Authentication – H3C Technologies H3C WA3600 Series Access Points User Manual
Page 270
257
A client sends a probe request (with a specified SSID): When the wireless client is configured to access
a specific wireless network or has already successfully accessed a wireless network, the client
periodically sends a probe request carrying the specified SSID of the configured or connected wireless
network. When an AP that can provide the wireless service with the specified SSID receives the probe
request, it sends a probe response. This active scanning mode enables a client to access a specified
wireless network. The active scanning process is as shown in
.
Figure 256 Active scanning (the probe request carries the specified SSID AP 1)
2.
Passive scanning
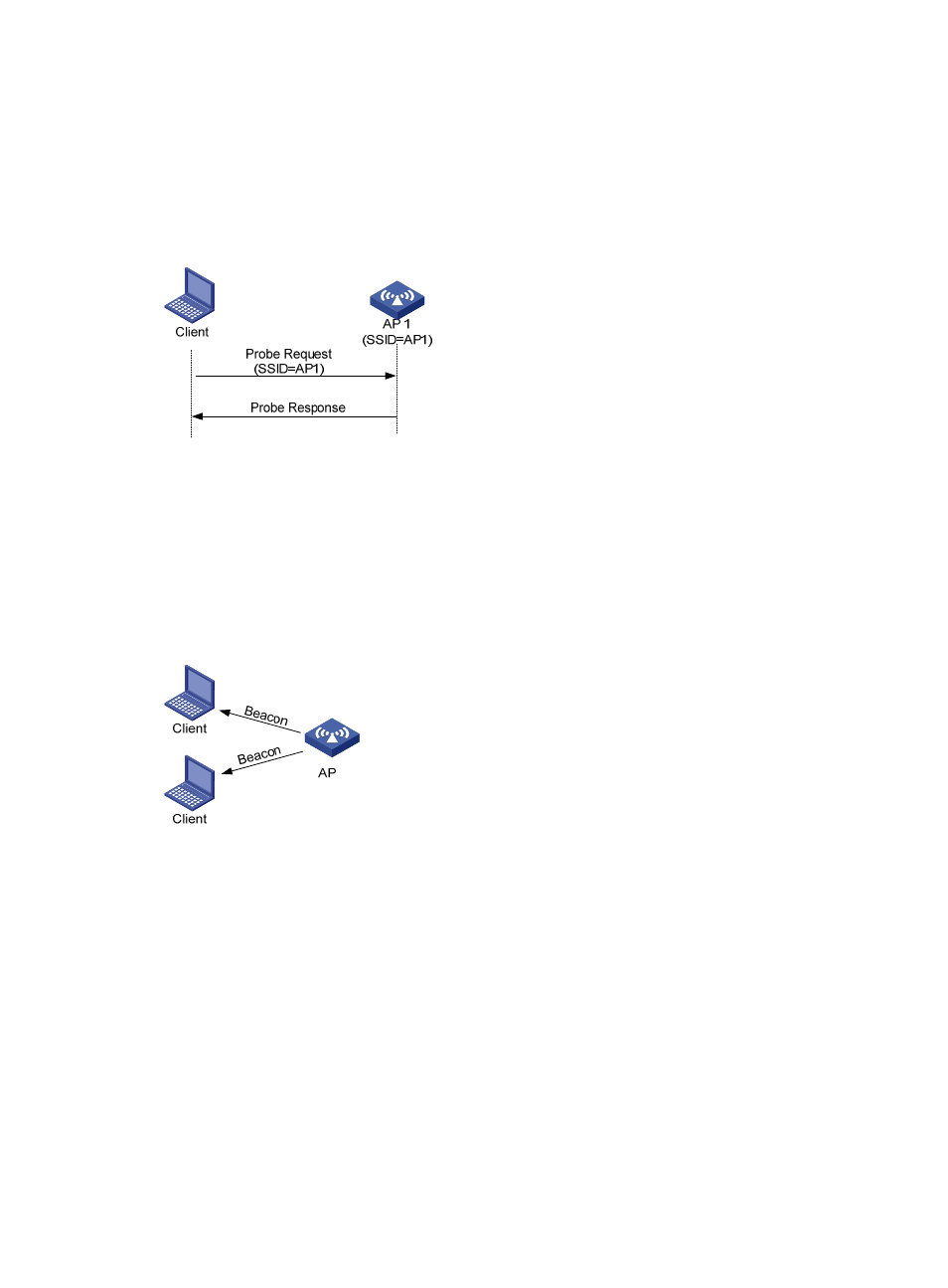
Passive scanning is used by clients to discover surrounding wireless networks through listening to the
beacon frames periodically sent by an AP. All APs providing wireless services periodically send beacon
frames, so that wireless clients can periodically listen to beacon frames on the supported channels to get
information about surrounding wireless networks. Passive scanning is used by a client when it wants to
save battery power. Typically, VoIP clients adopt the passive scanning mode. The passive scanning
process is as shown in
Figure 257 Passive scanning
Authentication
To secure wireless links, the wireless clients must be authenticated before accessing the AP, and only
wireless clients passing the authentication can be associated with the AP. 802.11 links define two
authentication mechanisms: open system authentication and shared key authentication.
•
Open system authentication
Open system authentication is the default authentication algorithm. This is the simplest of the available
authentication algorithms. Essentially it is a null authentication algorithm. Any client that requests
authentication with this algorithm can become authenticated. Open system authentication is not required
to be successful as an AP may decline to authenticate the client. Open system authentication involves a
two-step authentication process. In the first step, the wireless client sends a request for authentication. In
the second step, the AP returns the result to the client.
