Ipsec roaming clients with pre-shared keys – Amer Networks E5Web GUI User Manual
Page 572
Note: The system time and date should be correct
The cOS Core date and time should be set correctly since certificates have an expiry date
and time.
Also review Section 9.7, “CA Server Access” below, which describes important considerations for
certificate validation.
Self-signed certificates instead of CA signed can be used for LAN to LAN tunnels but the Web
Interface and other interfaces do not have a feature to generate them. Instead, they must be
generated by another utility and imported into cOS Core. This means that they are not truly
self-signed since they are generated outside of cOS Core control and it should be remembered
that there is no guarantee that their private key is unique. However, the security provided can
still be considered adequate for some scenarios.
Two self-signed certificates are required and the same two are used at either end of the tunnel
but their usage is reversed. In other words: one certificate is used as the root certificate at one
end, call it Side A, and as the host certificate at the other end, call it Side B. The second certificate
is used in the opposite way: as the host certificate at Side A and the root certificate at Side B.
No CA server considerations are needed with self-signed certificates since CRL lookup does not
occur.
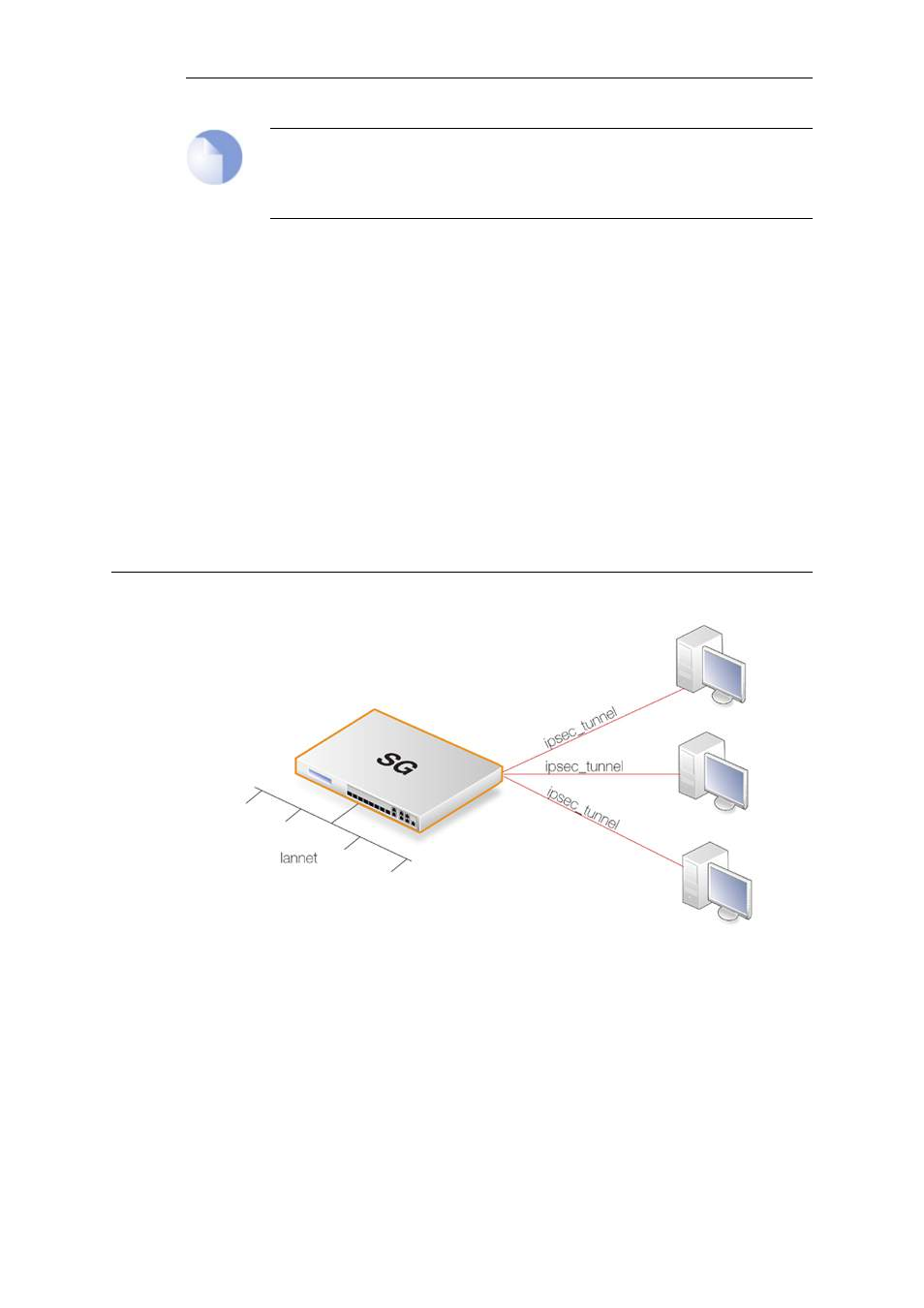
9.2.3. IPsec Roaming Clients with Pre-shared Keys
This section details the setup with roaming clients connecting through an IPsec tunnel using
pre-shared keys to a protected Local Network which is located behind a Clavister Security
Gateway.
There are two types of roaming clients:
A. the IPv4 addresses of the clients are already allocated.
B. the IPv4 addresses of clients are not known beforehand and must be handed out by cOS Core
when the clients try to connect.
Chapter 9: VPN
572
