Transparent mode scenario 2 – Amer Networks E5Web GUI User Manual
Page 349
•
Name: http_allow
•
Action: Allow
•
Service: http
•
Source Interface: lan
•
Destination Interface: any
•
Source Network: 10.0.0.0/24
•
Destination Network: all-nets
3.
Click OK
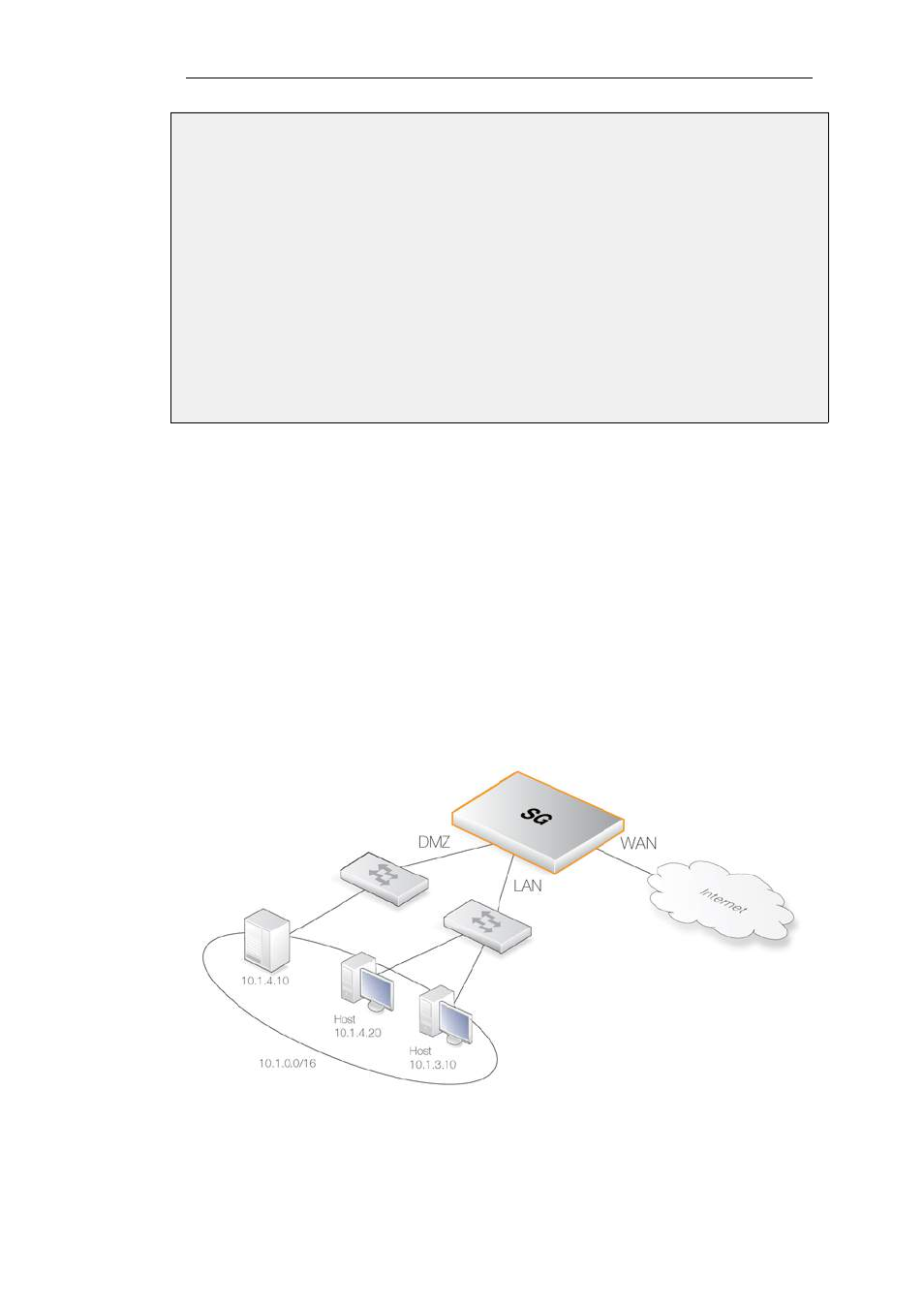
Scenario 2
In the second scenario, the Clavister Security Gateway in transparent mode separates server
resources in the DMZ from an internal local network. Each is connected to a separate interface
without the need for different address ranges.
All hosts connected to lan and dmz interfaces share the 10.0.0.0/24 address space. As this is
configured using transparent mode, any IP address can be used for the servers and there is no
need for the hosts on the internal network to know if a resource is on the same network or
placed in the DMZ.
The clients on the internal network are allowed to communicate with an HTTP server on the DMZ
network. At the same time, the DMZ HTTP server is reachable from the public Internet. The
Clavister Security Gateway is transparent between the dmz and lan interfaces but traffic is still
controlled by IP rules.
Figure 4.27. Transparent Mode Scenario 2
Chapter 4: Routing
349
