Cisco ASA 5505 User Manual
Page 1921
C-23
Cisco ASA 5500 Series Configuration Guide using the CLI
Appendix C Configuring an External Server for Authorization and Authentication
Configuring an External LDAP Server
Use this attribute to create an Allow Access (TRUE) or a Deny Access (FALSE) condition for the
protocols and enforce the method for which the user is allowed access.
For this simplified example, by mapping the tunnel protocol IPsec/IKEv1 (4), you can create an allow
(true) condition for the Cisco VPN client. You also map WebVPN (16) and SVC/AC (32), which are
mapped as a value of 48 (16+32) and create a deny (false) condition. This allows the user to connect to
the ASA using IPsec, but any attempt to connect using clientless SSL or the AnyConnect client is denied.
Another example of enforcing dial-in allow access or deny access is available in the Tech Note ASA/PIX:
Mapping VPN Clients to VPN Group Policies Through LDAP Configuration Example at the following
URL:
ttp://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a008089149d.sht
ml
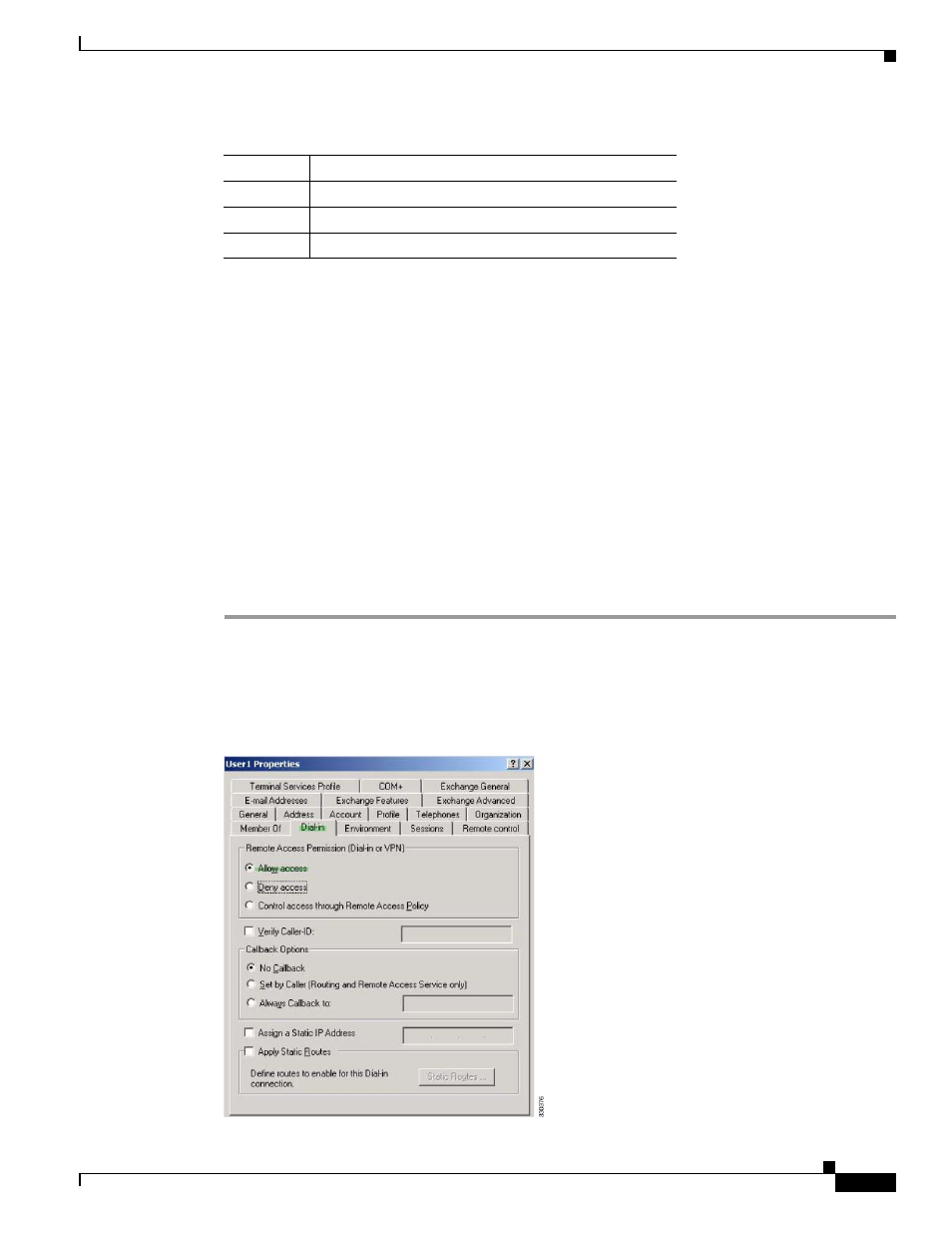
To configure the user attributes on the AD/LDAP server, perform the following steps:
Step 1
Right-click the user.
The Properties dialog box appears.
Step 2
Click the Dial-in tab, then click the Allow Access radio button (
).
Figure C-9
AD/LDAP User1 - Allow Access
16
Clientless SSL
32
SSL client—AnyConnect or SSL VPN client
64
IPsec (IKEv2)
1.
IPsec and L2TP over IPsec are not supported simultaneously. Therefore, the values
4 and 8 are mutually exclusive.
2.
See note 1.
Table C-6
Bitmap Values for Cisco Tunneling-Protocol Attribute (continued)
Value
Tunneling Protocol
