Pptp alg usage – Amer Networks E5Web GUI User Manual
Page 409
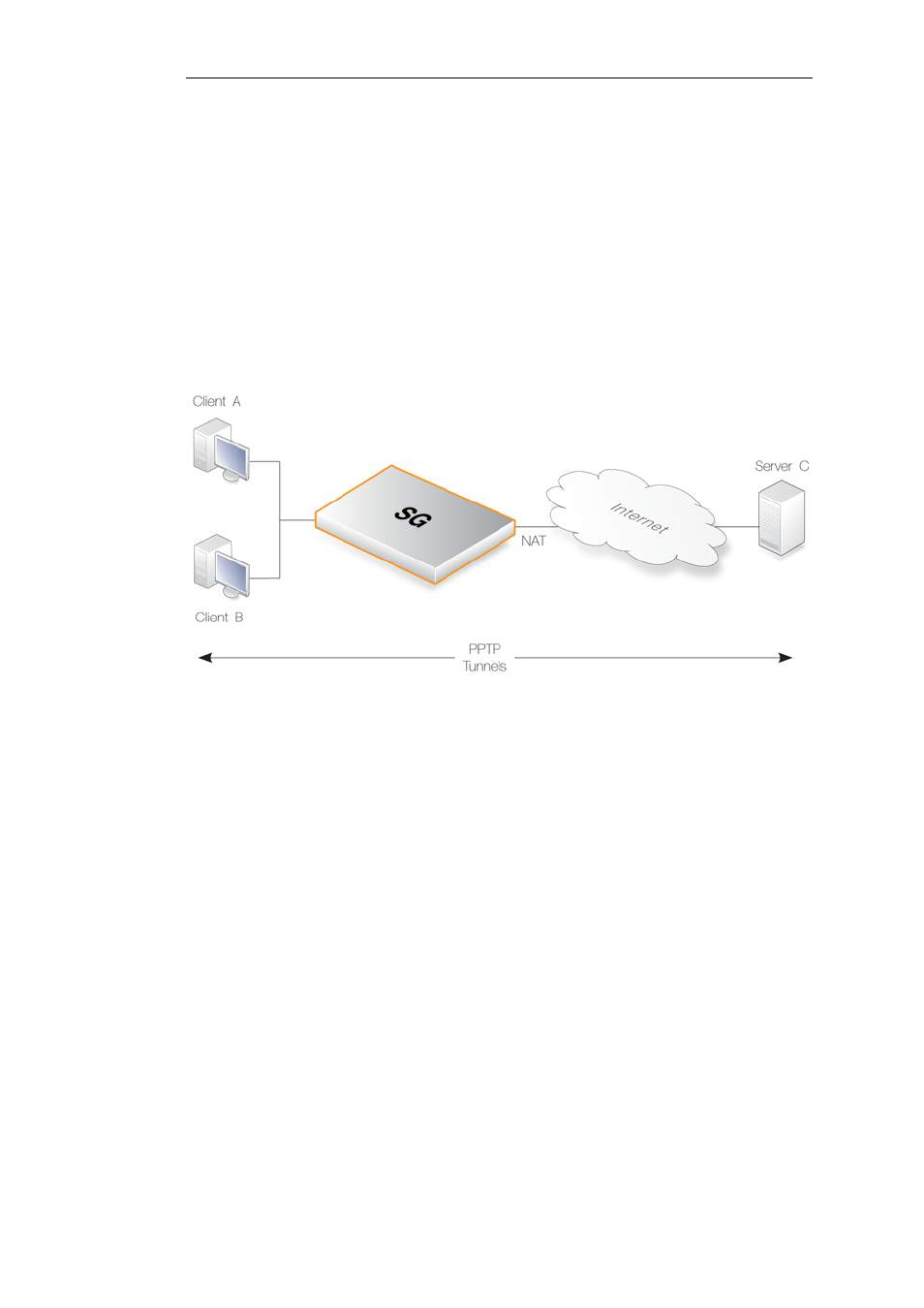
The PPTP ALG is provided to deal with a specific issue when PPTP tunnels are used with NAT.
Let us suppose we have two clients A and B on a protected inner network behind a Clavister
Security Gateway. The security gateway is connected to the external Internet and a NAT rule is
defined to allow traffic from the clients to flow to the Internet. Both clients will therefore appear
to have from the same IP address as they make connections to servers across the Internet.
One client A now establishes a PPTP tunnel to an external host C across the Internet. The tunnel
endpoints are the client and the external server. Because of the NAT IP rule, the tunnel
connection will appear to be coming from the external IP address on the security gateway.
This first connection will be successful but when the second client B also tries to connect to the
same server C at the same endpoint IP address, the first connection for A will be lost. The reason
is that both clients are trying to establish a PPTP tunnel from the same external IP address to the
same endpoint.
Figure 6.6. PPTP ALG Usage
The PPTP ALG solves this problem. By using the ALG, the traffic from all the clients can be
multiplexed through a single PPTP tunnel between the security gateway and the server.
PPTP ALG Setup
Setting up the PPTP ALG is similar to the set up of other ALG types. The ALG object must be
associated with the relevant service and the service is then associated with an IP rule. The full
sequence of steps for setup is as follows:
•
Define a new PPTP ALG object with an appropriate name, for example pptp_alg. The full list of
options for the ALG are listed towards the end of this section.
•
Associate the new ALG object with an appropriate Service object. The predefined service
called pptp-ctl can be used for this purpose.
Alternatively, a new custom service object can be defined, for example called pptp_service.
The service must have the following characteristics:
i.
Select the Type (the protocol) as TCP.
ii.
The Source port range can be the default of 0-65535.
iii.
Set the Destination port to be 1723.
Chapter 6: Security Mechanisms
409
