B&B Electronics VFG3000 - Manual User Manual
Page 188
C
REATING
U
SERS
V
LINX
F
IELDBUS
G
ATEWAY
M
ANAGER
U
SER
M
ANUAL
P
AGE
172
value for this setting will produce an insecure system, while too low a value will
produce a system that is awkward for operators.
•
The Clear Logon Name property is used to indicate whether or not the username
should be cleared before asking the operator to logon. If this setting is disabled,
the previous username will be displayed, and only the password will need to be
re-entered. Enabling this feature produces higher security, and may be required
to comply with security standards in certain industries.
•
The Default Access properties are used to indicate the access to be provided to
various objects should no specific access be defined for that item. The settings
are as described in the Access Control section above.
•
The Default Logging properties are used to indicate whether changes to mapped
and unmapped tags should be logged should no specific logging criteria be
defined for a tag. It is not possible to log programmatic access by default, as
such logging should be carefully considered to avoid excessive log activity.
•
The Logging Control properties are used to define whether and how the security
logs should be created. Refer to the Configuring Data Logging chapter for
information on how the data is written and how files are named.
C
REATING
U
SERS
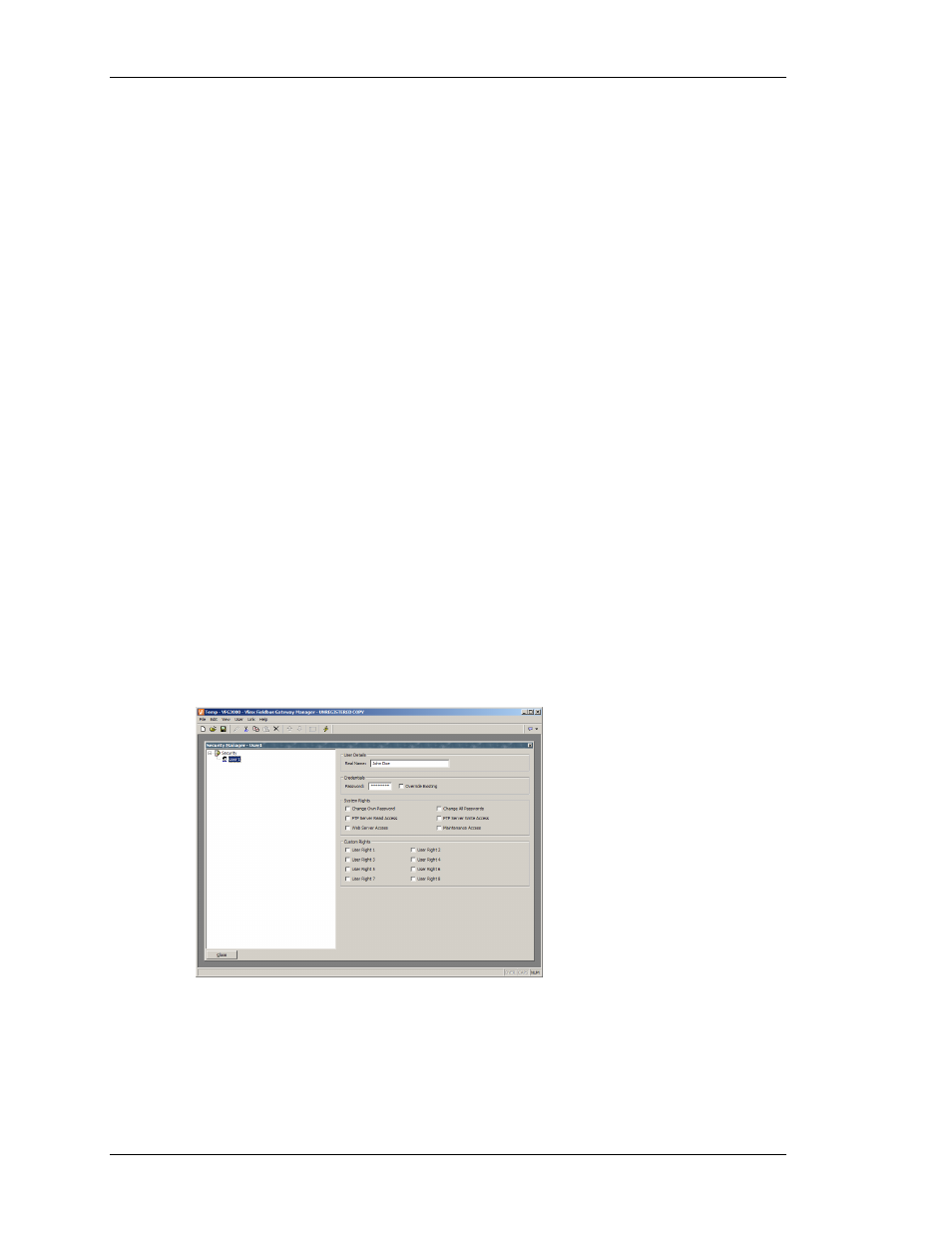
You may use the Create User button to create as many users as you need. The users may be
renamed or deleted using the left-hand pane. To select a user, either click on the name in the
list, or use the up and down arrows in the toolbar. Alternatively, you can use the
Alt+Left
and
Alt+Right
key combinations to move up and down the list as required. These keys will
work no matter which pane is selected.
Each user has the following properties…
•
The Real Name property is used to record the user’s identity in security logs, and
in the Security Manager primitive that is used to change passwords from the
Gateway. If maximum security is required, the user name should not be easily
derived from the real name.
