Amer Networks E5Web GUI User Manual
Page 420
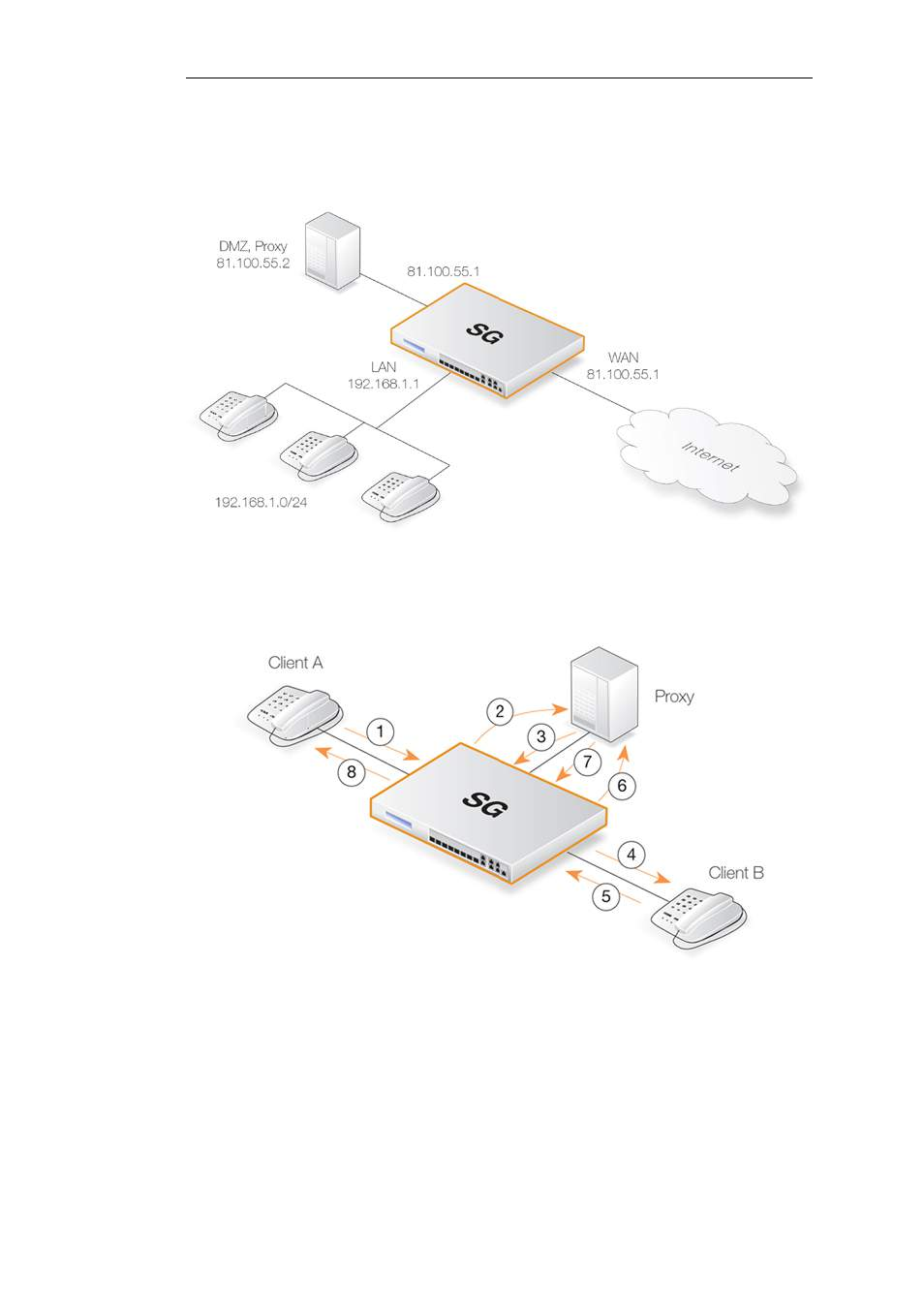
This scenario is similar to the previous but the major difference is the location of the local SIP
proxy server. The server is placed on a separate interface and network to the local clients. This
setup adds an extra layer of security since the initial SIP traffic is never exchanged directly
between a remote endpoint and the local, protected clients.
The complexity is increased in this scenario since SIP messages flow across three interfaces: the
receiving interface from the call initiator, the DMZ interface towards the proxy and the
destination interface towards the call terminator. This the initial messages exchanges that take
place when a call is setup in this scenario are illustrated below:
The exchanges illustrated are as follows:
•
1,2 - An initial INVITE is sent to the outbound local proxy server on the DMZ.
•
3,4 - The proxy server sends the SIP messages towards the destination on the Internet.
•
5,6 - A remote client or proxy server replies to the local proxy server.
•
7,8 - The local proxy forwards the reply to the local client.
This scenario can be implemented in a topology hiding setup with DMZ (Solution A below) as
Chapter 6: Security Mechanisms
420
