Cisco ASA 5505 User Manual
Page 1377
64-25
Cisco ASA 5500 Series Configuration Guide using the CLI
Chapter 64 Configuring IPsec and ISAKMP
Configuring IPsec
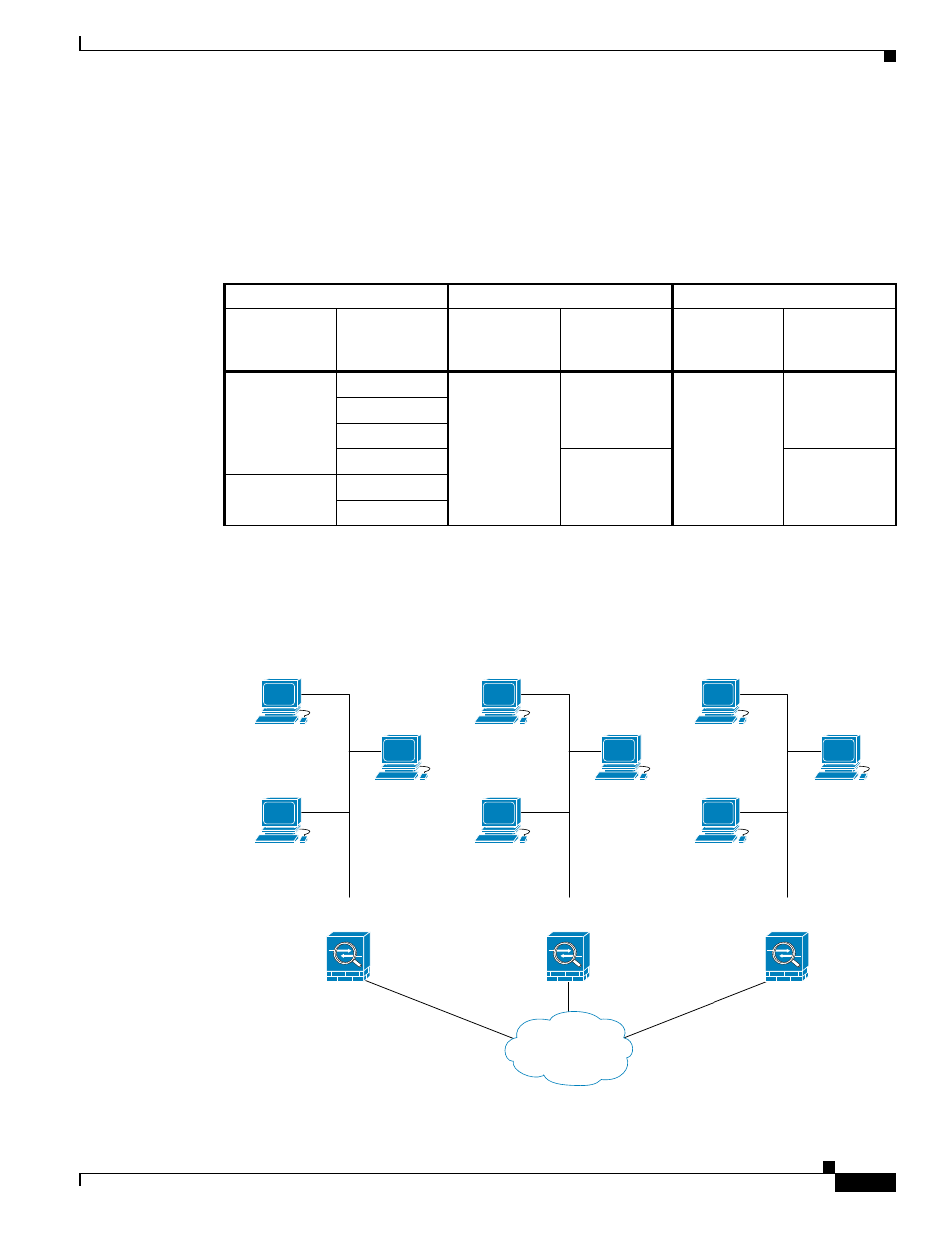
To complete the security appliance configuration in the example network, we assign mirror crypto maps
to Security Appliances B and C. However, because security appliances ignore deny ACEs when
evaluating inbound, encrypted traffic, we can omit the mirror equivalents of the deny A.3 B
and deny A.3 C ACEs, and therefore omit the mirror equivalents of Crypto Map 2. So the configuration
of cascading ACLs in Security Appliances B and C is unnecessary.
shows the ACLs assigned to the crypto maps configured for all three ASAs in
.
maps the conceptual addresses shown in
to real IP addresses.
Figure 64-3
Effect of Permit and Deny ACEs on Traffic (Real Addresses)
Table 64-4
Example Permit and Deny Statements (Conceptual)
Security Appliance A
Security Appliance B
Security Appliance C
Crypto Map
Sequence
No.
ACE Pattern
Crypto Map
Sequence
No.
ACE Pattern
Crypto Map
Sequence
No.
ACE Pattern
1
deny A.3 B
1
permit B A
1
permit C A
deny A.3 C
permit A B
permit A C
permit B C
permit C B
2
permit A.3 B
permit A.3 C
A.1
192.168.3.1
A.2
192.168.3.2
A.3
192.168.3.3
Human Resources
A
192.168.3.0/26
143514
B.1
192.168.12.1
B.2
192.168.12.2
B.2
192.168.12.3
B
192.168.12.0/29
C.1
192.168.201.1
C.2
192.168.201.2
C.3
192.168.201.3
C
192.168.201.0/27
Internet
