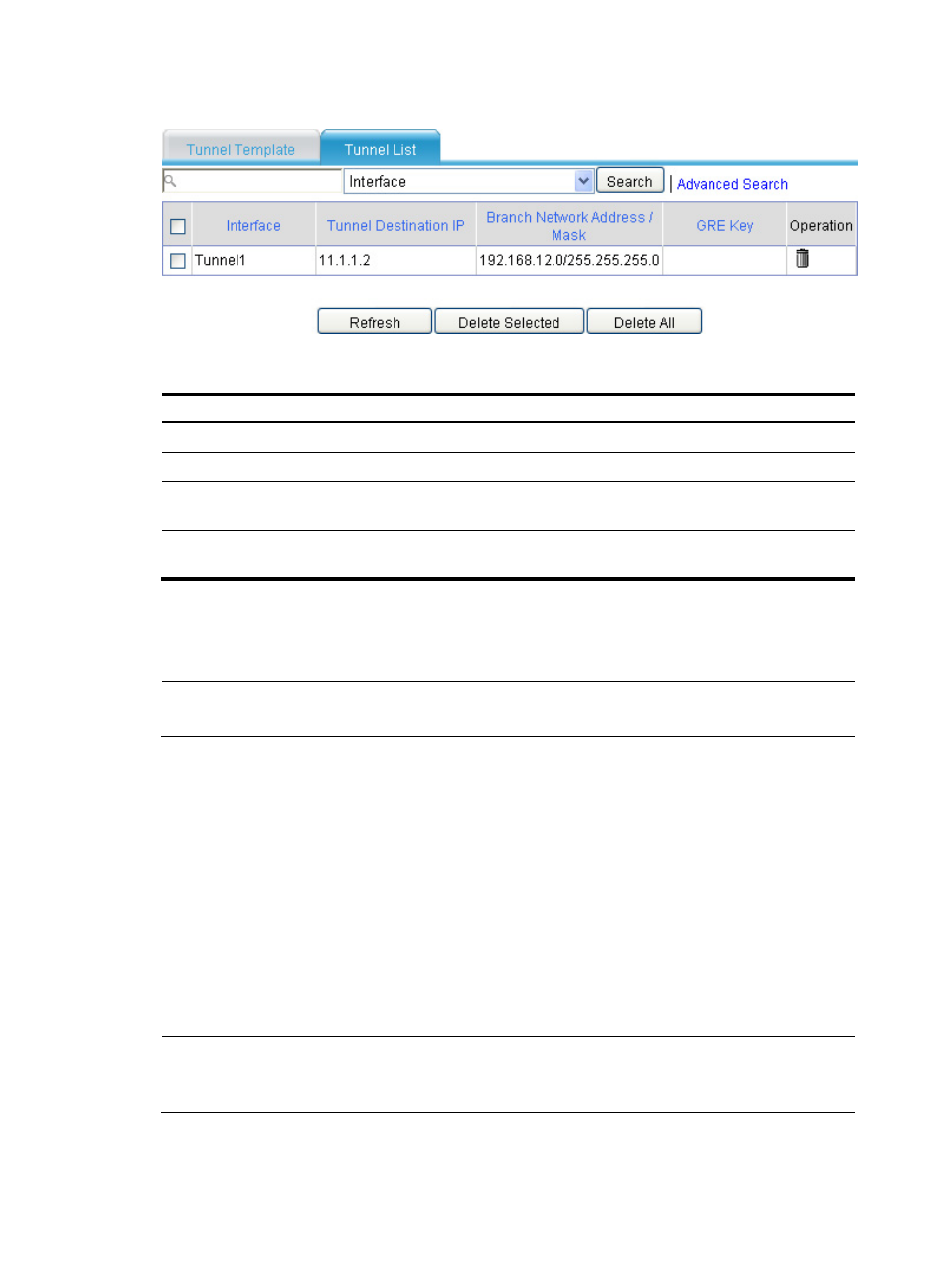
Figure 23 Tunnel list
Table 3 Field description
Field Description
Tunnel Interface
Name of the tunnel interface
Tunnel Dest Address
IP address of the tunnel destination
Branch Network
Address/Mask
IP address and mask of the branch network
GRE Key
GRE key of the tunnel, used to identify the priority of the tunnel entry. If the tunnel peer
device is not configured with a GRE key, nothing will be displayed for this field.
Basic P2MP GRE tunnel configuration example
NOTE:
In this configuration example, either Device A or Device B is the SecPath firewall.
Network requirements
A company has a network at the headquarters and each of its branches. It is required to implement
communication between the headquarters and the branches through GRE.
shows a simplified
scenario, where there is only one branch.
•
Device A is the gateway at the headquarters, and Device B is the gateway of the branch.
•
Host A is an internal user at the headquarters and Host B is an internal user at the branch. A GRE
tunnel is established between Device A and Device B to implement communication between Host A
and Host B.
If you use P2P GRE tunnels, the number of GRE tunnels to be configured is the same as that of the
branches. To simplify the configuration at the headquarters, you can create a P2MP GRE tunnel interface
on Device A, and configure a GRE over IPv4 tunnel interface on Device B.
NOTE:
This example gives only the configuration of one branch gateway (Device B). The configuration on other
branch gateways is similar.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
