Verifying the configuration, Configuration guidelines – H3C Technologies H3C WA3600 Series Access Points User Manual
Page 402
389
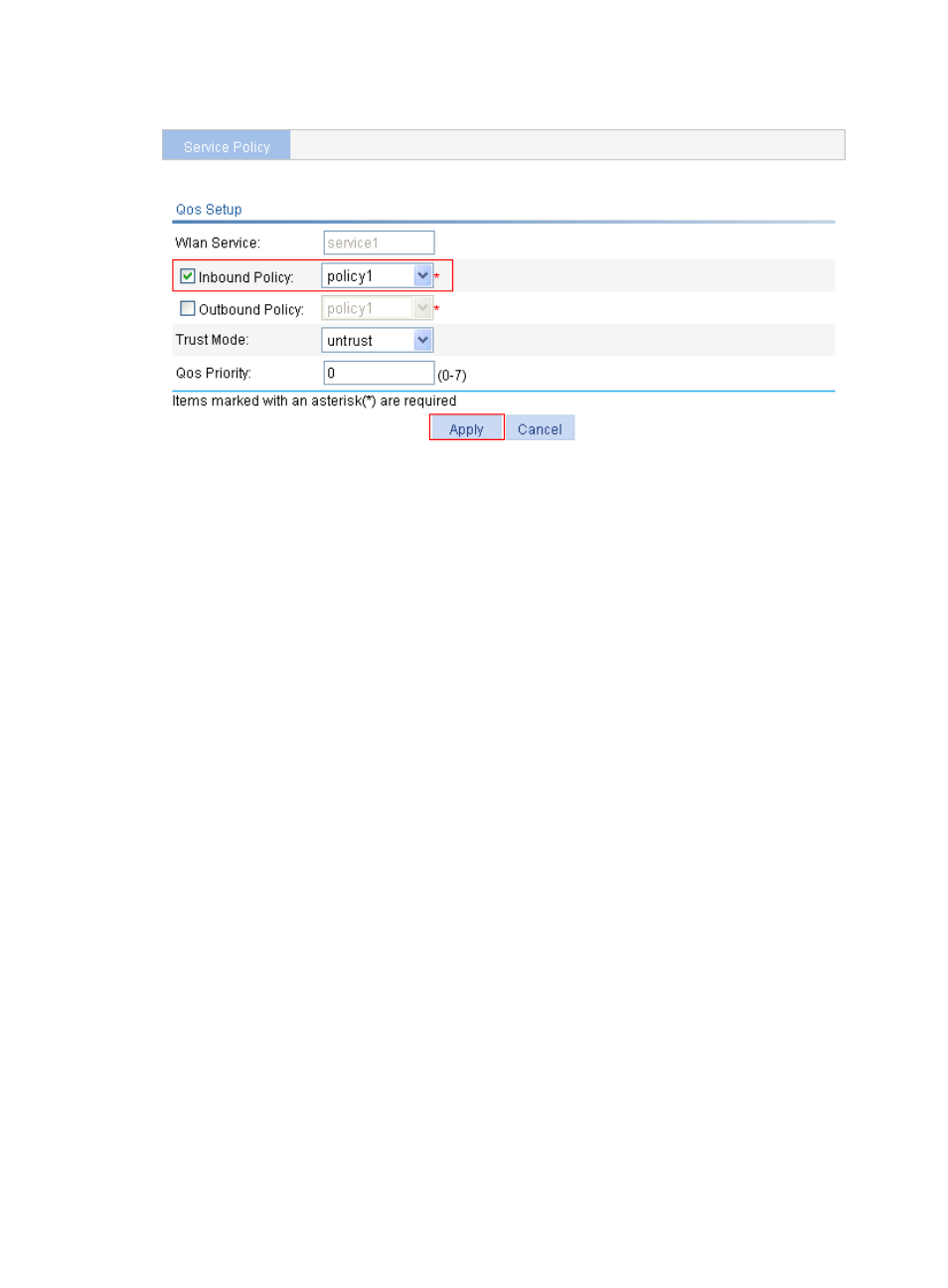
Figure 414 Applying the QoS policy in the inbound direction of wireless service service1
Verifying the configuration
After you complete these configurations, the QoS policy is applied to wireless service service1, and the
wireless clients cannot access the FTP server at IP address 10.1.1.1 from 8:00 to 18:00 every day, but they
can do that at any other time.
Configuration guidelines
When you configure ACL and QoS, follow these guidelines:
•
You cannot add a rule with, or modify a rule to have, the same permit/deny statement as an
existing rule in the ACL.
•
You can only modify the existing rules of an ACL that uses the match order of config. When
modifying a rule of such an ACL, you may choose to change just some of the settings, in which case
the other settings remain the same.
•
When you configure line rate and traffic policing for a behavior, make sure that the ratio of CBS to
CIR is more than 100:16. Otherwise, the handling for bursty traffic may be affected.
•
If an ACL is referenced by a QoS policy for defining traffic classification rules, the operation of the
QoS policy varies by interface: The definition of software/hardware interface varies with device
models. The specific process is as follows:
If the QoS policy is applied to a software interface and the referenced ACL rule is a deny clause,
the ACL rule does not take effect and packets go to the next classification rule.
If the QoS policy is applied to a hardware interface, packets matching the referenced ACL rule
are organized as a class and the behavior defined in the QoS policy applies to the class
regardless of whether the referenced ACL rule is a deny or permit clause.
•
If a QoS policy is applied in the outbound direction of a port, the QoS policy cannot influence local
packets. Local packets refer to the important protocol packets that maintain the normal operation of
the device. QoS must not process such packets to avoid packet drop. Commonly used local packets
are: link maintenance packets, ISIS packets, OSPF packets, RIP packets, BGP packets, LDP packets,
RSVP packets, and SSH packets and so on.
