Motorola Series Switch WS5100 User Manual
Page 263
Switch Security
6-39
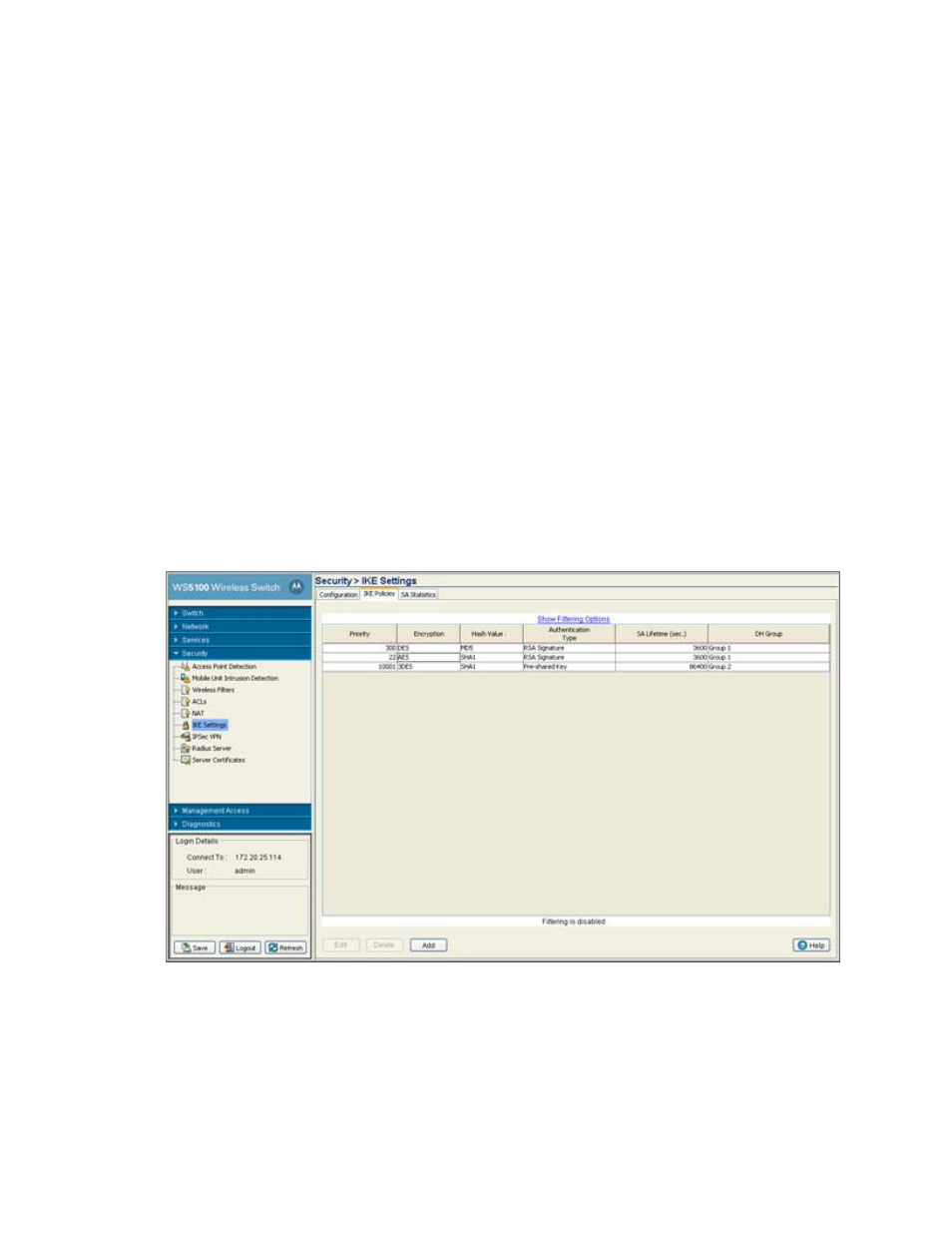
• A priority value (1 through 65,543, with 1 as highest priority permitted)
• An authentication scheme ensure the credentials of the peers
• An encryption scheme protecting the data
• A HMAC method ensuring the identity of the sender, and validating that the message has not been
altered
• A Diffie-Hellman group establishing the strength of the of the encryption-key algorithm.
• A time limit for how long the encryption key is used before it is replaced.
If IKE policies are not defined, the switch uses the default policy (always set to the lowest priority) and
contains the default values. When IKE negotiations start, the peer initiating the negotiation sends its policies
to the remote peer. The remote peer searches for a match with its own policies using the defined priority
scheme.
A IKE policies match when they have the same encryption, hash, authentication and Diffie-Hellman settings.
The SA lifetime must also be less than or equal to the lifetime in the policy sent. If the lifetimes do not match,
the shorter lifetime applies. If no match exists, IKE refuses negotiation.
To view the current set of IKE policies:
1. Select
Security
>
IKE Settings
from the main menu tree.
2. Click the
IKE Policies
tab.
