Pki configuration examples, Network requirements, Configuration procedure – H3C Technologies H3C WX3000E Series Wireless Switches User Manual
Page 292
278
Task Command
Remarks
Display CRLs.
display pki crl domain
domain-name [ | { begin | exclude
| include } regular-expression ]
Available in any view
Display information about one or
all certificate attribute groups.
display pki certificate
attribute-group { group-name |
all } [ | { begin | exclude |
include } regular-expression ]
Available in any view
Display information about one or
all certificate attribute-based
access control policies.
display pki certificate
access-control-policy { policy-name
| all } [ | { begin | exclude |
include } regular-expression ]
Available in any view
PKI configuration examples
CAUTION:
•
When the CA uses Windows Server, the SCEP add-on is required, and you must use the certificate
request from ra command to specify that the entity request a certificate from an RA.
•
When the CA uses RSA Keon, the SCEP add-on is not required, and you must use the certificate request
from ca command to specify that the entity request a certificate from a CA.
Requesting a certificate from a CA running RSA Keon
Network requirements
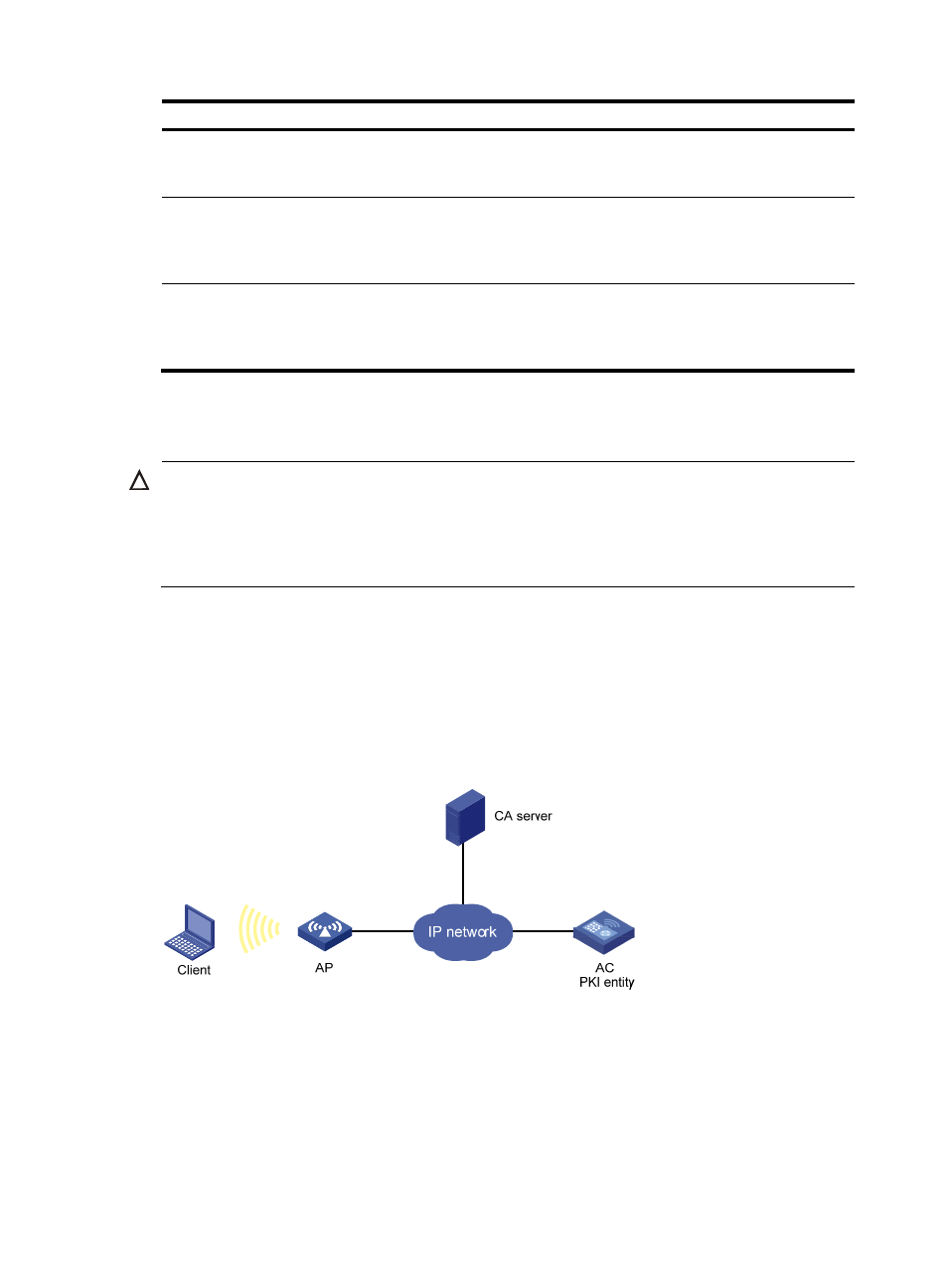
As shown in
, the AC submits a local certificate request to the CA server.
The AC acquires the CRLs for certificate verification.
Figure 123 Network diagram
Configuration procedure
1.
Configure the CA server
# Create a CA server named myca.
In this example, configure these basic attributes on the CA server:
•
Nickname: Name of the trusted CA.
- H3C WX5500E Series Access Controllers H3C WX3500E Series Access Controllers H3C WX2500E Series Access Controllers H3C WX6000 Series Access Controllers H3C WX5000 Series Access Controllers H3C LSWM1WCM10 Access Controller Module H3C LSUM3WCMD0 Access Controller Module H3C LSUM1WCME0 Access Controller Module H3C LSWM1WCM20 Access Controller Module H3C LSQM1WCMB0 Access Controller Module H3C LSRM1WCM2A1 Access Controller Module H3C LSBM1WCM2A0 Access Controller Module H3C WA3600 Series Access Points H3C WA2600 Series WLAN Access Points H3C S10500 Series Switches H3C S5800 Series Switches H3C S5820X Series Switches H3C S12500 Series Switches H3C S9500E Series Switches H3C MSR 5600 H3C MSR 50 H3C MSR 3600 H3C MSR 30 H3C MSR 2600 H3C MSR 20-2X[40] H3C MSR 20-1X H3C MSR 930 H3C MSR 900 H3C SR8800 H3C SR6600-X H3C SR6600 H3C SecPath F5020 H3C SecPath F5040 H3C VMSG VFW1000
