Key chains, Creating trusted rip neighbors using the cli – Avaya P580 User Manual
Page 412
10-8
Avaya P550R, P580, P880, and P882 Multiservice Switch User Guide,v5.3.1
Chapter
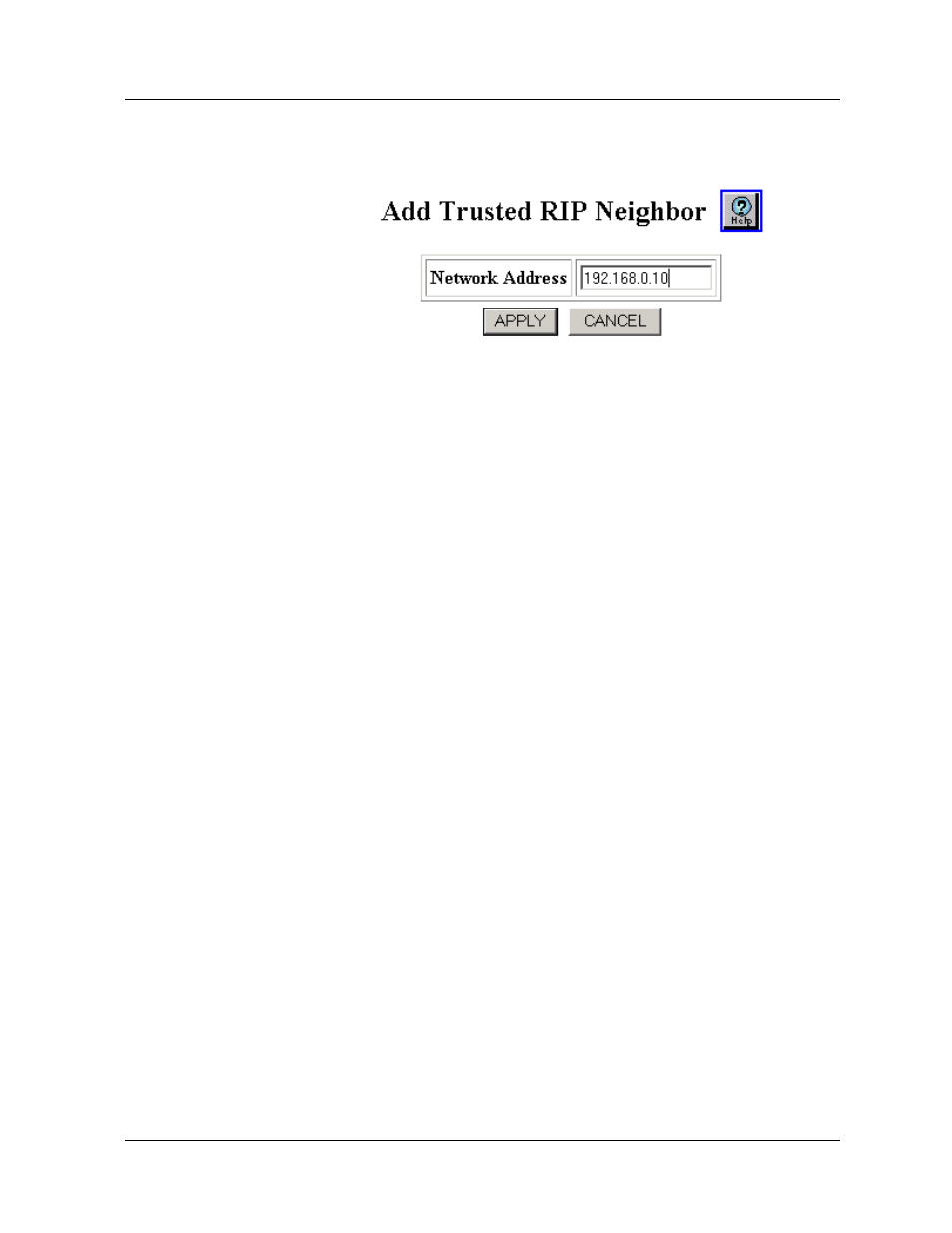
Figure 6-75. Add Trusted RIP Neighbors Dialog Box
6. Enter the IP address for the node that acts as the trusted RIP
neighbor in Network Address field.
7. Click APPLY to save your changes, or CANCEL to restore
previous settings.
Creating
Trusted RIP
Neighbors
Using the CLI
To create a trusted RIP neighbor using the CLI enter the following
command from Configure mode:
> (configure)# route rip
> (configure router rip)# neighbor
Refer to the Command Reference Guide for the Avaya P550R, P580, P880,
and P882 Multiservice Switches, Version 5.3 for details about this
command.
Key Chains
In a full implementation of Key Chains, a Key Chain a set of Keys
each with its own set of parameters used for MD5 encryption. The
parameters are an encryption Key and the period of time that the
key is valid. This key must be identical on each device that will
participate in an exchange of information. In the case of RIP
(version 2 only), routers can use MD5 encryption to ensure that
only routing information packets (RIP packets) from authorized
routers are accepted.
In a simple implementation, the user creates one Key in a Key
Chain and this key is used until it expires.In an advanced
implementation, a Key Chain contains multiple keys each valid for a
limited amount of time. This provides a periodic change of the
encryption key giving the highest level of security. The drawback to
this approach is that every device participating in an exchange, such
as RIP V2 routers on the same subnet, must have their clocks
synchronized. Failure to synchronize would cause devices to use
different keys and hence reject RIP updates from neighboring RIP
routers.
