Configuring ike at the cli, Ike configuration task list, Figure 92 – H3C Technologies H3C SecPath F1000-E User Manual
Page 146
134
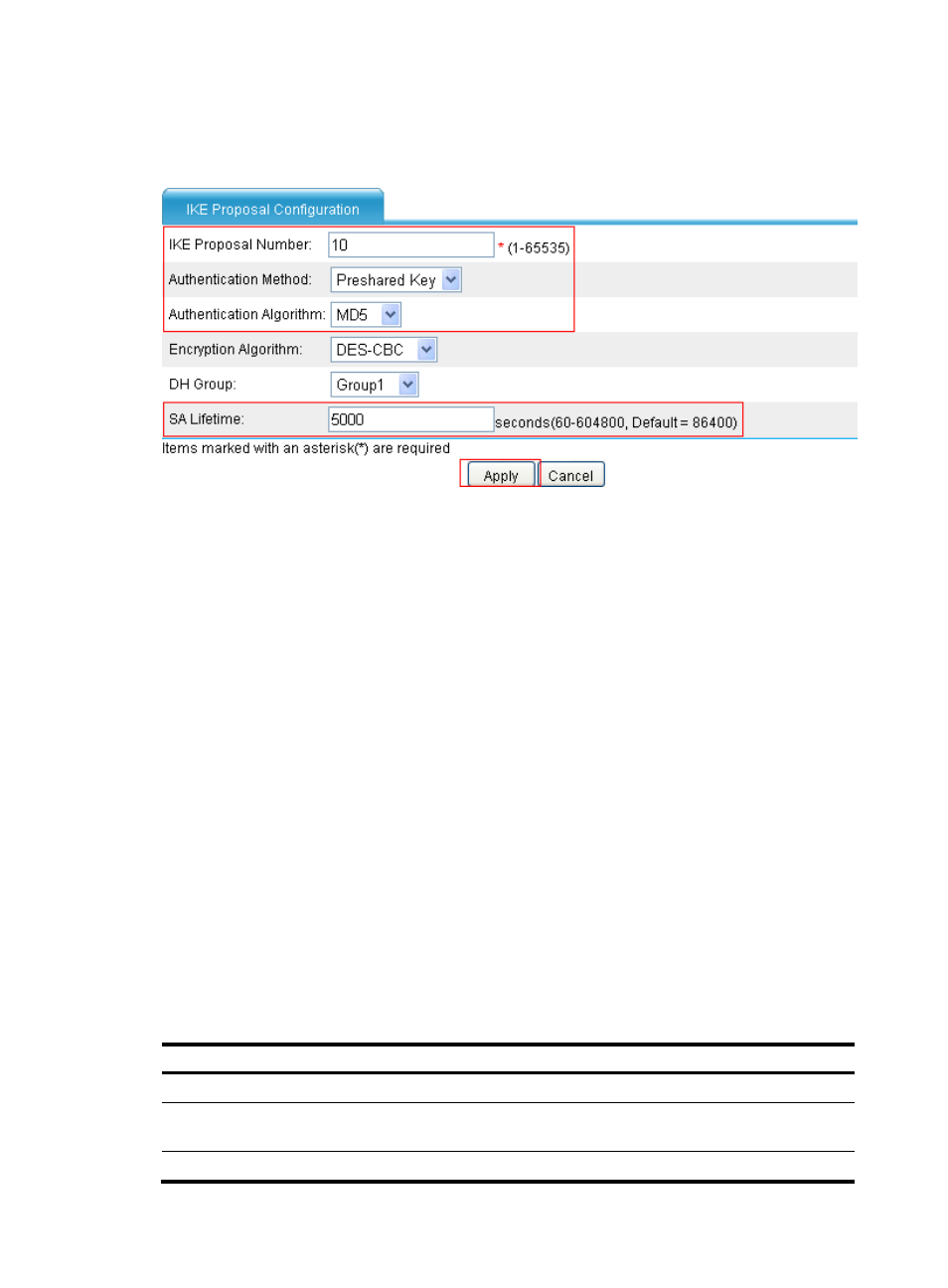
Enter 5000 as the SA lifetime.
c.
Click Apply.
Figure 92 Creating an IKE proposal numbered 10
3.
Configuring the IKE peer on Device B:
a.
Select VPN > IKE > Peer from the navigation tree and then click Add.
The IKE peer configuration page appears, as shown in
.
b.
Perform the following operations on the page:
Enter peer as the peer name.
Select Main as the negotiation mode.
Enter 1.1.1.1 as the remote gateway IP address.
Select Pre-Shared Key and enter abcde as the pre-shared key.
c.
Click Apply.
After you complete the configuration, security gateways Device A and Device B can perform IKE
negotiation. Device A is configured with an IKE proposal numbered 10, which uses the authentication
algorithm of MD5; but Device B has only a default IKE proposal, which uses the default authentication
algorithm of SHA. Device B has no proposal matching proposal 10 of Device A, and the two devices
have only one pair of matched proposals, namely the default IKE proposals. The two devices do not need
to have the same ISAKMP SA lifetime; they will negotiate one.
Configuring IKE at the CLI
IKE configuration task list
Task Remarks
Configuring a name for the local security gateway
Optional.
Required if you want to specify an IKE proposal for an
IKE peer to reference.
Required.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
