2 the rip screen, Figure 199 network > routing > rip, Table 94 network > routing protocol > rip – ZyXEL Communications 200 Series User Manual
Page 288
Chapter 13 Routing Protocols
ZyWALL USG 100/200 Series User’s Guide
288
13.2 The RIP Screen
RIP (Routing Information Protocol, RFC 1058 and RFC 1389) allows a device to exchange
routing information with other routers. RIP is a vector-space routing protocol, and, like most
such protocols, it uses hop count to decide which route is the shortest. Unfortunately, it also
broadcasts its routes asynchronously to the network and converges slowly. Therefore, RIP is
more suitable for small networks (up to 15 routers).
• In the ZyWALL, you can configure two sets of RIP settings before you can use it in an
interface.
• First, the Authentication field specifies how to verify that the routing information that is
received is the same routing information that is sent. This is discussed in more detail in
Authentication Types on page 295
• Second, the ZyWALL can also redistribute routing information from non-RIP networks,
specifically OSPF networks and static routes, to the RIP network. Costs might be
calculated differently, however, so you use the Metric field to specify the cost in RIP
terms.
• RIP uses UDP port 520.
Use the RIP screen to specify the authentication method and maintain the policies for
redistribution.
To access this screen, login to the web configurator. When the main screen appears, click
Network > Routing > RIP to open the following screen.
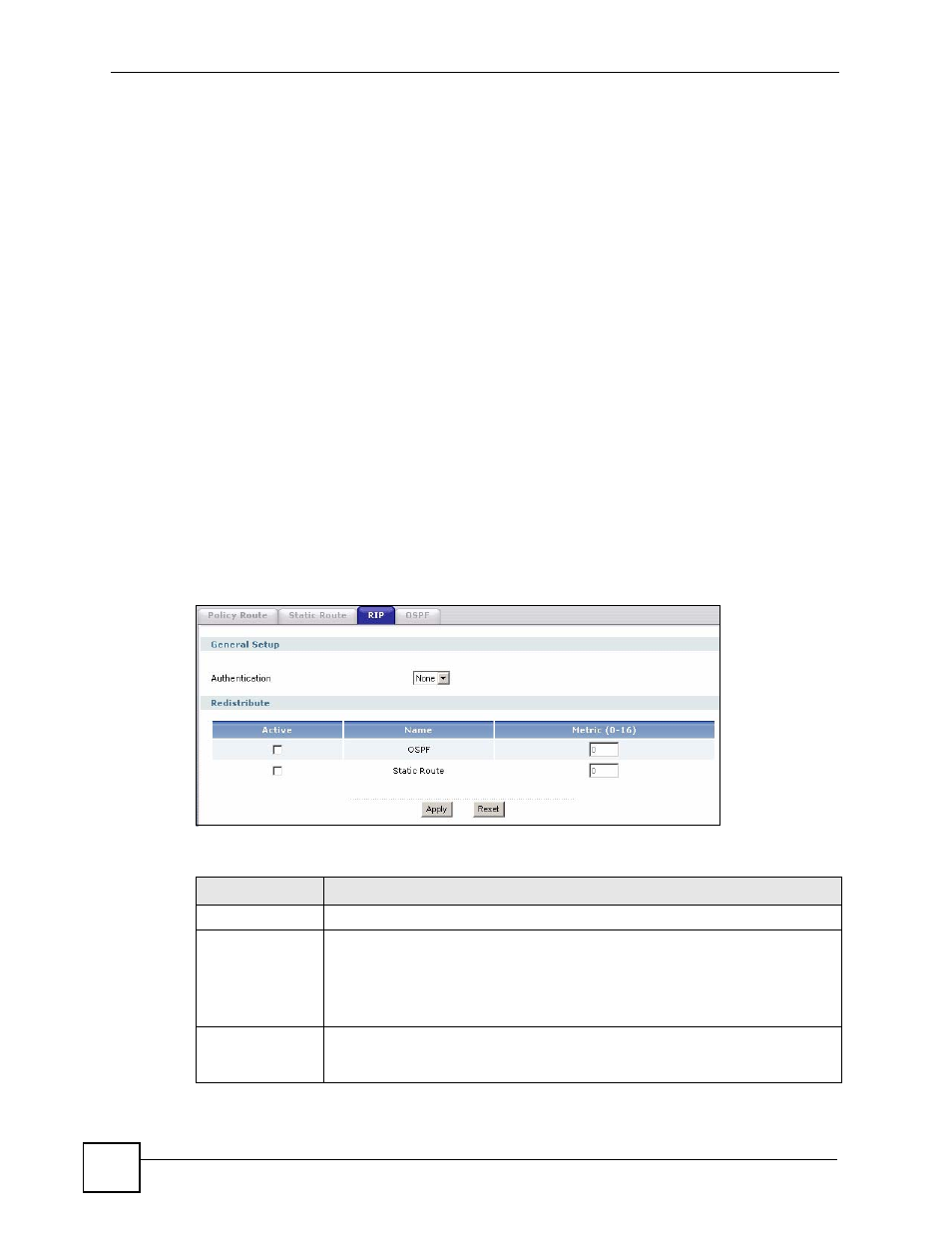
Figure 199 Network > Routing > RIP
The following table describes the labels in this screen.
Table 94 Network > Routing Protocol > RIP
LABEL
DESCRIPTION
Authentication
Authentication
Select the authentication method used in the RIP network. This authentication
protects the integrity, but not the confidentiality, of routing updates.
None uses no authentication.
Text uses a plain text password that is sent over the network (not very secure).
MD5 uses an MD5 password and authentication ID (most secure).
Text
Authentication
Key
This field is available if the Authentication is Text. Type the password for text
authentication. The key can consist of alphanumeric characters and the
underscore, and it can be up to 8 characters long.
