Westermo MR Series User Manual
Page 158
158
6622-3201
Web Interface and Command Line Reference Guide
www.westermo.com
Duration (kb):
As an alternative to negotiating new keys based on duration of connection, the “lifetime” of a
session may be set based on the amount of data transferred. This parameter is used to specify
the validity of an SA in terms of the maximum amount of data (in kb) that may be transmitted
before a new phase 2 key exchange will be initiated. A value of 0 means that the default value of
32Mb is used.
Inactivity Timeout (s):
When set to a non-zero value, any IPsec SAs associated with the eroute that haven’t been used
for the configured period of time get removed. If zero value is used, this parameter is ignored.
No SA action:
This parameter determines how the router will respond if it receives a request to route a
packet that matches an Eroute definition (i.e. source address, destination address, protocol etc.
match) but for which no SAs exist. When set to “Use IKE”, it will try to initiate an IKE ses-
sion to establish SAs. When set to “Drop Packet” it will discard the packet. When set to “Pass
Packet” it will allow the packet through without authentication or encryption.
Create SAs automatically:
When this parameter is set to “Yes”, the Eroute will automatically attempt to create an IPSec
SA (VPN Tunnel) regardless of whether the unit needs to route any packets to the remote sub-
net or not. This effectively creates an “always on” Eroute.
If the parameter is set to “Yes, Route with matching interface required” the Eroute (VPN) will
be activated. The Eroute will remain active for the length of the “Duration” parameter and or
the “Inactivity Timeout”.
Authentication method:
This parameter specifies the “key” used between VPN endpoints to encrypt and de-crypt data.
The “Pre-shared keys” option requires that both the remote and host system (initiator and
responder) share a secret key, or password, that can be matched by the responder to the ini-
tiator calling in. Selecting “RSA signatures” invokes the use of X.509 certificates (see “X.509
Certificates” in the “IPSec and VPNs” section for more information). To configure users and
their passwords or pre shared secrets, you must populate the user table with details of the
remote system’s ID (IP address in Main mode and ID string in Aggressive mode), and the pass-
word to use (see Configure > Users).
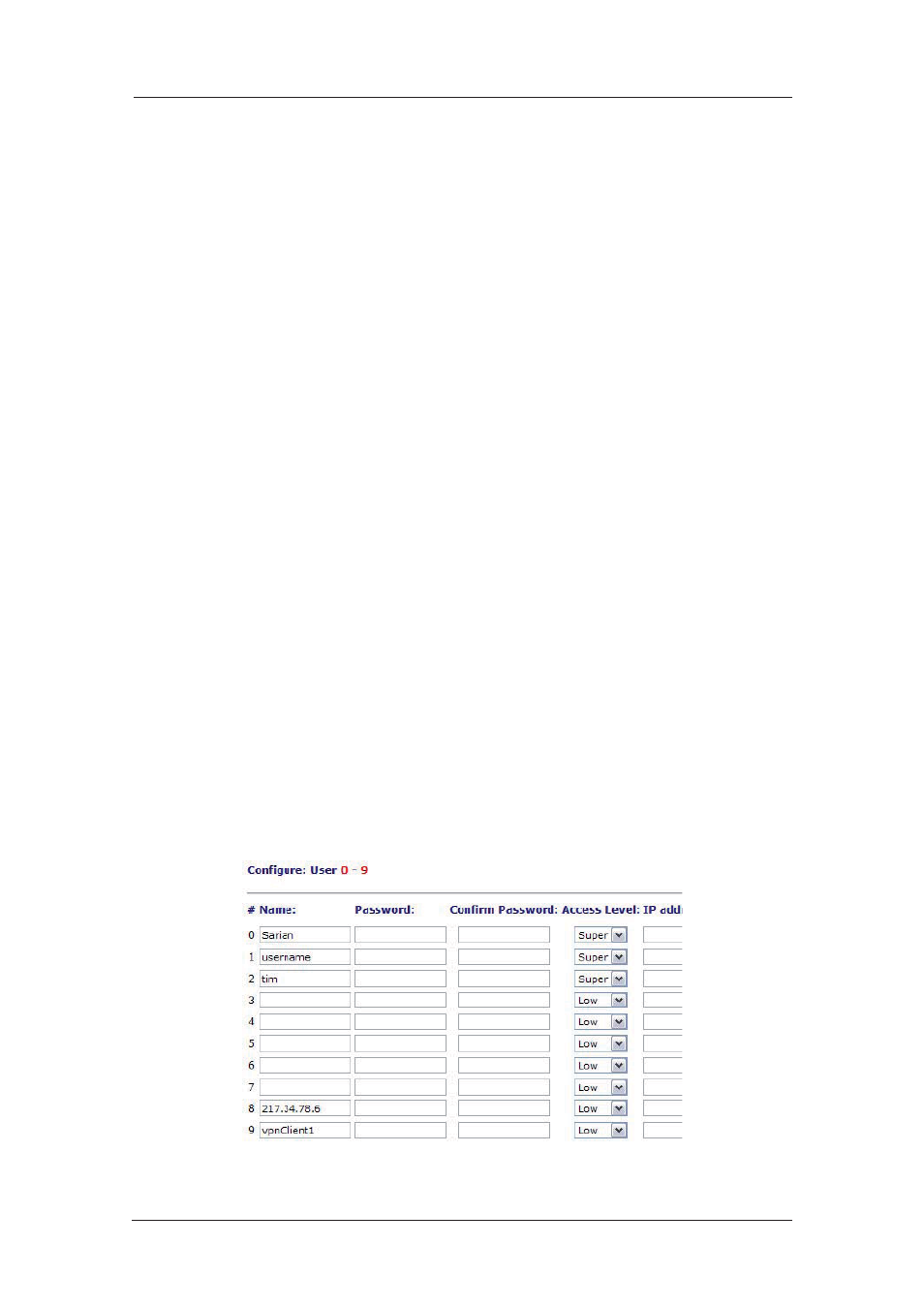
The user table serves a dual purpose in that it may contain a series of entries for normal login
access (i.e. for dial-in HTTP, FTP or Telnet access) and entries for IPSec look-up. In the screen-
shot below entries 1-3 are for normal login access, entry 10 stores the shared secret for a
remote unit which will connect in Main mode and entry 11 contains the shared secret for a
remote unit that will connect in Aggressive mode.
