The importance of sat rule ordering – Amer Networks E5Web GUI User Manual
Page 507
interface of the SAT rule must be set to any. The correct second rule for the external or internal
traffic is then selected based on the source interface. In this example, the internal clients are
allowed any type of access to the DMZ, not just HTTP access.
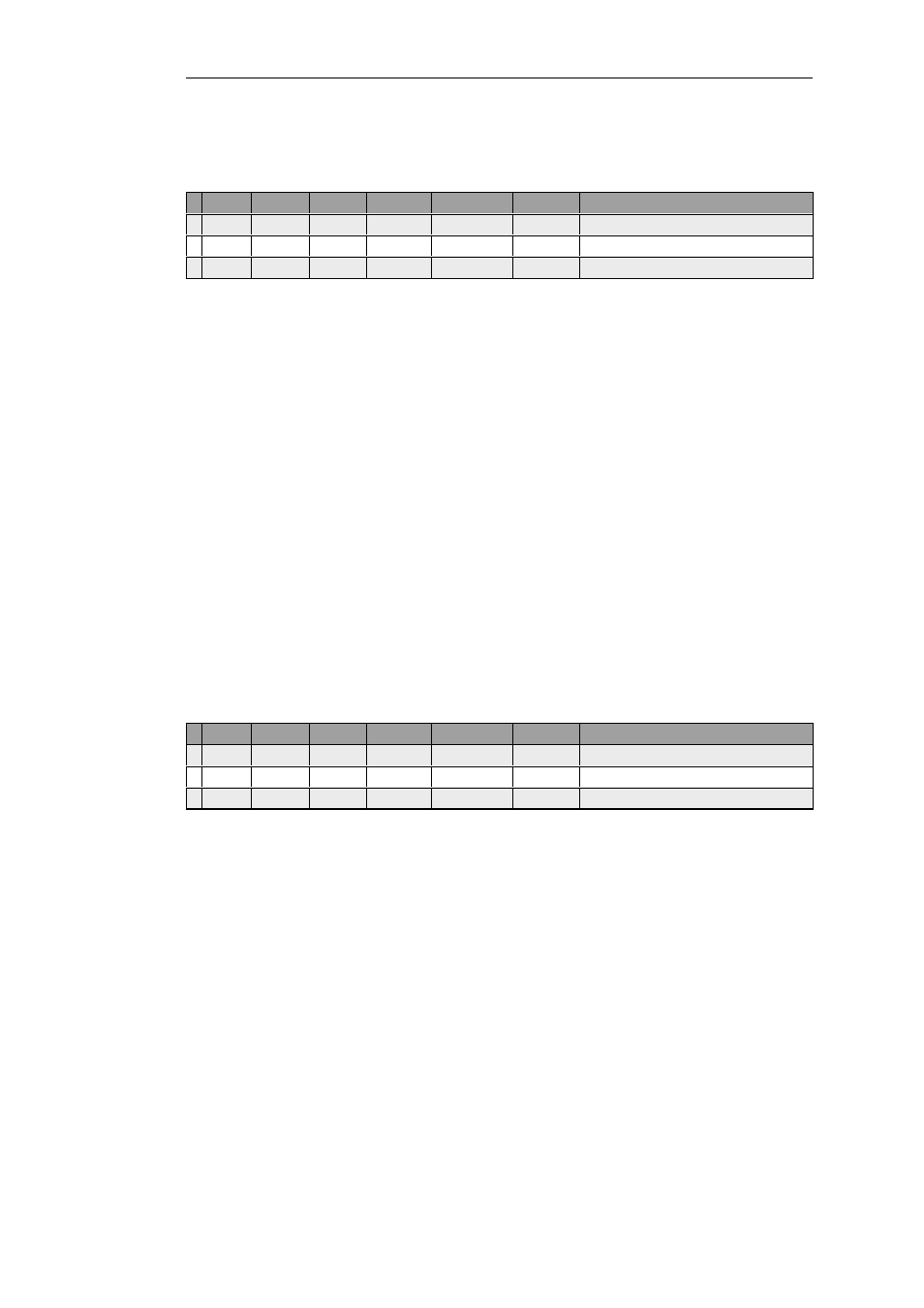
# Action
Src Iface
Src Net
Dest Iface Dest Net
Service
SAT Action
1 SAT
any
all-nets
core
wan_ip
all_services Destination IP: 10.10.10.5
2 Allow
wan
all-nets
core
wan_ip
http
3 NAT
lan
lan_net
any
all-nets
all_services
Here, only one SAT rule is needed and once it triggers it will be used with whichever rule is
triggered next. The ordering of the Allow and NAT rules don't matter but they must be found
after the SAT rule.
The Importance of SAT Rule Ordering
To demonstrate how IP rules are processed for SAT, consider another simple case of a web server
with a private IPv4 address located on an internal network that will be accessed by both external
and internal users.
Assume the following IPv4 addresses:
•
wan_ip (195.55.66.77): the security gateway's public IPv4 address
•
lan_ip (10.0.0.1): the local network's private IPv4 address
•
wwwsrv_ip (10.0.0.2): the web server's private IPv4 address
•
client_ip (10.0.0.3): the local client's private IPv4 address
The IP rules that are needed for external and internal access to the web server could be specified
as follows:
# Action
Src Iface
Src Net
Dest Iface Dest Net
Service
SAT Action
1 SAT
any
all-nets
core
wan_ip
all_services Destination IP: wwwsrv_ip Port: 80
2 Allow
any
all-nets
core
wan_ip
http
3 NAT
lan
lan_net
core
wan_ip
all_services
With the above rules, the following will happen to traffic:
•
The local client sends a packet to wan_ip to reach the web server.
10.0.0.3:1038 => 195.55.66.77:80
•
cOS Core translates the address in accordance with SAT rule 1 and forwards the packet in
accordance with Allow rule 2:
10.0.0.3:1038 => 10.0.0.2:80
•
The server at wwwsrv_ip processes the packet and replies:
10.0.0.2:80 => 10.0.0.3:1038
This reply arrives directly to the local client without passing through the Clavister Security
Gateway and this causes problems because the client expects a reply from 195.55.66.77:80 and
not 10.0.0.2:80. The unexpected reply is therefore discarded and the client continues to wait for a
response from 195.55.66.77:80 which will never arrive.
Chapter 7: Address Translation
507
