Configuring acls, Permit/deny actions in acls – H3C Technologies H3C SecPath F1000-E User Manual
Page 171
159
Configuring ACLs
Permit/Deny actions in ACLs
IPsec uses ACLs to identify data flows. An ACL is a collection of ACL rules. Each ACL rule is a deny or
permit statement. A permit statement identifies a data flow protected by IPsec, and a deny statement
identifies a data flow that is not protected by IPsec. IPsec uses referenced ACL to match against packets.
The matching process stops once a match is found or ends with no match hit. The packet is handled as
follows:
•
Each ACL rule matches both the outbound traffic and the returned inbound traffic. Suppose there is
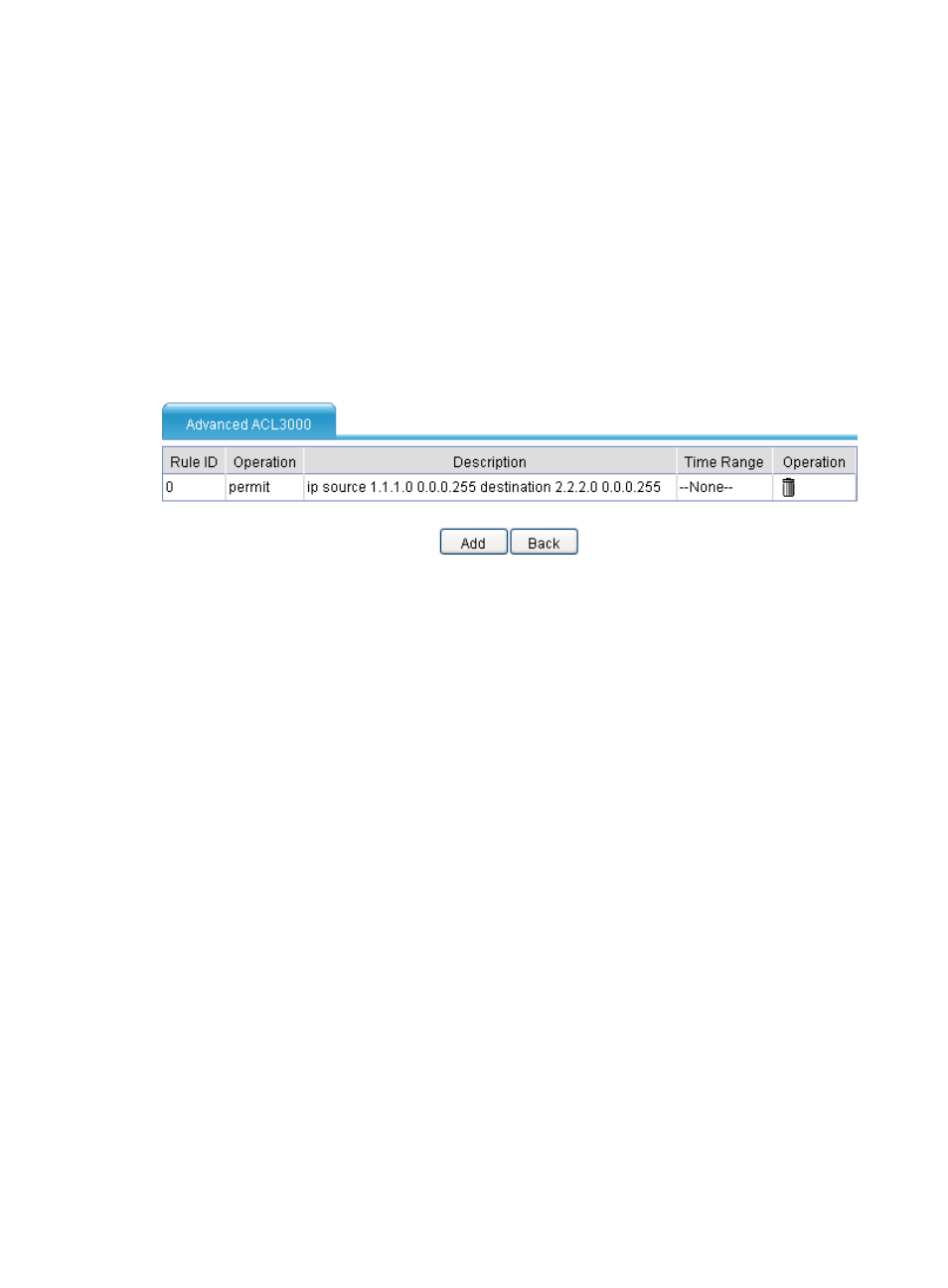
a rule as shown in
. This rule matches both traffic from 1.1.1.0 to 2.2.2.0 and returned
traffic from 2.2.2.0 to 1.1.1.0.
Figure 100 An ACL referenced in an IPsec policy
•
In the outbound direction, if a permit statement is matched, IPsec considers the packet as requiring
protection and continues to process it. If a deny statement is matched or no match is found, IPsec
considers the packet as not requiring protection and delivers it to the next function module.
•
In the inbound direction, if the packet is an IPsec packet and matches a permit statement, IPsec
receives and processes the packet. If the packet is not an IPsec packet and matches a permit
statement, it is discarded.
When defining ACL rules for IPsec, follow these guidelines:
•
Make sure that only the data flows to be protected by IPsec are defined in permit statements. If a
packet is protected at the entry of the IPsec tunnel but not at the exit of the IPsec tunnel, it will be
dropped.
•
Avoid statement conflicts in the scope of IPsec policy groups. When creating a deny statement, be
careful with its matching scope and matching order relative to permit statements. The policies in an
IPsec policy group have different match priorities. ACL rule conflicts between them are prone to
cause mistreatment of packets. For example, when you configure a permit statement for an IPsec
policy to protect an outbound traffic flow, you must avoid the situation that the traffic flow matches
a deny statement in a higher priority IPsec policy. Otherwise, the packets will be sent out as normal
packets; if they match a permit statement at the receiving end, they will be dropped by IPsec.
The following uses a configuration example to show how a statement conflict causes packet drop. In this
example, only the ACL-related configurations are presented.
Device A connects the segment 1.1.2.0/24 and Device B connects the segment 3.3.3.0/24. On Device
A, apply the IPsec policy group test to the outbound interface to Device B. The IPsec policy group
contains two policies, test 1 and test 2. The ACLs referenced by the two policies each contain a rule that
matches traffic from 1.1.2.0/24 to 3.3.3.0/24. The one referenced in policy test 1 is a deny statement
and the one referenced in policy test 2 is a permit statement. Because test 1 is matched prior to test 2,
traffic from 1.1.2.0/24 to 3.3.3.0/24 will match the deny statement and sent as normal traffic. When the
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
