5 crypto map interfaces, Crypto map interfaces – Motorola Series Switch WS5100 User Manual
Page 284
6-60 WS5100 Series Switch System Reference Guide
a. Define the
Seq #/Name
. The lower the number, the higher the priority among Crypto Maps.
b. Enter the name of the
Transform set
used with the Crypto Map.
7. Click
OK
when completed to save the configuration of the Crypto Map transform set.
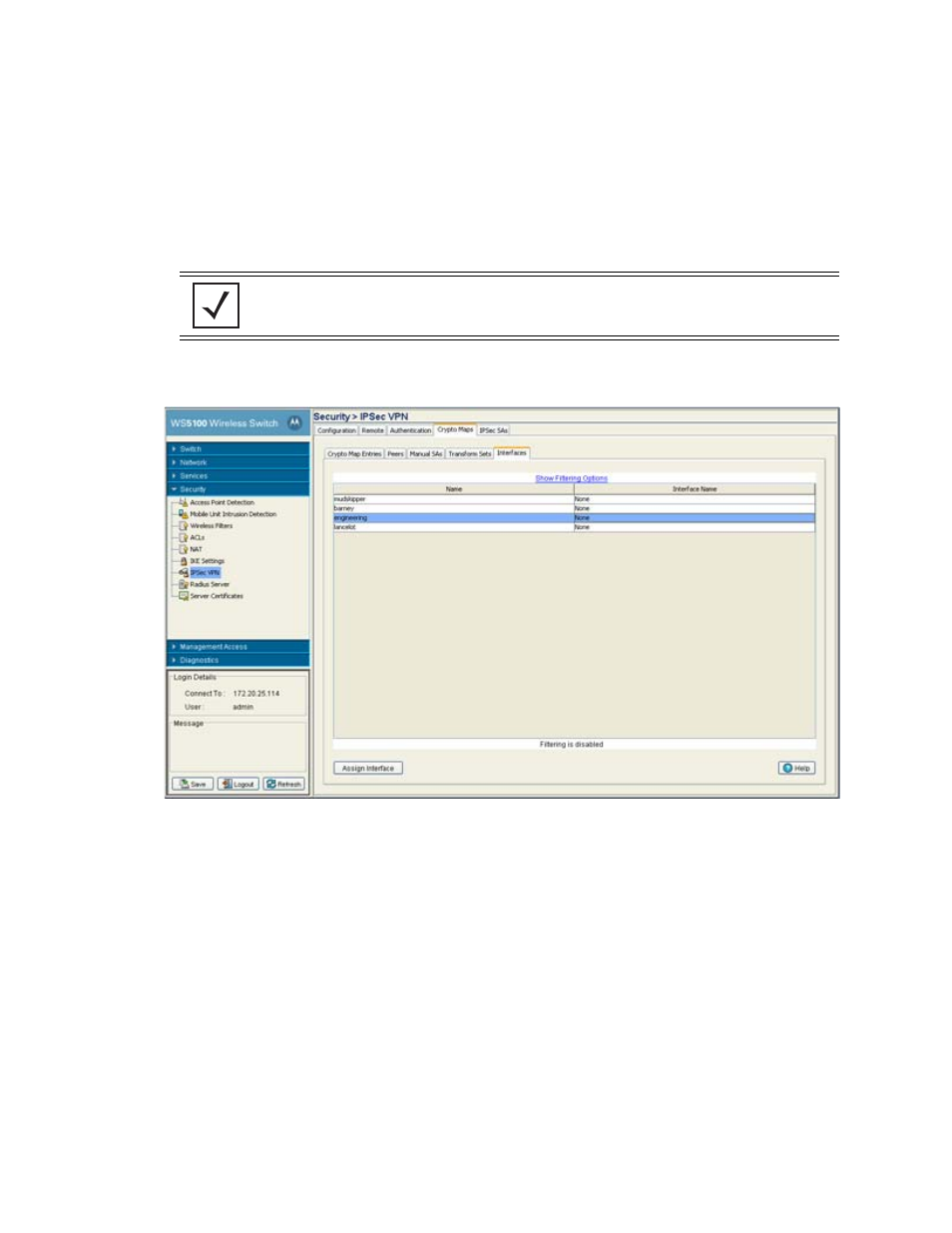
6.8.4.5 Crypto Map Interfaces
To review the interfaces currently available to the Crypto Maps or assign an interface:
1. Select
Security
>
IPSec VPN
from the main menu tree.
2. Click the
Crypto Maps
tab and select
Interfaces
.
3. Refer to the following read-only information displayed within the
Interfaces
tab.
4. Click the
Assign Interface
button to assign a Crypto Map to each interface through which IPSec traffic
flows.
The security appliance supports IPSec on all interfaces. Assigning the Crypto Map set to an interface
instructs the security appliance to evaluate all the traffic against the Crypto Map set and to use the
specified policy during connection or SA negotiation. Assigning a Crypto Map to an interface also
initializes run-time data structures, such as the SA database and the security policy database.
Reassigning a modified Crypto Map to the interface resynchronizes the run-time data structures with the
NOTE: A Crypto Map cannot get applied to more than one interface at a time.
Name
Displays the name of the Crypto Maps available for interface.
Interface Name
Displays the name of the interface through which IPSec traffic will flow. Applying the Crypto
Map set to an interface instructs the switch to evaluate all the interface's traffic against the
Crypto Map set and to use the specified policy during connection or security association
negotiation on behalf of traffic to be protected by crypto (either CET or IPSec).
