Root guard, Enabling stp root guard – Brocade FastIron Ethernet Switch Platform and Layer 2 Switching Configuration Guide User Manual
Page 326
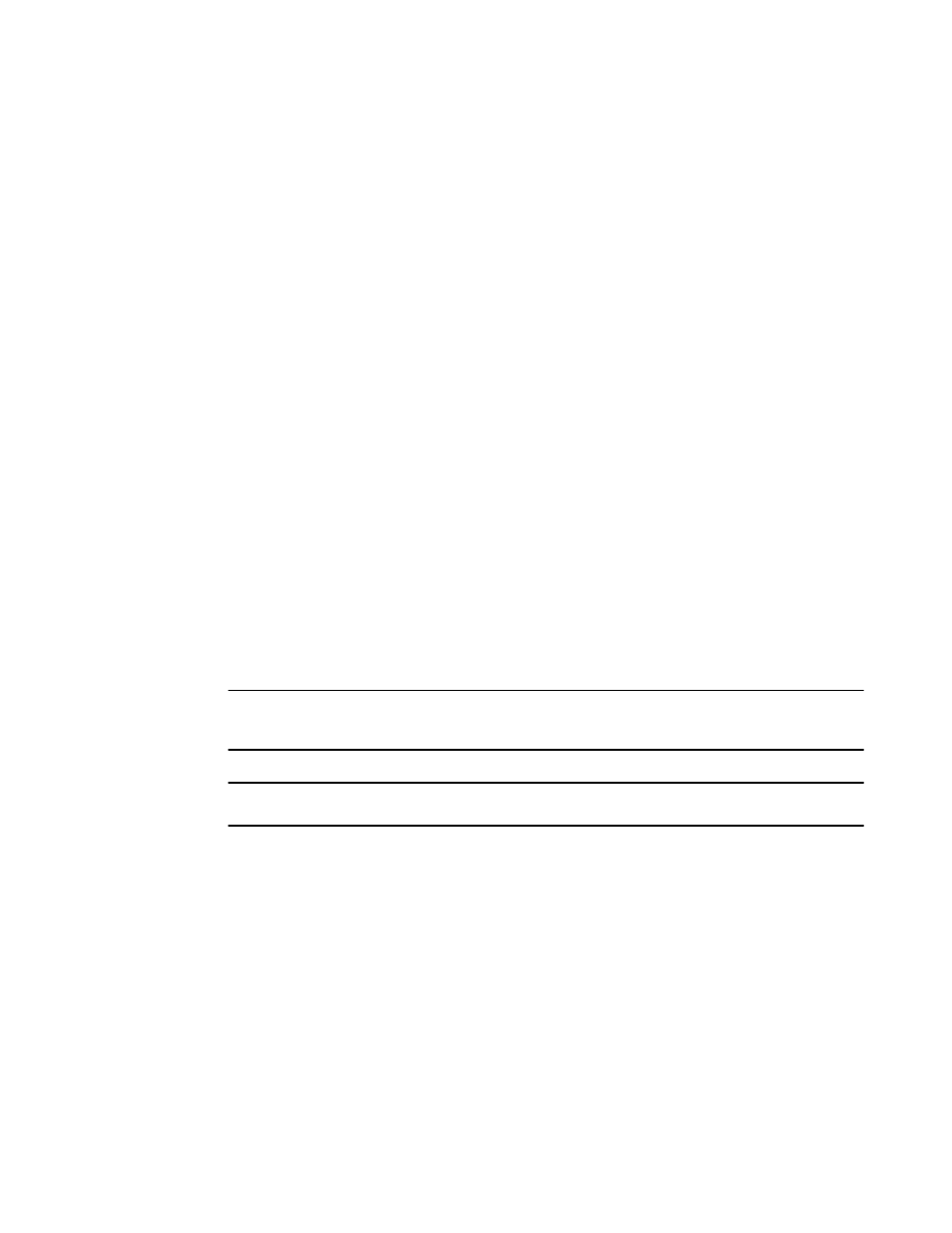
A console message such as the following is generated after a BPDU guard violation occurs on a
system that is running RSTP.
device(config-vlan-1)#RSTP: Received BPDU on BPDU guard enabled Port 23
(vlan=1),errdisable Port 23
Root guard
The standard STP (802.1D), RSTP (802.1W) or 802.1S does not provide any way for a network
administrator to securely enforce the topology of a switched layer 2 network. The forwarding topology
of a switched network is calculated based on the root bridge position, along with other parameters.
This means any switch can be the root bridge in a network as long as it has the lowest bridge ID. The
administrator cannot enforce the position of the root bridge. A better forwarding topology comes with
the requirement to place the root bridge at a specific predetermined location. Root Guard can be used
to predetermine a root bridge location and prevent rogue or unwanted switches from becoming the
root bridge.
When root guard is enabled on a port, it keeps the port in a designated role. If the port receives a
superior STP Bridge Protocol Data Units (BPDU), it puts the port into a ROOT-INCONSISTANT state
and triggers a log message and an SNMP trap. The ROOT-INCONSISTANT state is equivalent to the
BLOCKING state in 802.1D and to the DISCARDING state in 802.1W. No further traffic is forwarded
on this port. This allows the bridge to prevent traffic from being forwarded on ports connected to rogue
or misconfigured STP bridges.
Once the port stops receiving superior BPDUs, root guard automatically sets the port back to learning,
and eventually to a forwarding state through the spanning-tree algorithm.
Configure root guard on all ports where the root bridge should not appear. This establishes a
protective network perimeter around the core bridged network, cutting it off from the user network.
NOTE
Root guard may prevent network connectivity if it is improperly configured. Root guard must be
configured on the perimeter of the network rather than the core.
NOTE
Root guard is not supported when MSTP is enabled.
Enabling STP root guard
An STP root guard is configured on an interface by entering commands similar to the following.
device(config)#interface ethernet 5/5
device(config-if-e10000-5/5)spanning-tree root-protect
Syntax: [no] spanning-tree root-protect
Enter the no form of the command to disable STP root guard on the port.
Root guard
326
FastIron Ethernet Switch Platform and Layer 2 Switching Configuration Guide
53-1003086-04
