General security guidelines in ito, Restrictions, Table 10-7 restrictions in a c2-secure environment – HP UX B6941-90001 User Manual
Page 436
436
Chapter 10
Tuning, Troubleshooting, Security, and Maintenance
ITO Security
General Security Guidelines in ITO
A C2-secure or “trusted” system uses a number of techniques to improve
security at system level. These techniques would include, amongst other
things, the following:
❏ Imposing strict password and user authentication methods for the
UNIX login
❏ Auditing networking, shared memory, file systems and so on
❏ Controlling access to terminals
❏ Managing access to files
For information about the implications these security recommendations
can have with regard to the configuration of ITO, see “Restrictions” on
page 436.
Restrictions
Running ITO in a C2-secure environment imposes a number of
important restrictions on the ITO configuration. Table 10-7 on page 436
lists those areas and provides a brief explanation of the cause of the
restriction. It is the administrator’s decision as to where security
priorities lie.
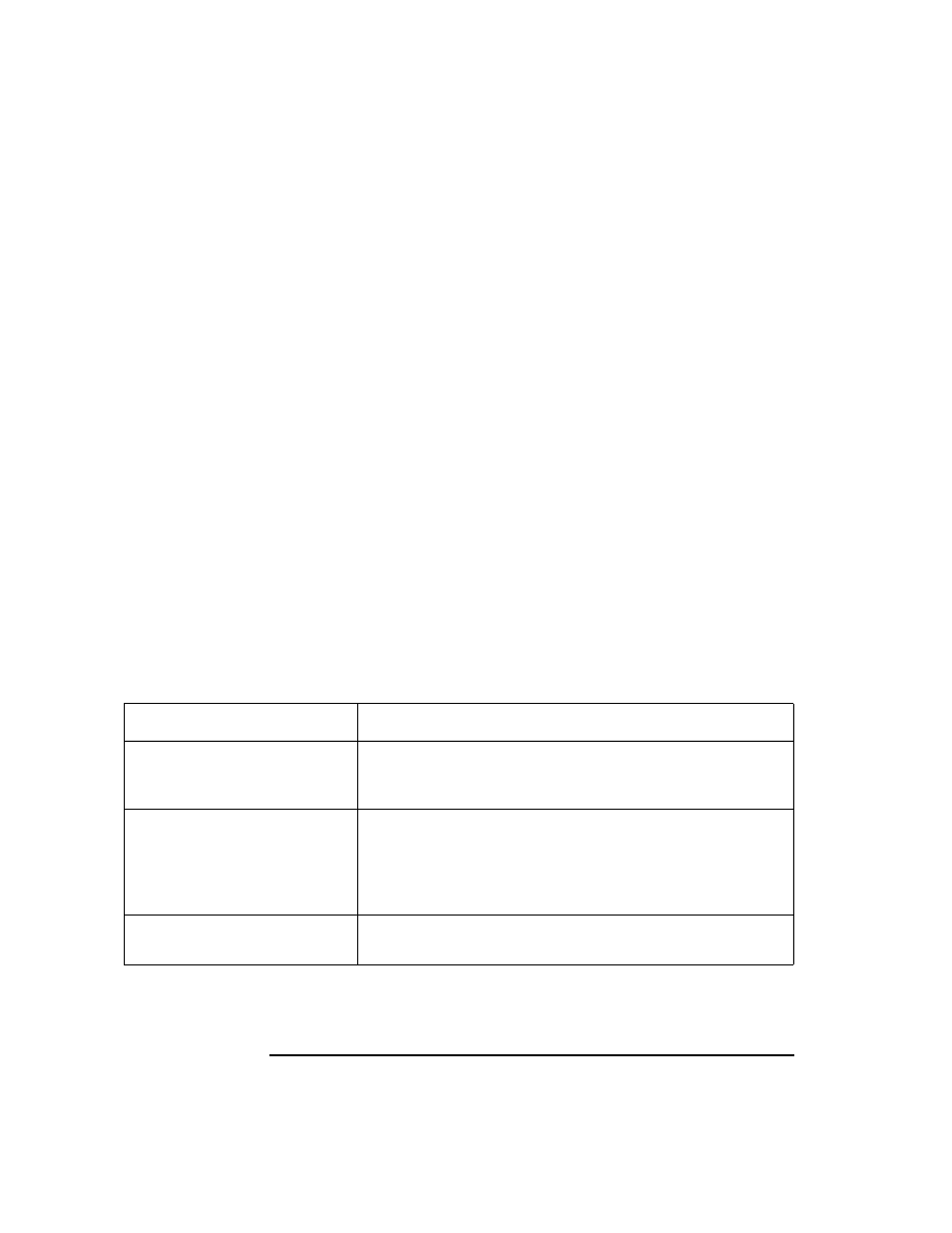
Table 10-7
Restrictions in a C2-secure Environment
Restricted Area
Explanation
ACLs
Although C2 recommends the use of ACLs, the OpenView
file tree does not support them. In addition,
opc_backup
and
opc_restore
are not aware of ACLs.
Agent Installation
If root-login over the network is not allowed, the ITO
agent has to be installed manually. For more information
about installing the agent manually, see the HP OpenView
IT/Operations Installation Guide for the Management
Server
Application Passwords
Password aging and changing can lead to problems with
remote application startup.
