Information about extended access rules, Access rules for returning traffic – Cisco ASA 5505 User Manual
Page 674
34-4
Cisco ASA 5500 Series Configuration Guide using the CLI
Chapter 34 Configuring Access Rules
Information About Access Rules
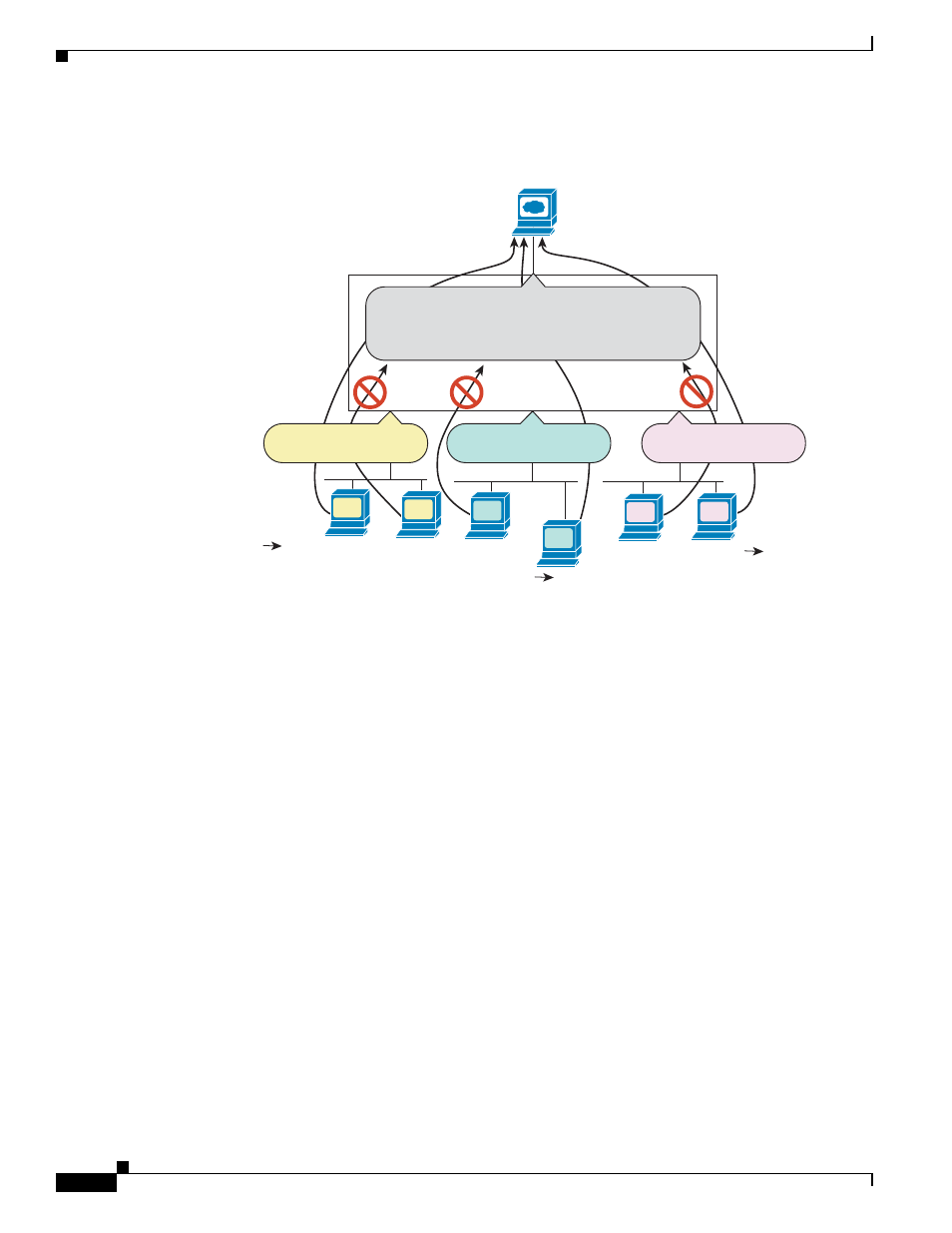
Figure 34-1
Outbound Access List
See the following commands for this example:
hostname(config)# access-list OUTSIDE extended permit tcp host 10.1.1.14
host 209.165.200.225 eq www
hostname(config)# access-list OUTSIDE extended permit tcp host 10.1.2.67
host 209.165.200.225 eq www
hostname(config)# access-list OUTSIDE extended permit tcp host 10.1.3.34
host 209.165.200.225 eq www
hostname(config)# access-group OUTSIDE out interface outside
Information About Extended Access Rules
This section describes information about extended access rules and includes the following topics:
•
Access Rules for Returning Traffic, page 34-4
•
•
Management Access Rules, page 34-5
Access Rules for Returning Traffic
For TCP and UDP connections for both routed and transparent mode, you do not need an access rule to
allow returning traffic because the ASA allows all returning traffic for established, bidirectional
connections.
Web Server:
209.165.200.225
Inside
HR
Eng
Outside
Static NAT
209.165.201.4
10.1.1.14
Static NAT
209.165.201.6
10.1.2.67
Static NAT
209.165.201.8
10.1.3.34
ACL Outbound
Permit HTTP from
10.1.1.14
,
10.1.2.67
,
and
10.1.3.34
to
209.165.200.225
Deny all others
ACL Inbound
Permit from
any
to
any
ACL Inbound
Permit from
any
to
any
ACL Inbound
Permit from
any
to
any
ASA
333823
