Rm protection, Rm protection 80 – HP XP Continuous Access Software User Manual
Page 79
Using RAID Manager
79
RM protection
The RAID Manager protection facility restricts RM volume control
operations to volumes that:
• the host is allowed to see, with or without host-based LUN security
(Secure LUN XP)
• are listed in the RM configuration file.
To avoid inconsistency, RM security cannot be controlled within RM itself.
RM security is determined by command device definition within the SVP,
Remote Console, or via SNMP. Upon definition, the protection facility for
each command device can be enabled by setting an attribute. RM refers to
this attribute when it first recognizes the command device.
Command devices with protection ON permit access to volumes that are
not only on their list of allowed volumes, but are also host viewable.
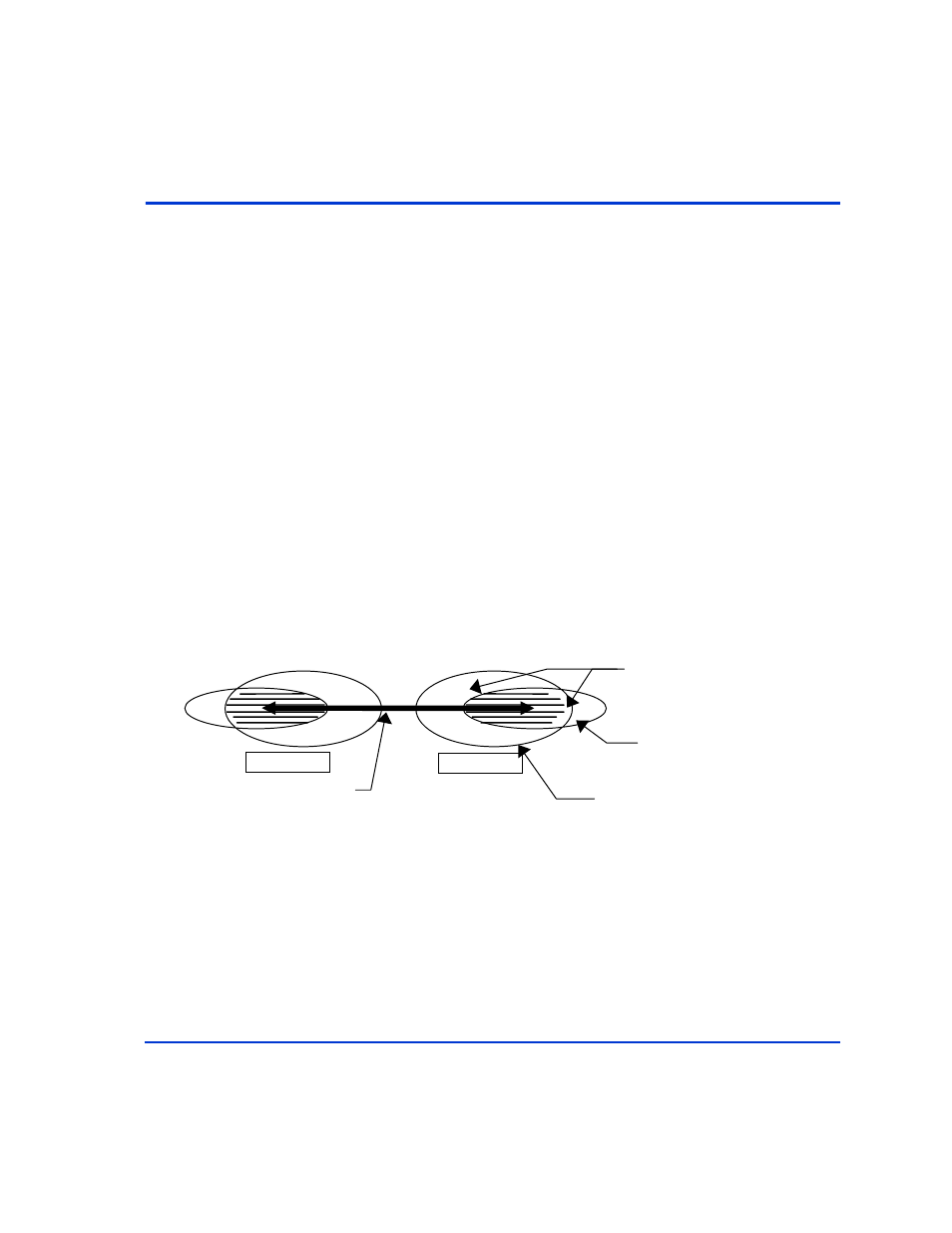
The following figure shows the definition of a protected (access refused)
volume:
Permitted volumes
Volumes within Host view via
LUN Security
Volumes in the horcm.conf file viewable via
protection ON command device
Protected (refused) volumes
HOST1
HOST2
