Ipsec protocols (esp/ah), The ah protocol – Amer Networks E5Web GUI User Manual
Page 589
case when using pre-shared keys and roaming clients. Instead, should a client be compromised,
the client's certificate can simply be revoked. No need to reconfigure every client.
Disadvantages of Certificates
The principal disadvantage of certificates is the added complexity. Certificate-based
authentication may be used as part of a larger public key infrastructure, making all VPN clients
and gateways dependent on third parties. In other words, there are more aspects that have to be
configured, and there is more that can go wrong.
9.3.4. IPsec Protocols (ESP/AH)
The IPsec protocols are the protocols used to protect the actual traffic being passed through the
VPN. The actual protocols used and the keys used with those protocols are negotiated by IKE.
There are two protocols associated with IPsec, AH and ESP. These are covered in the sections
below.
AH (Authentication Header)
AH is a protocol used for authenticating a data stream.
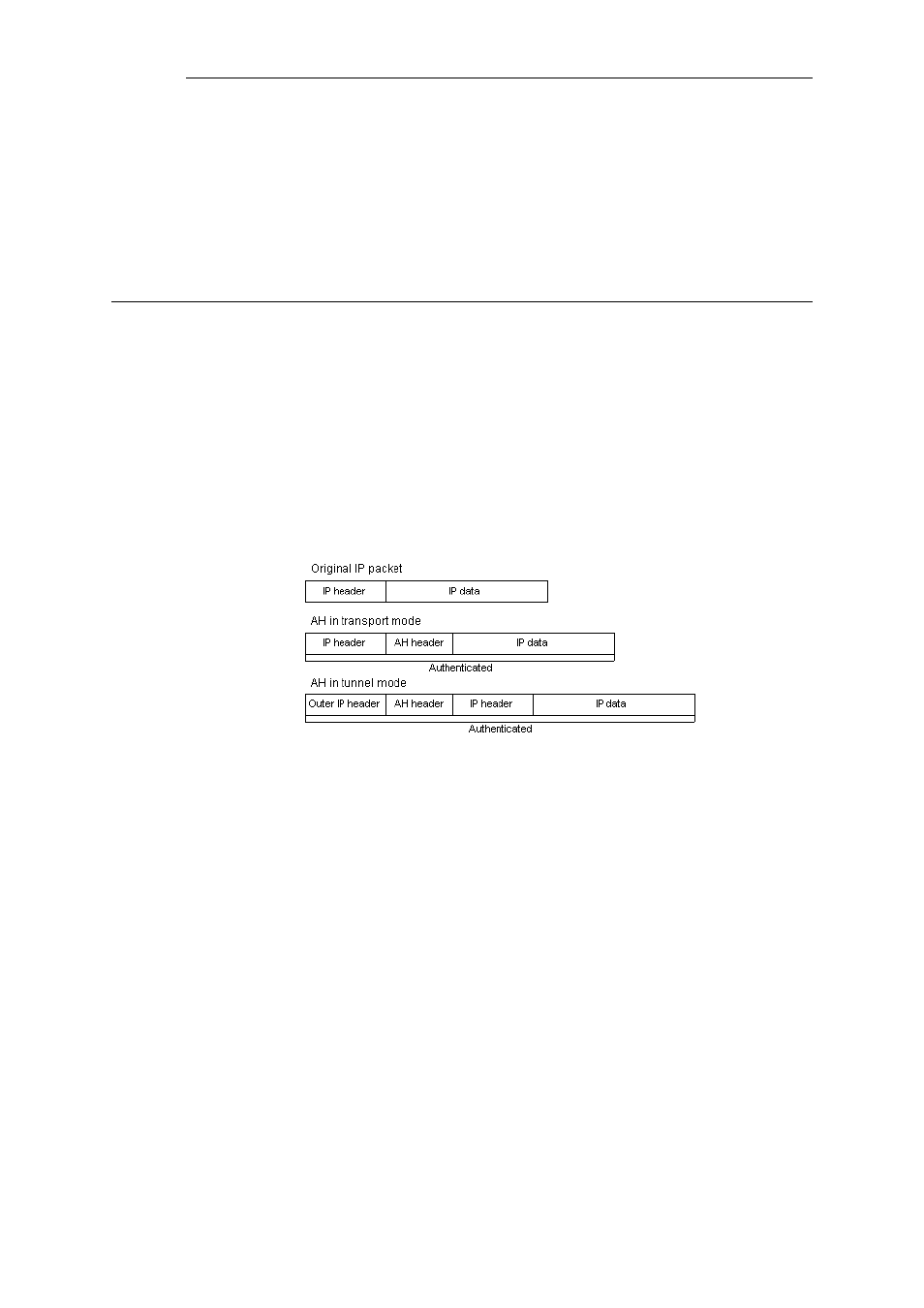
Figure 9.1. The AH protocol
AH uses a cryptographic hash function to produce a MAC from the data in the IP packet. This
MAC is then transmitted with the packet, allowing the remote endpoint to verify the integrity of
the original IP packet, making sure the data has not been tampered with on its way through the
Internet. Apart from the IP packet data, AH also authenticates parts of the IP header.
The AH protocol inserts an AH header after the original IP header. In tunnel mode, the AH header
is inserted after the outer header, but before the original, inner IP header.
ESP (Encapsulating Security Payload)
The ESP protocol inserts an ESP header after the original IP header, in tunnel mode, the ESP
header is inserted after the outer header, but before the original, inner IP header.
All data after the ESP header is encrypted and/or authenticated. The difference from AH is that
ESP also provides encryption of the IP packet. The authentication phase also differs in that ESP
only authenticates the data after the ESP header; thus the outer IP header is left unprotected.
The ESP protocol is used for both encryption and authentication of the IP packet. It can also be
used to do either encryption only, or authentication only.
Chapter 9: VPN
589
