21 configuring roaming authentication, Roaming authentication example, Roaming authentication prerequisites – H3C Technologies H3C Intelligent Management Center User Manual
Page 430: Ation, see, 21 configuring roaming, Authentication
412
21 Configuring roaming authentication
Roaming authentication requires at least two AAA servers. It takes place between the visited and
registration networks, when a user attempt s to access the visited network. The visited network server
does not have the user information needed to authenticate the user, but works with the registration
network server that does have the information, so the user can be authenticated.
Roaming authentication example
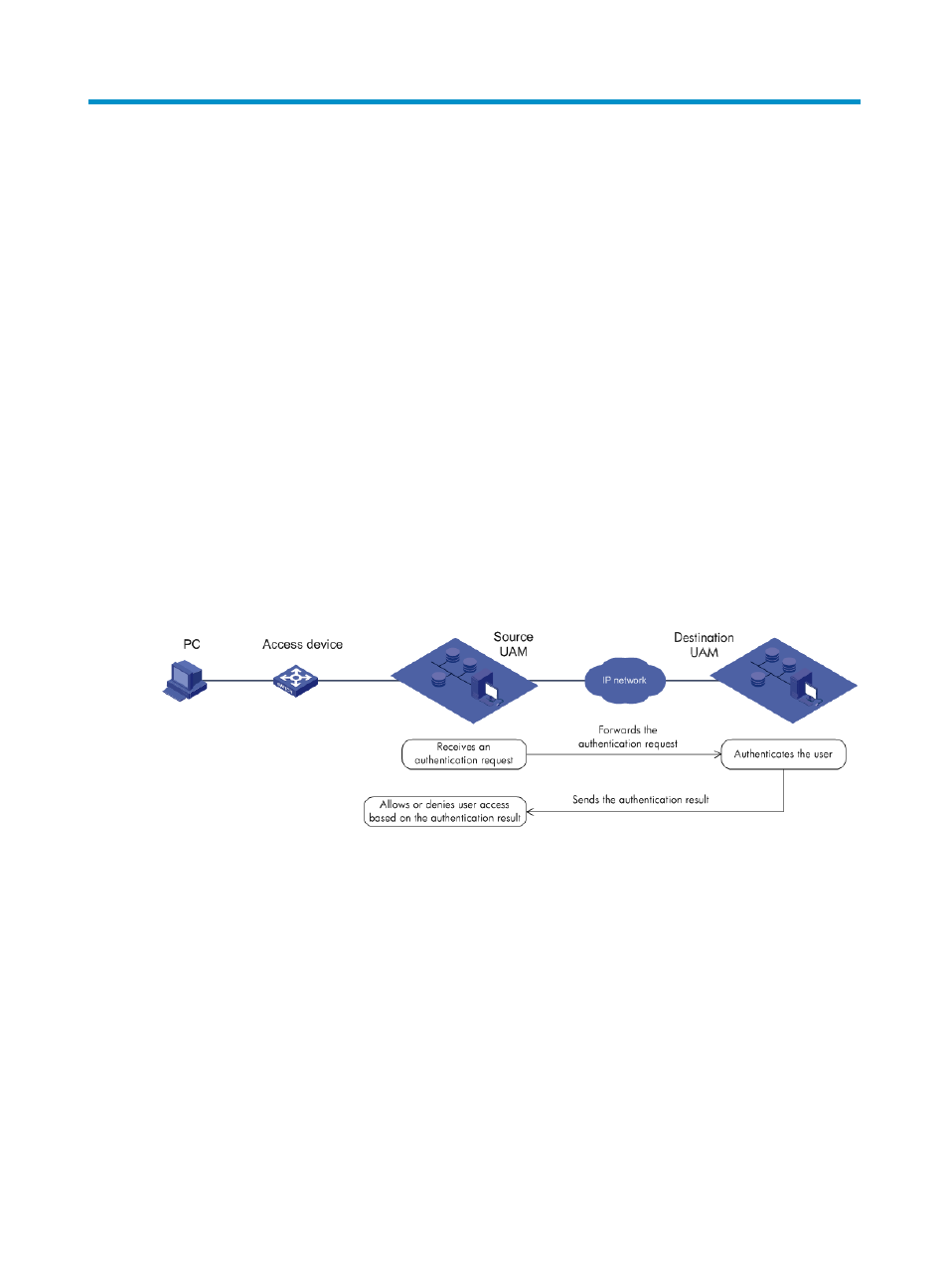
A roaming authentication process example, using two UAM servers, is shown in
:
1.
The source UAM receives a user authentication request. However, the source UAM does not have
the user information needed to authenticate the user. A source UAM is also known as a roaming
UAM.
2.
The source UAM forwards the authentication request to the destination UAM. A destination UAM
is also known as a local UAM.
3.
The destination UAM has the user information. It authenticates the user, and sends the
authentication result to the source UAM.
4.
Based on the authentication result, the source UAM allows or denies user's access to the network.
Figure 108 Roaming authentication process
Roaming authentication prerequisites
To implement roaming authentication, both the destination UAM and the source UAM require
configuration, as follows:
•
On the destination UAM, configure the source UAM as an access device.
•
On the source UAM, enable and configure the roaming function.
Unavailable UAM functions in roaming authentication
The following UAM functions are not available in roaming authentication:
•
Binding computer name.
•
Binding the computer to a Windows domain.
