H3C Technologies H3C WA3600 Series Access Points User Manual
Page 294
281
Item Description
Port Security
See
.
Parameters such as authentication type and encryption type determine the port
mode. For more information, see
After you select the Cipher Suite option, the following four port security modes
are added:
•
mac and psk—MAC-based authentication must be performed on access
users first. If MAC-based authentication succeeds, an access user has to use
the pre-configured PSK to negotiate with the device. Access to the port is
allowed only after the negotiation succeeds.
•
psk—An access user must use the pre-shared key (PSK) that is
pre-configured to negotiate with the device. The access to the port is
allowed only after the negotiation succeeds.
•
userlogin-secure-ext—Perform MAC-based 802.1X authentication for
access users. In this mode, the port supports multiple 802.1X users.
a.
Configure mac and psk
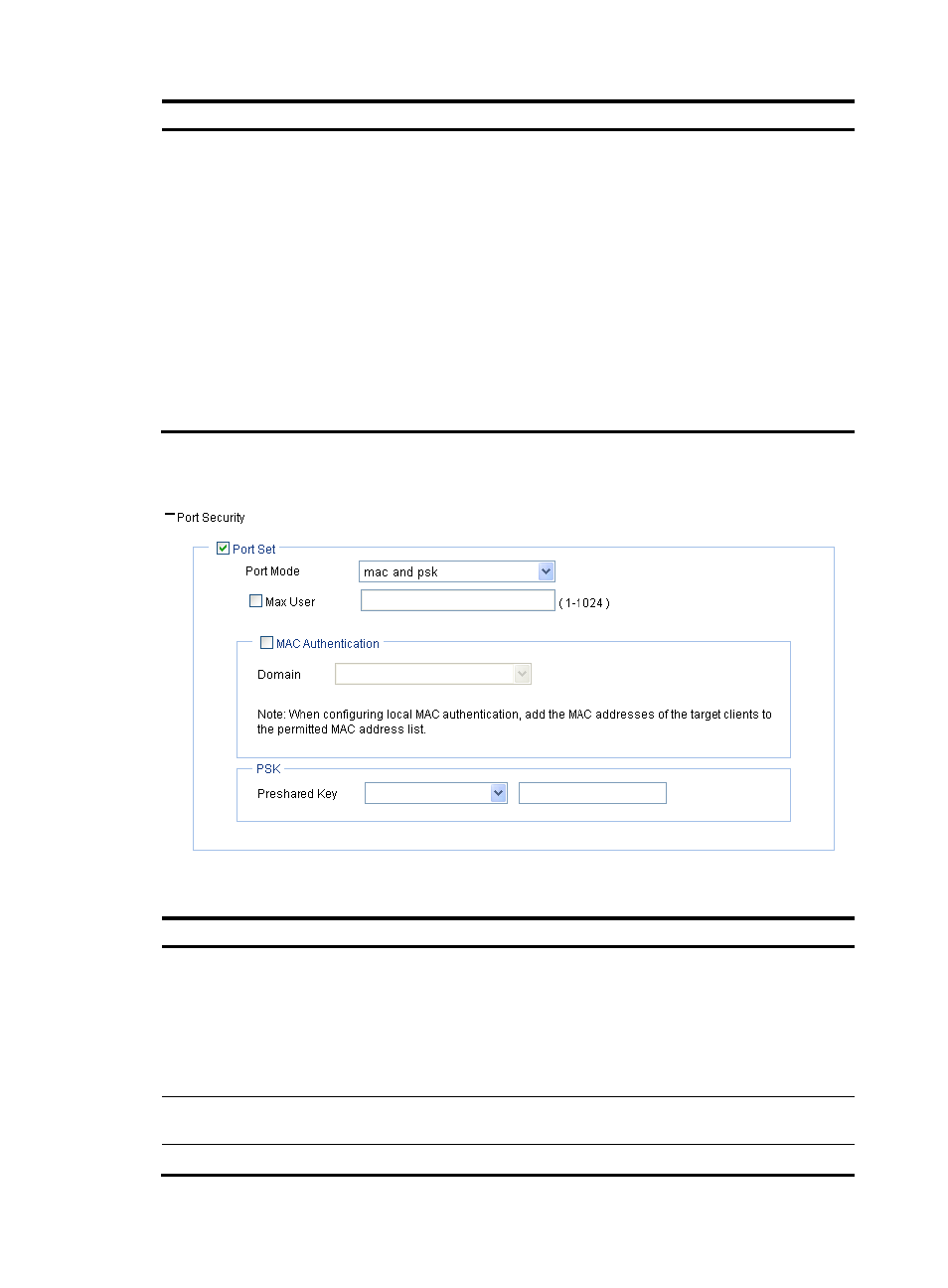
Figure 278 mac and psk port security configuration page
Table 104 Configuration items
Item Description
Port Mode
mac and psk—MAC-based authentication must be performed on access
users first. If MAC-based authentication succeeds, an access user has to use
the pre-configured PSK to negotiate with the device. Access to the port is
allowed only after the negotiation succeeds.
Select Wireless Service > Access Service from the navigation tree, and click
MAC Authentication List to enter the page for configuring a MAC
authentication list. On the page, enter the MAC address of the client.
Max User
Control the maximum number of users allowed to access the network through
the port.
MAC Authentication
Select MAC Authentication.
