3 crypto map manual sas, Crypto map manual sas – Motorola Series Switch WS5100 User Manual
Page 281
Switch Security
6-57
a. Define the
Seq # /Name
for the new peer. The lower the number, the higher the priority among
Crypto Maps.
b. Enter the name of the
IKE Peer
used with the Crypto Map to build an IPSec security association.
7. Click
OK
when completed to save the configuration of the new Crypto Map peer.
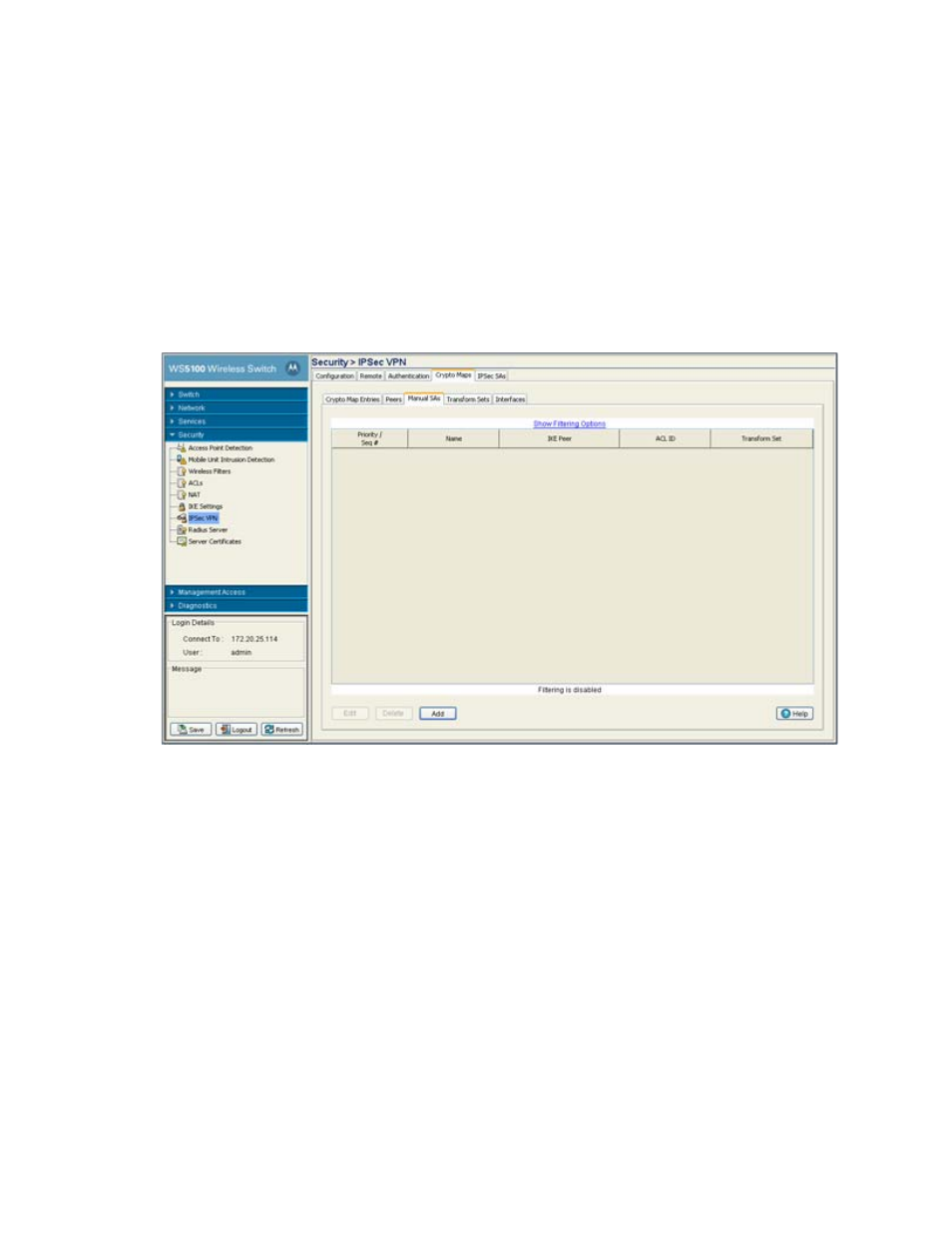
6.8.4.3 Crypto Map Manual SAs
To review, revise or add a Crypto Map using a manually defined security association:
1. Select
Security
>
IPSec VPN
from the main menu tree.
2. Click the
Crypto Maps
tab and select
Manual SAs
.
3. Refer to the read-only information displayed within the
Manual SAs
tab to determine whether a Crypto
Map with a manually defined security association requires modification or a new one requires creation.
4. If a Crypto Map with a manual security association requires revision, select it from amongst those
displayed and click the
Edit
button to revise its Seq #, IKE Peer, ACL ID and security protocol.
5. Select an existing table entry and click the
Delete
button to remove from the list of those available to
the switch.
Priority / Seq #
Displays the Seq # (sequence number) used to determine priority. The lower the number, the
higher the priority.
Name
Displays the name assigned to the security association.
IKE Peer
Displays the IKE peer used with the Crypto Map to build an IPSec security association.
ACL ID
Displays the ACL ID the Crypto Map’s data flow is using to establish access permissions.
Transform Set
Displays the transform set representing a combination of security protocols and algorithms.
During the IPSec security association negotiation, peers agree to use a particular transform
set for protecting the data flow.
