1 instruction decoding, 2 .1 instruction decoding -4, Figure 2-2 . instruction word format -4 – Maxim Integrated MAXQ610 User Manual
Page 8: Maxq610 user’s guide
2-4
MAXQ610 User’s Guide
Memory access from the MAXQ610 is based on a Harvard architecture with separate address spaces for program
and data memory . The simple instruction set and transport-triggered architecture allow the MAXQ610 to decode and
execute nearly all instructions in a single clock cycle . Data memory is accessed through one of three data pointer
registers . Two of these data pointers, DP[0] and DP[1], are stand-alone 16-bit pointers . The third data pointer, FP, is
composed of a 16-bit base pointer (BP) and an offset register (OFFS) . All three pointers support postincrement/decre-
ment functionality for read operations and preincrement/decrement for write operations . For the frame pointer (FP =
BP[OFFS]), the increment/decrement operation is executed on the OFFS register and does not affect the base pointer
(BP) . Stack functionality is accessible through the stack pointer (SP) . Program memory is read accessible through the
code pointer (CP), which supports postincrement/decrement functionality .
2.1 Instruction Decoding
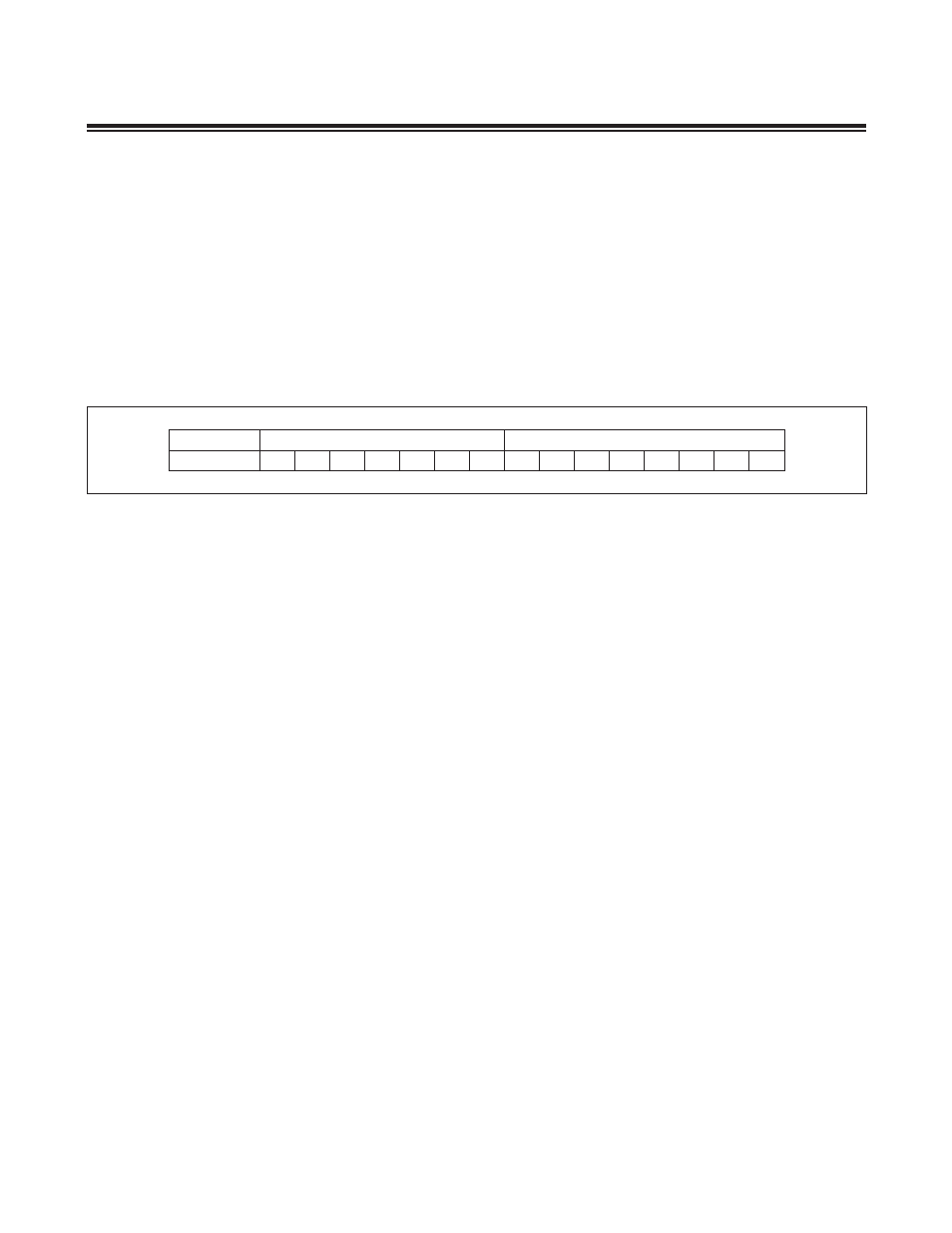
Every MAXQ instruction is encoded as a single 16-bit word according to the format shown in Figure 2-2 .
Bit 15 (f) indicates the format for the source field of the instruction as follows:
• If f equals 0, the instruction is an immediate source instruction, and the source field represents an immediate 8-bit
value .
• If f equals 1, the instruction is a register source instruction, and the source field represents the register from which
the source value is read .
Bits 0 to 7 (ssssssss) represent the source for the transfer . Depending on the value of the format field, this can either
be an immediate value or a source register . If this field represents a register, the lower 4 bits contain the module speci-
fier and the upper 4 bits contain the register index in that module .
Bits 8 to 14 (ddddddd) represent the destination for the transfer . This value always represents a destination register,
with the lower 4 bits containing the module specifier and the upper 3 bits containing the register subindex within that
module .
Because the source field is 8 bits wide and 4 bits are required to specify the module, any one of 16 registers in that
module can be specified as a source . However, the destination field has one less bit, which means that only eight
registers in a module can be specified as a destination in a single-cycle instruction .
While the asymmetry between source and destination fields of the op code can initially be considered a limitation,
this space can be used effectively . First, since read-only registers can never be specified as destinations, they can
be placed in the second eight locations in a module to give single-cycle read access . Second, there are often critical
control or configuration bits associated with system and certain peripheral modules where limited write access is ben-
eficial (e .g ., watchdog timer enable and reset bits) . By placing such bits in one of the upper 24 registers of a module,
this write protection is added in a way that is virtually transparent to the assembly source code . Anytime that it is nec-
essary to directly select one of the upper 24 registers as a destination, the prefix register, PFX, is used to supply the
extra destination bits . This prefix register write is inserted automatically by the assembler/compiler and requires
one additional execution cycle.
The MAXQ architecture is transport-triggered . This means that writing to or reading from certain register locations also
causes side effects . These side effects form the basis for the higher level op codes defined by the assembler, such
as ADDC, OR, JUMP, and so on . These op codes are actually implemented as MOVE instructions between certain
register locations, while the encoding is handled by the assembler/compiler and need not be a concern to the
programmer. The registers defined in the system register and peripheral register maps operate as described in the
documentation; the unused empty locations are the ones used for these special cases .
Figure 2-2. Instruction Word Format
format
Destination
source
f
d
d
d
d
d
d
d
s
s
s
s
s
s
s
s
