Motorola Series Switch WS5100 User Manual
Page 226
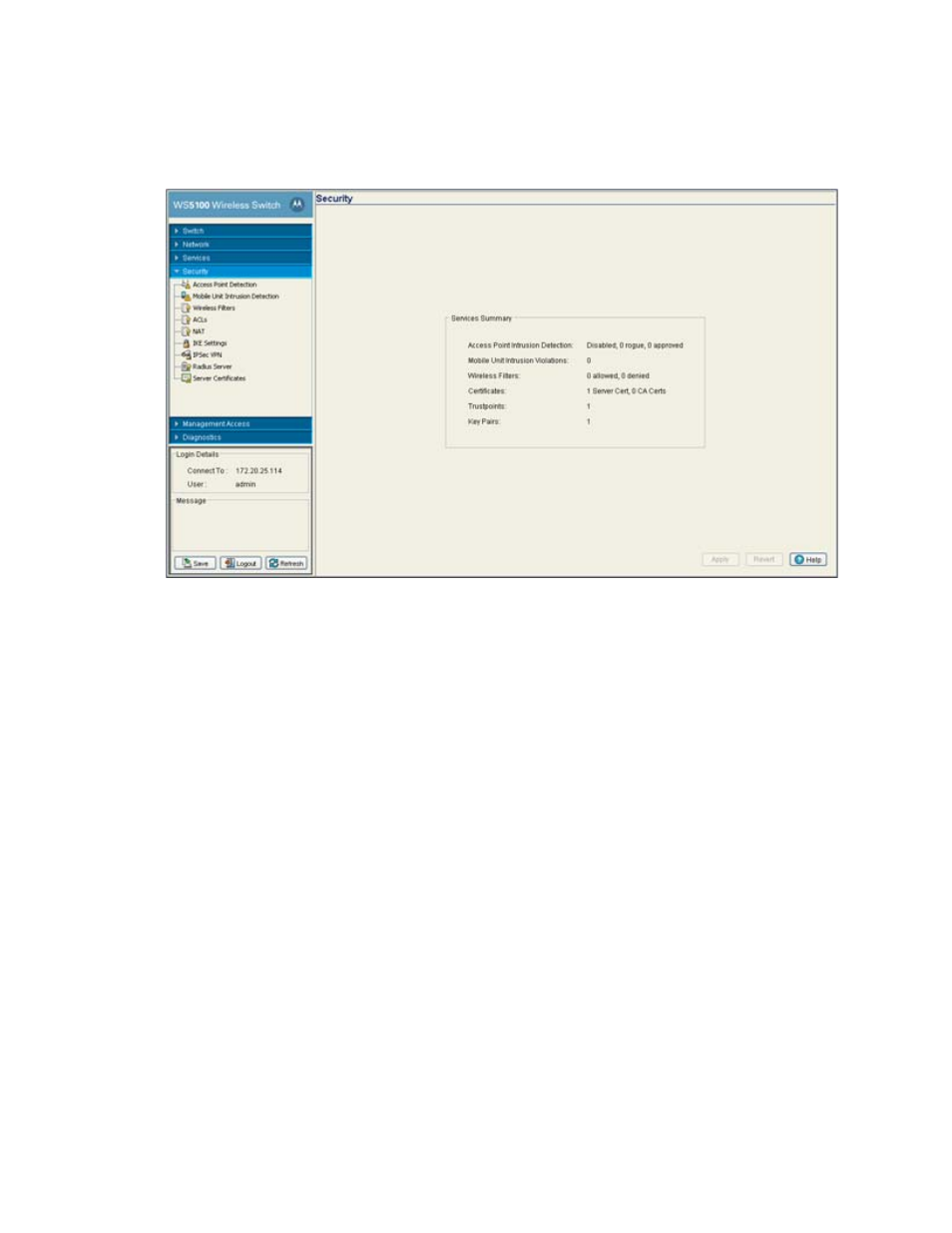
6-2 WS5100 Series Switch System Reference Guide
To view main menu security information:
1. Select
Security
from the main menu tree.
2. Refer to the following information to discern if configuration changes are warranted:
The
Apply
and
Cancel
buttons are greyed out within this screen, as there is no data to be configured or saved.
Access Port Intrusion
Detection
Displays the Enable or Disable state of the switch to detect potentially hostile access ports
(the definition of which defined by you). Once detected, these devices can be added to a list
of devices either approved or denied from interoperating within the switch managed
network. For more information, see
AP Intrusion Detection on page 6-3
.
Mobile Unit Intrusion
Detection
Displays the state of the switch protecting against threats from MUs trying to find network
vulnerabilities. For more information, see
MU Intrusion Detection on page 6-9
.
Wireless Filters
Displays the state of the current filters used to either allow or deny a MAC address (or groups
of MAC addresses) from associating with the switch. For more information, see
.
Certificates
Displays the number of Server and CA certificates currently used by the switch. For more
information, see
Creating Server Certificates on page 6-74
Trustpoints
Displays the number of trustpoints currently in use by this switch. The trustpoint
signing the certificate can be a certificate authority, corporation or an individual. A
trustpoint represents a CA/identity pair and contains the identity of the CA, CA-
specific configuration parameters, and an association with one enrolled identity
certificate.
For more information, see
Using Trustpoints to Configure Certificates on page 6-75
.
Key Pairs
Displays the number of Key Pairs currently used by the switch. For more information, see
Configuring Trustpoint Associated Keys on page 6-81
.
