Rockwell Automation 1783-WAPxxx Stratix 5100 Wireless Access Point User Manual User Manual
Page 85
Rockwell Automation Publication 1783-UM006A-EN-P - May 2014
85
Stratix 5100 Device Manager Parameter Definitions
Chapter 4
Security Configuration Settings on the Easy Setup Page
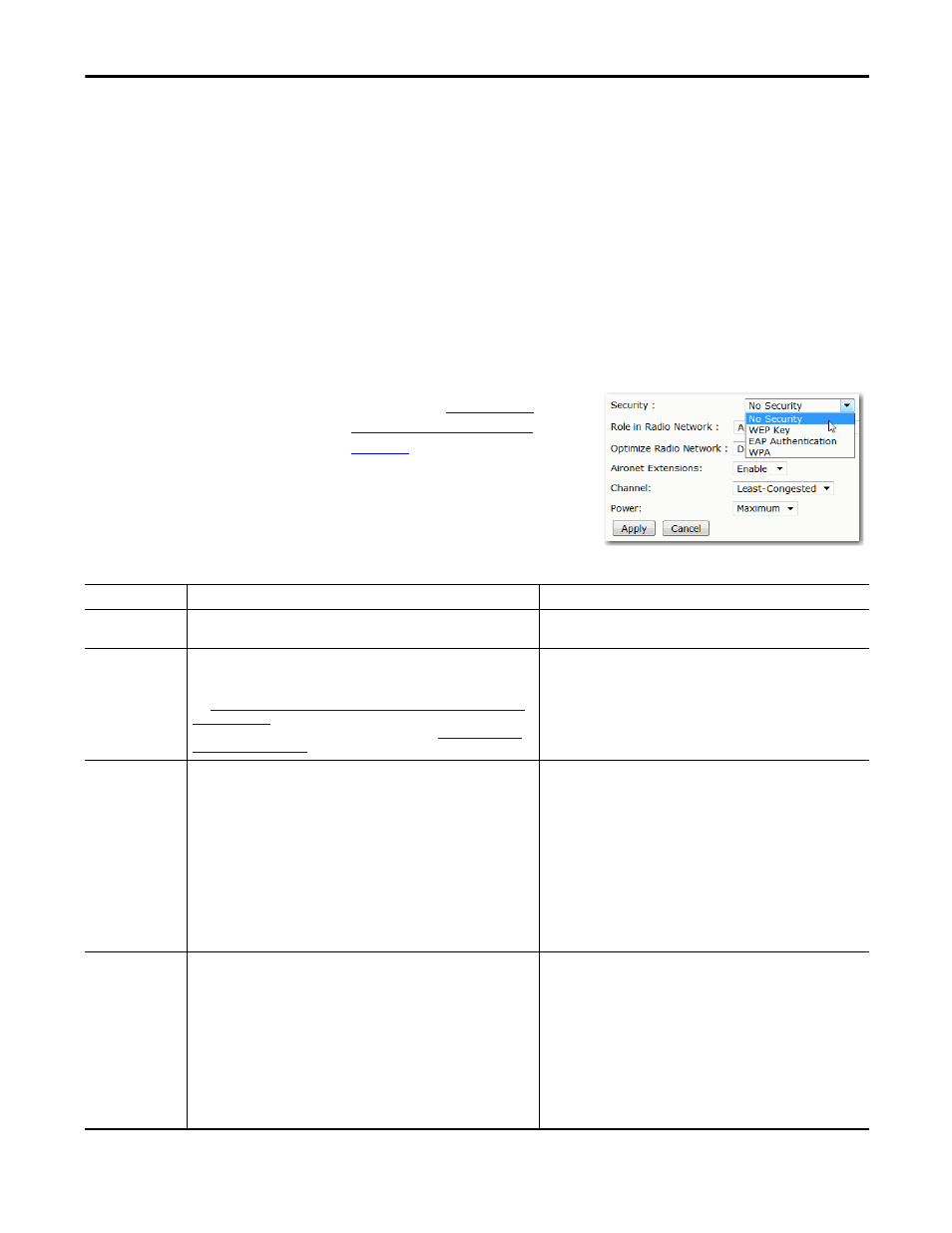
You can configure a limited number of security parameters for the Stratix 5100
WAP. There are four choices:
• No Security
• WEP Key
• EAP Authentication
• WPA
Use the Security page to review and configure the security settings for the access
point.
You can configure security also by
using CLI, see
Configuration Examples on
page 184
.
Table 12 - Security Types on Easy Set-up Security Setup Page
Security Type
Description
Security Features Enabled
No Security
This is the least secure option. Use this option only for SSIDs used in a public
space and assign it to a VLAN that restricts access to your network.
None.
WEP Key
This option is more secure than no security. However, static WEP keys are
vulnerable to attack. If you configure this setting, consider limiting association
to the wireless device based on MAC address
See
Using MAC Address ACLs to Block or Allow Client Association to the Access
or, if your network does not have a RADIUS server, consider
using an access point as a local authentication server, see
Mandatory WEP. Client devices cannot associate by using this SSID without
a WEP key that matches the wireless device key.
EAP Authentication
This option enables 802.1X authentication, for example, LEAP, PEAP, EAP-TLS,
EAP-FAST, EAP-TTLS, EAP-GTC, EAP-SIM, and other 802.1X/EAP based products)
This setting uses mandatory encryption, WEP, open authentication + EAP,
network EAP authentication, no key management, RADIUS server
authentication port 1645.
You are required to enter the IP address and shared secret for an authentication
server on your network (server authentication port 1645). Because 802.1X
authentication provides dynamic encryption keys, you don’t need to enter a
WEP key.
Mandatory 802.1X authentication. Client devices that associate by using
this SSID must perform 802.1X authentication.
If radio clients are configured to authenticate by using EAP-FAST, open
authentication with EAP can also be configured. If you do not configure
open authentication with EAP, the following GUI warning message
appears:
WARNING: Network EAP is used for LEAP authentication only. If radio
clients are configured to authenticate by using EAP-FAST, Open
Authentication with EAP can also be configured.
If you are using CLI, this warning message appears:
SSID CONFIG WARNING: [SSID]: If radio clients are using EAP-FAST, AUTH
OPEN with EAP must be configured.
WPA
Wi-Fi Protected Access (WPA) permits wireless access to users authenticated
against a database through the services of an authentication server, then
encrypts their IP traffic with stronger algorithms than those used in WEP.
This setting uses encryption ciphers, TKIP, open authentication + EAP, network
EAP authentication, key management WPA mandatory, and RADIUS server
authentication port 1645.
As with EAP authentication, you must enter the IP address and shared secret for
an authentication server on your network (server authentication port 1645).
Mandatory WPA authentication. Client devices that associate by using this
SSID must be WPA-capable.
If radio clients are configured to authenticate by using EAP-FAST, open
authentication with EAP must be configured. If you don’t configure open
authentication with EAP, the following GUI warning message appears:
WARNING: Network EAP is used only for LEAP authentication. If radio
clients are configured to authenticate by using EAP-FAST, Open
Authentication with EAP must be configured.
If you are using CLI, this warning message appears:
SSID CONFIG WARNING: [SSID]: If radio clients are using EAP-FAST, AUTH
OPEN with EAP must be configured.
