Motorola Series Switch WS5100 User Manual
Page 102
4-28 WS5100 Series Switch System Reference Guide
across an insecure network connection. Once a MU and server prove their identity, they can encrypt all
communications to assure privacy and data integrity. Kerberos can only be used on the with Motorola clients.
To configure a Kerberos authentication scheme for a WLAN:
1. Select
Network
>
Wireless LANs
from the main menu tree.
2. Select an existing WLAN from those displayed within the
Configuration
tab.
3. Click the
Edit
button.
A WLAN screen displays with the WLAN’s existing configuration. Refer to the
Authentication
and
Encryption
columns to assess the WLAN’s existing security configuration.
4. Select the
Kerberos
button from within the Authentication field.
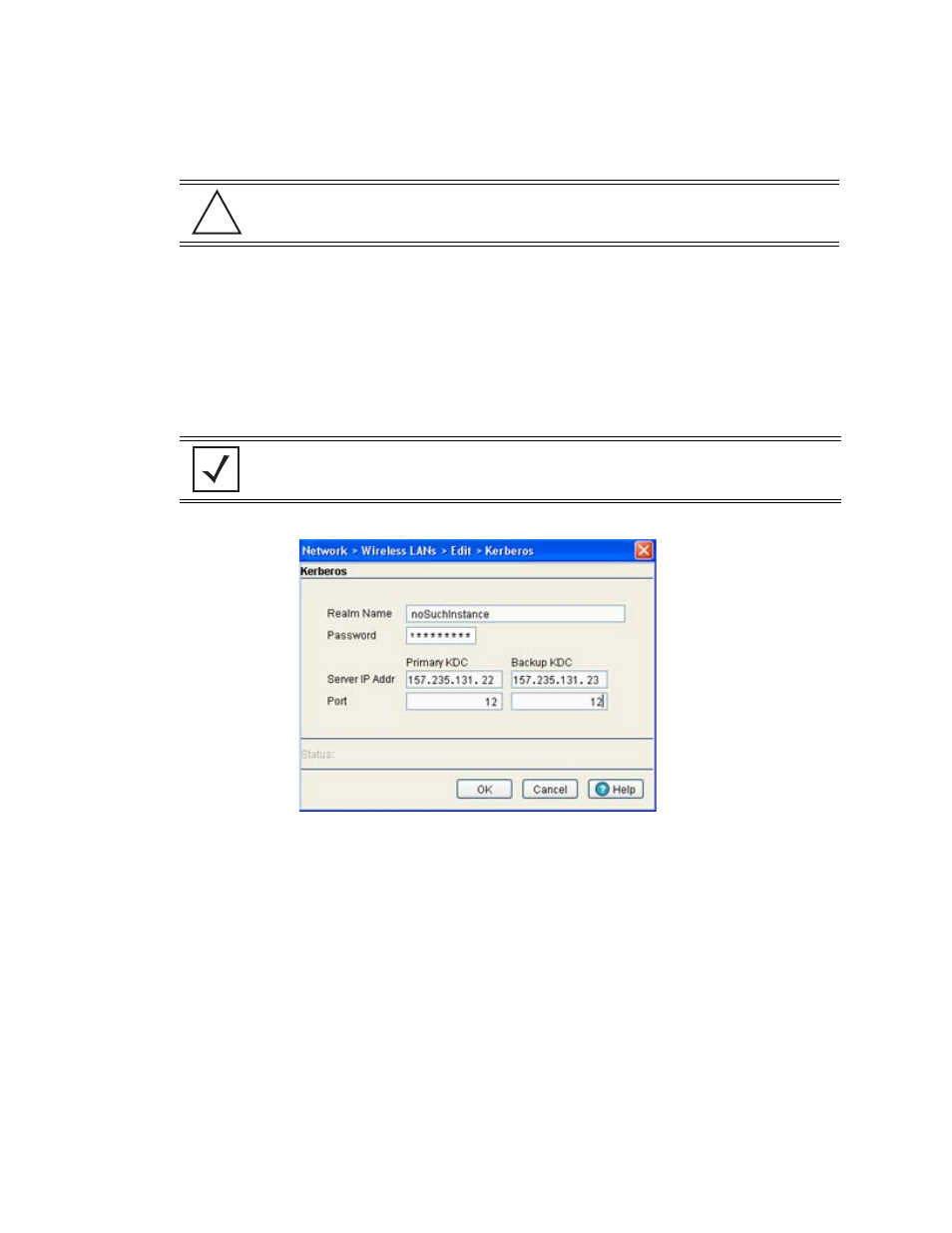
5. Click the
Config
button to the right of the Kerberos checkbox. The
Kerberos
screen displays.
6. Specify a case-sensitive
Realm Name
(for example, MOTOROLA.COM).
The realm name is the name domain/realm name of the KDC Server. A realm name functions similarly to
a DNS domain name. In theory, the realm name is arbitrary. However, in practice a Kerberos realm is
named by uppercasing the DNS domain name associated with hosts in the realm.
7. Enter a
Server IP Addr
(IP address) for the Primary and (if necessary) Backup KDC.
Specify a numerical (non-DNS) IP address for the Primary Key Distribution Center (KDC). The KDC
implements an Authentication Service and a Ticket Granting Service, whereby an authorized user is
granted a ticket encrypted with the user's password. The KDC has a copy of every user password
provided. Optionally, specify a numerical (non-DNS) IP address for a backup KDC. Backup KDCs are often
referred to as slave servers.
8. Specify the
Ports
on which the Primary and Backup KDCs reside.
The default port number for Kerberos Key Distribution Centers is port 88.
CAUTION: Kerberos makes no provisions for host security. Kerberos assumes it is
running on a trusted host with an untrusted network. If host security is compromised,
Kerberos is compromised as well
NOTE: Kerberos requires at least one encryption scheme be enabled (WEP 128 or other).
If neither WEP 128 or KeyGuard is enabled, WEP 128 will automatically be enabled for
use with Kerberos.
!
