User authentication setup for web access, Forcing users to a login page – Amer Networks E5Web GUI User Manual
Page 539
HTTP authentication cannot operate unless a rule is added to the IP rule set to explicitly allow
authentication to take place. This is also true with HTTPS.
If we consider the example of a number of clients on the local network lan_net who would like
access to the public Internet through the wan interface then the IP rule set would contain the
following rules:
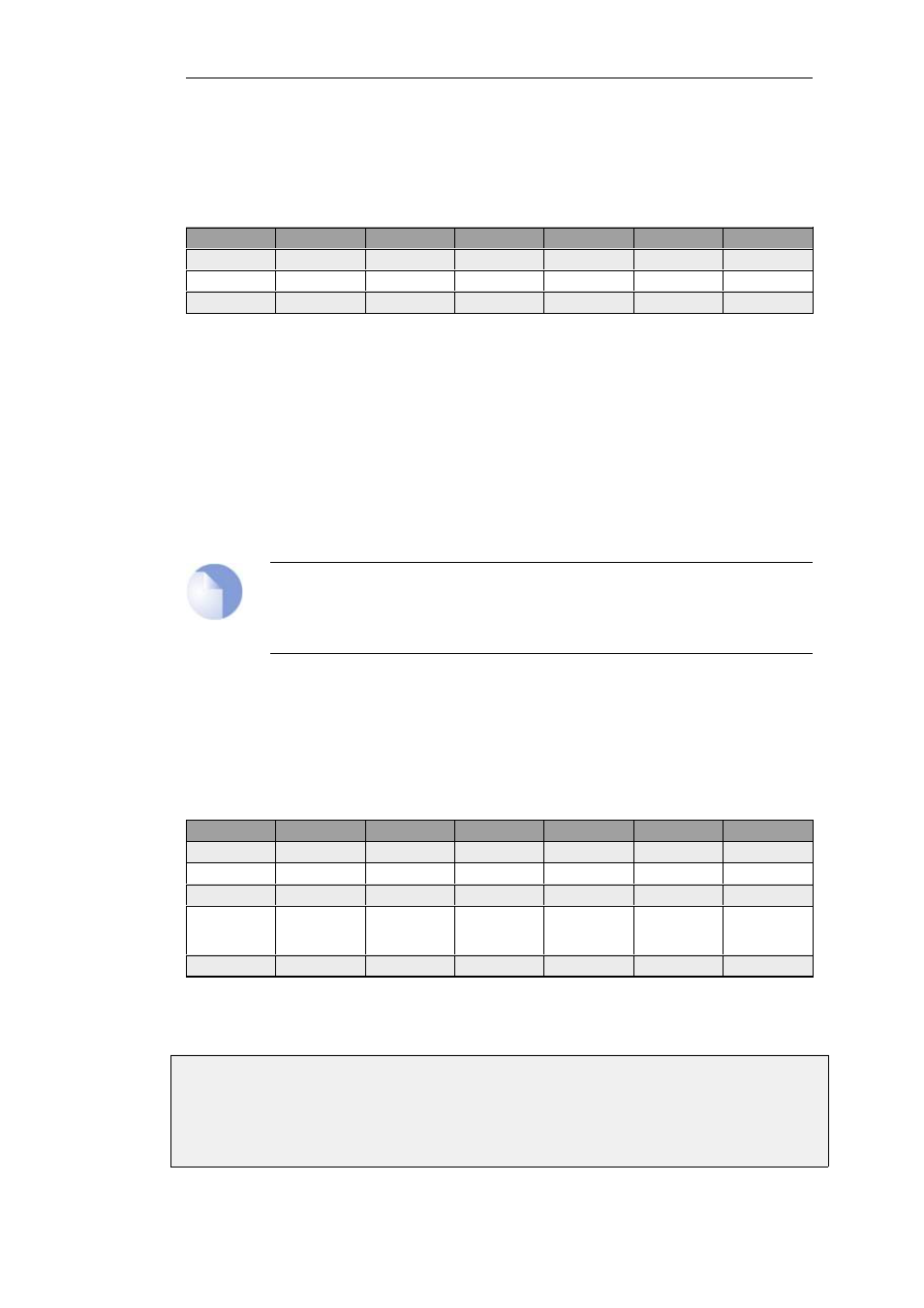
#
Action
Src Interface
Src Network
Dest Interface
Dest Network
Service
1
Allow
lan
lan_net
core
lan_ip
http-all
2
NAT
lan
trusted_users
wan
all-nets
http-all
3
NAT
lan
lan_net
wan
all-nets
dns-all
The first rule allows the authentication process to take place and assumes the client is trying to
access the lan_ip IP address, which is the IP address of the interface on the Clavister Security
Gateway where the local network connects.
The second rule allows normal surfing activity but we cannot just use lan_net as the source
network since the rule would trigger for any unauthenticated client from that network. Instead,
the source network is an administrator defined IP object called trusted_users which is the same
network as lan_net but has additionally either the Authentication option No Defined
Credentials enabled or has an Authentication Group assigned to it (which is the same group as
that assigned to the users).
The third rule allows DNS lookup of URLs.
Note
Do not modify the default http-all service in the IP rules above. This can cause
authentication to fail.
Forcing Users to a Login Page
With this setup, when users that are not authenticated try to surf to any IP except lan_ip they will
fall through the rules and their packets will be dropped. To always have these users come to the
authentication page, a SAT rule and its associated Allow rule must be added. The rule set will now
look like this:
#
Action
Src Interface
Src Network
Dest Interface
Dest Network
Service
1
Allow
lan
lan_net
core
lan_ip
http-all
2
NAT
lan
trusted_users
wan
all-nets
http-all
3
NAT
lan
lan_net
wan
all-nets
dns-all
4
SAT
lan
lan_net
wan
all-nets
all-to-one
127.0.0.1
http-all
5
Allow
lan
lan_net
wan
all-nets
http-all
The SAT rule catches all unauthenticated requests and must be set up with an all-to-one address
mapping that directs them to the address 127.0.0.1 which corresponds to core (cOS Core itself ).
Example 8.3. User Authentication Setup for Web Access
The configurations below shows how to enable HTTP user authentication for the user group
lan_group on lan_net. Only users that belong to the group users can get Web browsing service
Chapter 8: User Authentication
539
