Endpoint-to-gateway tunnel, Roadwarrior configuration, Ipsec protocols – Brocade Fabric OS Administrators Guide (Supporting Fabric OS v7.3.0) User Manual
Page 246
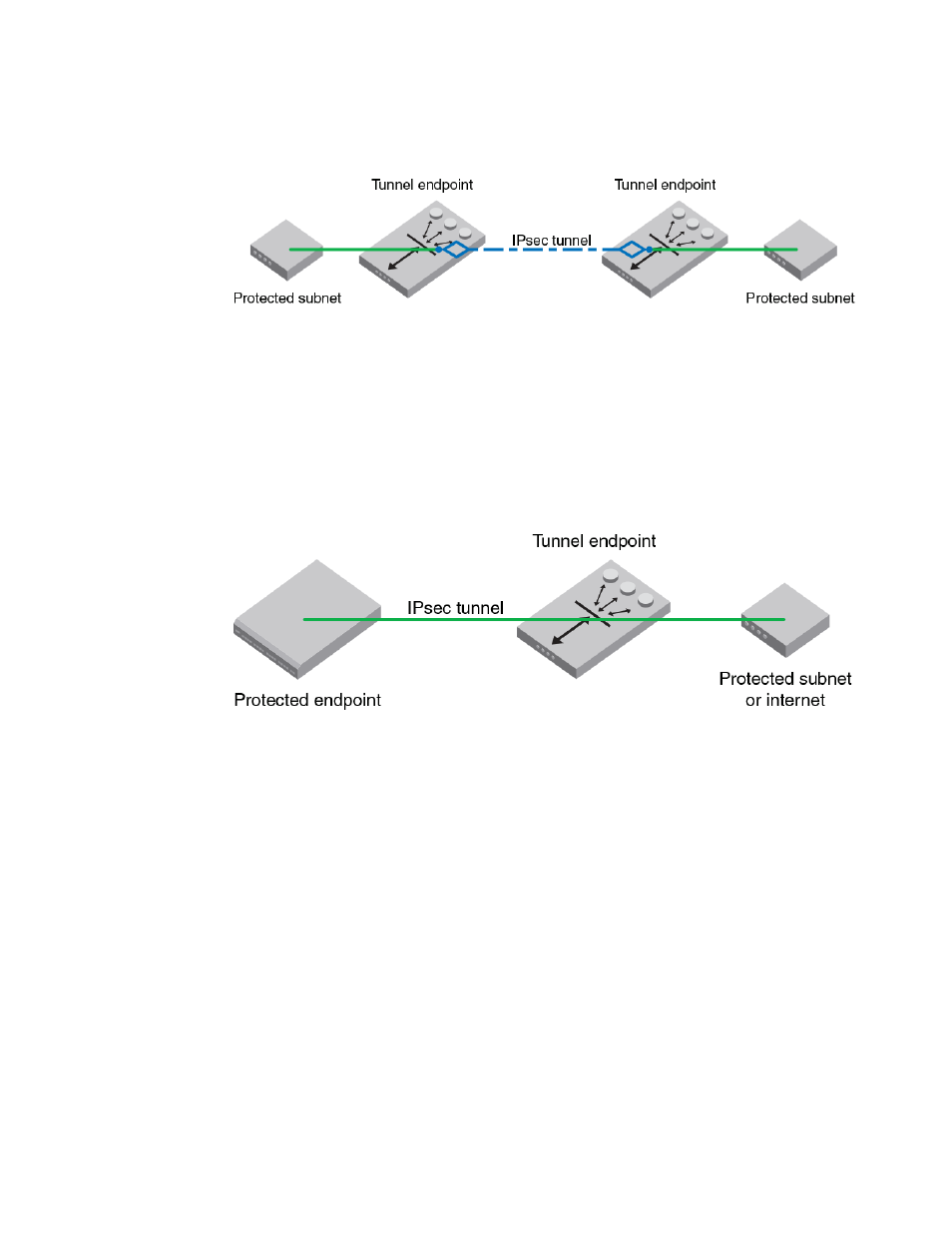
FIGURE 16 Gateway tunnel configuration
Endpoint-to-gateway tunnel
In this scenario, a protected endpoint (typically a portable computer) connects back to its corporate
network through an IPsec-protected tunnel. It might use this tunnel only to access information on the
corporate network, or it might tunnel all of its traffic back through the corporate network in order to take
advantage of protection provided by a corporate firewall against Internet-based attacks. In either case,
the protected endpoint will want an IP address associated with the security gateway so that packets
returned to it will go to the security gateway and be tunneled back.
FIGURE 17 Endpoint-to-gateway tunnel configuration
RoadWarrior configuration
In endpoint-to-endpoint security, packets are encrypted and decrypted by the host which produces or
consumes the traffic. In the gateway-to-gateway example, a router on the network encrypts and
decrypts the packets on behalf of the hosts on a protected network. A combination of the two is
referred to as a RoadWarrior configuration where a host on the Internet requires access to a network
through a security gateway that is protecting the network.
IPsec protocols
IPsec ensures confidentiality, integrity, and authentication using the following protocols:
• Authentication Header (AH)
• Encapsulating Security Payload (ESP)
IPsec protocols protect IP datagram integrity using hash message authentication codes (HMAC).
Using hash algorithms with the contents of the IP datagram and a secret key, the IPsec protocols
generate this HMAC and add it to the protocol header. The receiver must have access to the secret
key in order to decode the hash.
Endpoint-to-gateway tunnel
246
Fabric OS Administrators Guide
53-1003130-01
