5 802.1x authentication, 1x authentication, Fig. 4.1 – Siemens S223 User Manual
Page 64: Process of 802.1x authentication
UMN:CLI User Manual
SURPASS hiD 6615 S223/S323 R1.5
64 A50010-Y3-C150-2-7619
4.5 802.1x
Authentication
To enhance security and portability of network management, there are two ways of au-
thentication based on MAC address and port-based authentication which restrict clients
attempting to access to port. The port-based authentication (802.1x) decides to give ac-
cess to RADIUS server having the information about user who tries to access.
802.1x authentication adopts EAP (Extensible Authentication Protocol) structure. In EAP
system, there are EAP-MD5 (Message Digest 5), EAP-TLS (Transport Level Security),
EAP-SRP (Secure Remote Password), EAP-TTLS(Tunneled TLS) and the hiD 6615
S223/S323 supports EAP-MD5 and EAP-TLS. Accessing with user’s ID and password,
EAP-MD5 is one-way Authentication based on the password. EAP-TLS accesses through
the mutual authentication system of server authentication and personal authentication
and it is possible to guarantee high security because of mutual authentication system.
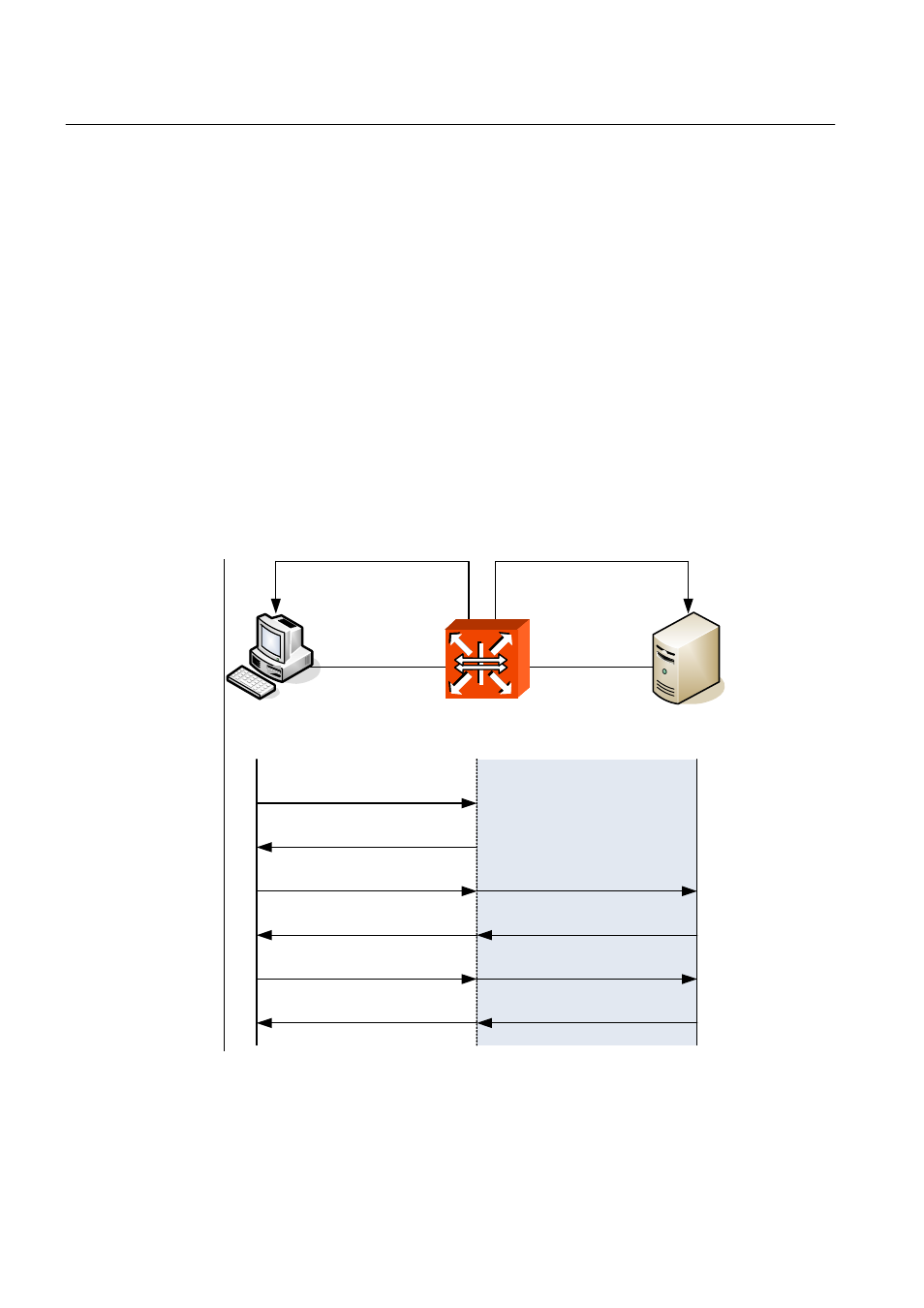
At a request of user Authentication, from user’s PC EAPOL-Start type of packets are
transmitted to authenticator and authenticator again requests identification. After getting
respond about identification, request to approve access to RADIUS server and be au-
thenticated by checking access through user’s information.
The following figure explains the process of 802.1x authentication.
]
[Suppliant]
[Authenticator]
[Authentication Server]
EAPOL
(EAP over LAN)
EAP over RADIUS
EAPOL-Start
EAP-Request / Identity
EAP-Response / Identity
RADIUS-Access-Request
RADIUS-Access-Challenge
EAP-Request
EAP-Response
RADIUS-Access-Request
EAP-Success
RADIUS-Access-Accept
RADIUS
Server
Fig. 4.1
Process of 802.1x Authentication
To enable 802.1x authentication on port of the hiD 6615 S223/S323, you should be able
to perform the following tasks.
