Loop avoidance, A usage example, The main ip rule set – Amer Networks E5Web GUI User Manual
Page 198: The extrarules ip rule set, Increasing ip rule lookup speed
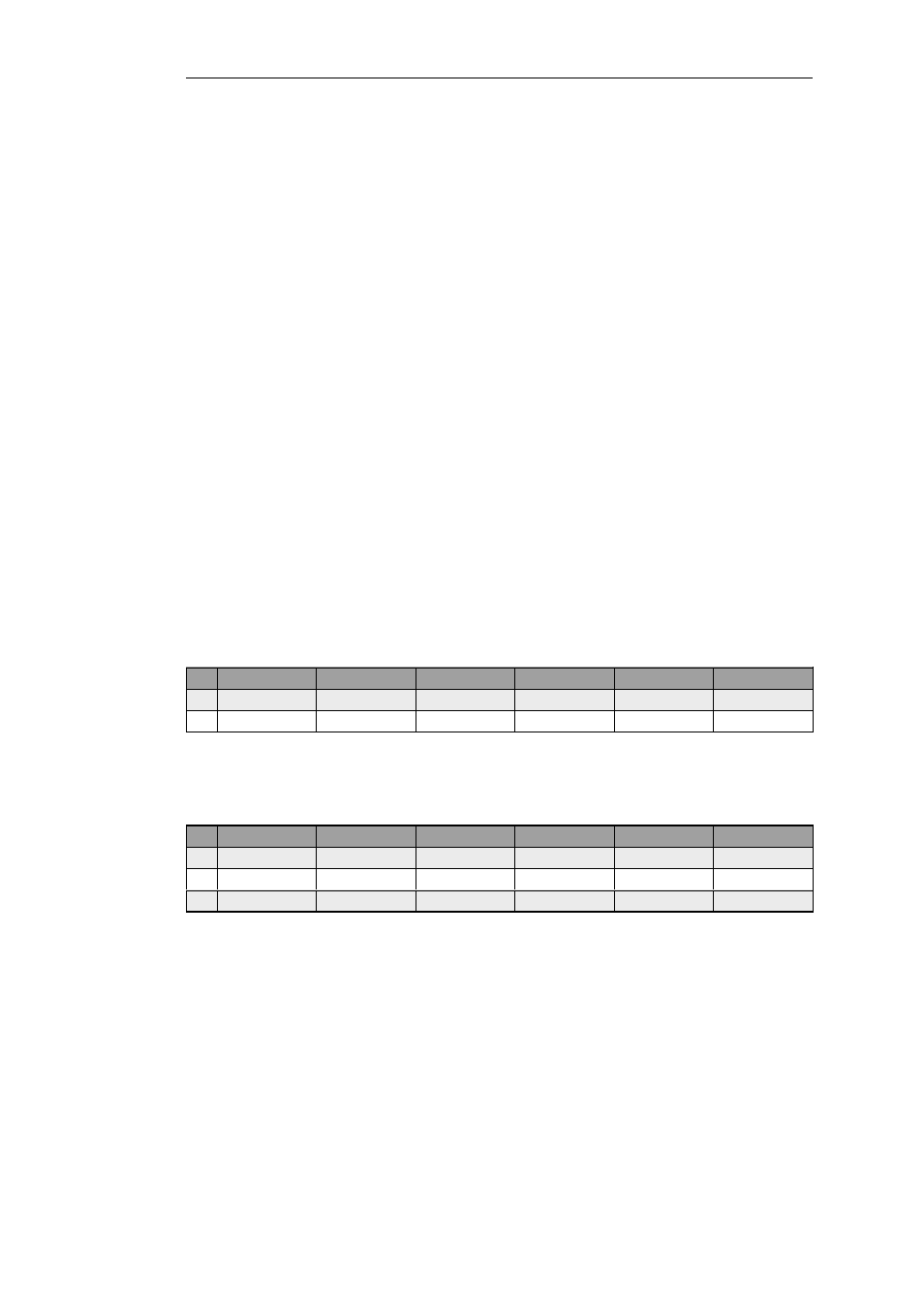
If the action is Return then the rule scanning resumes at the rule which follows the last Goto
action (if there was no last Goto then the connection is dropped and rule scanning stops).
Loop Avoidance
It is conceivable that a sequence of Goto actions results in an infinite looping scanning
sequence. cOS Core detects such logic when a configuration is initially uploaded. A new
configuration is rejected if multiple IP rule set logic is detected that could potentially cause a
loop condition.
The loop avoidance mechanism has to be efficient to enable fast configuration upload and for
this reason it uses an algorithm that might sometimes find a fault in correct but complex logic. In
this case it may be necessary to simplify the rule logic so the configuration can be uploaded.
A Usage Example
Below are two simple IP Rule set tables which illustrate how multiple rule sets might be used. The
main rule set contains a first rule which has a Goto action which references the named
administrator defined table called ExtraRules.
The administrator defined rule set ExtraRules contains a NAT and SAT rule. If neither are triggered
then the final rule has a Return action which will cause the scanning process to go back to the
rule in main which follows the Goto rule. In this case it will be the second rule in main.
The main IP rule set
#
Action
Src Iface
Src Net
Dest Iface
Dest Net
Service
1
Goto ExtraRules
any
all-nets
core
172.16.40.0/24
all_services
2
Allow
any
192.168.0.0/24
core
172.16.0.0/16
all_services
The ExtraRules IP rule set
#
Action
Src Iface
Src Net
Dest Iface
Dest Net
Service
1
SAT
any
all-nets
any
172.16.40.66
all_services
2
NAT
If2
176.16.0.0/16
any
all-nets
all_services
3
RETURN
If2
all-nets
any
all-nets
all_services
Increasing IP Rule Lookup Speed
When the main rule set starts to contain many thousands of rules, the speed of IP rule lookup can
become impaired and this can degrade the overall throughput of the security gateway. Typical
symptoms of this can be:
•
Consistently high CPU loads in the security gateway.
•
Unusually long loading times for Web Interface pages (which is a result of high CPU loads).
The solution is to break the large table up and place the rules into several new rule sets, each
containing the rules related to a generalized aspect of traffic throughput. A small number of IP
Chapter 3: Fundamentals
198
