Table c-7, List – Cisco ASA 5505 User Manual
Page 1926
C-28
Cisco ASA 5500 Series Configuration Guide using the CLI
Appendix C Configuring an External Server for Authorization and Authentication
Configuring an External RADIUS Server
are sent from the ASA to the RADIUS server for authentication and authorization requests. All four
previously listed attributes are sent from the ASA to the RADIUS server for accounting start,
interim-update, and stop requests. Upstream RADIUS attributes 146, 150, 151, and 152 were introduced
in ASA Version 8.4.3.
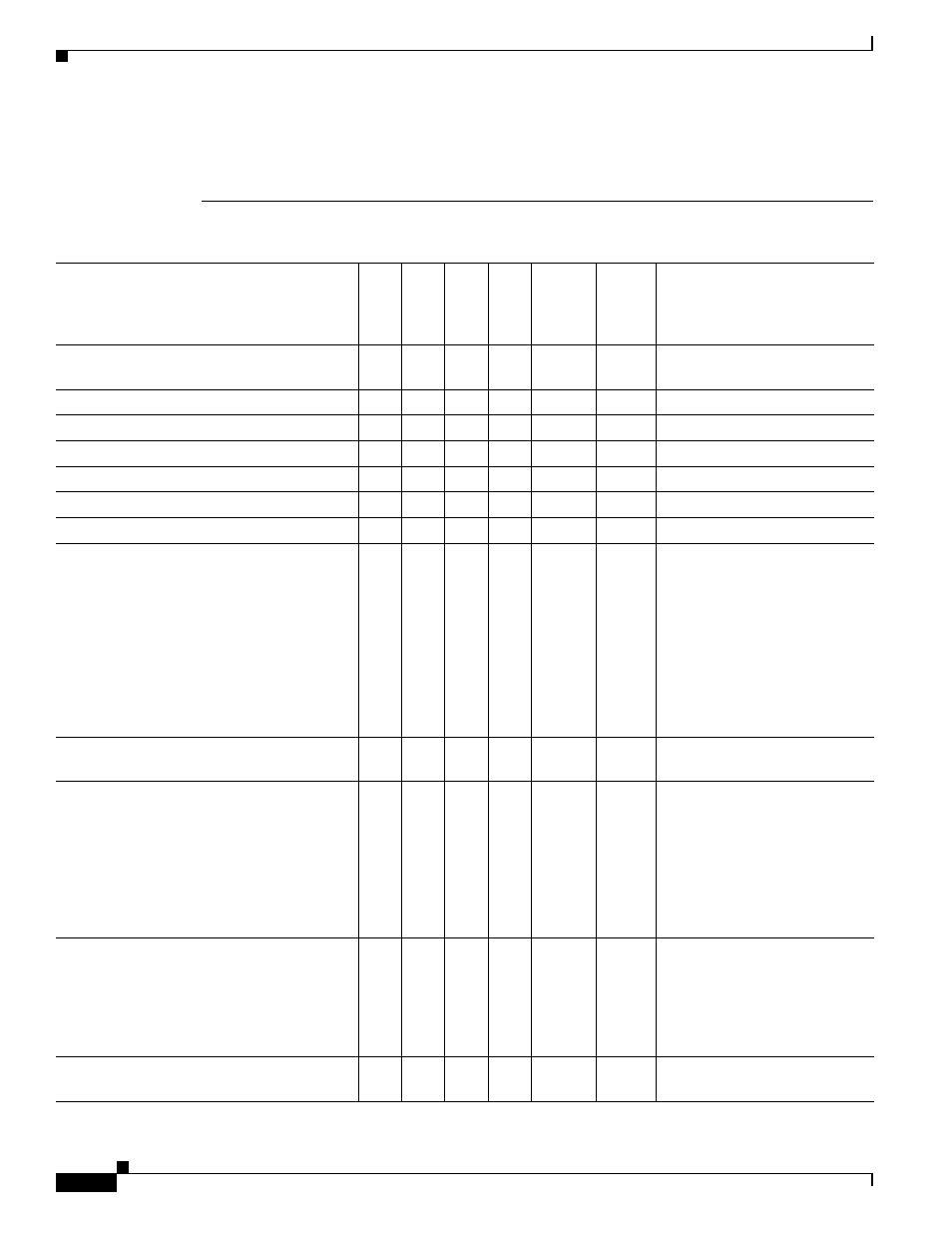
Table C-7
ASA Supported RADIUS Attributes and Values
Attribute Name
VPN
3000
ASA
PIX
Attr.
No.
Syntax/
Type
Single
or
Multi-
Valued
Description or Value
Access-Hours
Y
Y
Y
1
String
Single
Name of the time range, for
example, Business-hours
Simultaneous-Logins
Y
Y
Y
2
Integer
Single
0 - 2147483647
Primary-DNS
Y
Y
Y
5
String
Single
An
IP
address
Secondary-DNS
Y
Y
Y
6
String
Single
An IP address
Primary-WINS
Y
Y
Y
7
String
Single
An IP address
Secondary-WINS
Y
Y
Y
8
String
Single
An IP address
SEP-Card-Assignment
9
Integer
Single
Not used
Tunneling-Protocols
Y
Y
Y
11
Integer
Single
1 = PPTP
2 = L2TP
4 = IPSec (IKEv1)
8 = L2TP/IPSec
16 = WebVPN
32 = SVC
64 = IPsec (IKEv2)
8 and 4 are mutually exclusive
(0 - 11, 16 - 27, 32 - 43, 48 - 59
are legal values).
IPsec-Sec-Association
Y
12
String
Single
Name of the security
association
IPsec-Authentication
Y
13
Integer
Single
0 = None
1 = RADIUS
2 = LDAP (authorization only)
3 = NT Domain
4 = SDI
5 = Internal
6 = RADIUS with Expiry
7 = Kerberos/Active Directory
Banner1
Y
Y
Y
15
String
Single
Banner string to display for
Cisco VPN remote access
sessions: IPsec IKEv1,
AnyConnect
SSL-TLS/DTLS/IKEv2, and
Clientless SSL
IPsec-Allow-Passwd-Store
Y
Y
Y
16
Boolean Single
0 = Disabled
1 = Enabled
