1 defining the ike configuration, 1 defining the ike configuration -37, Defining the ike configuration – Motorola Series Switch WS5100 User Manual
Page 261
Switch Security
6-37
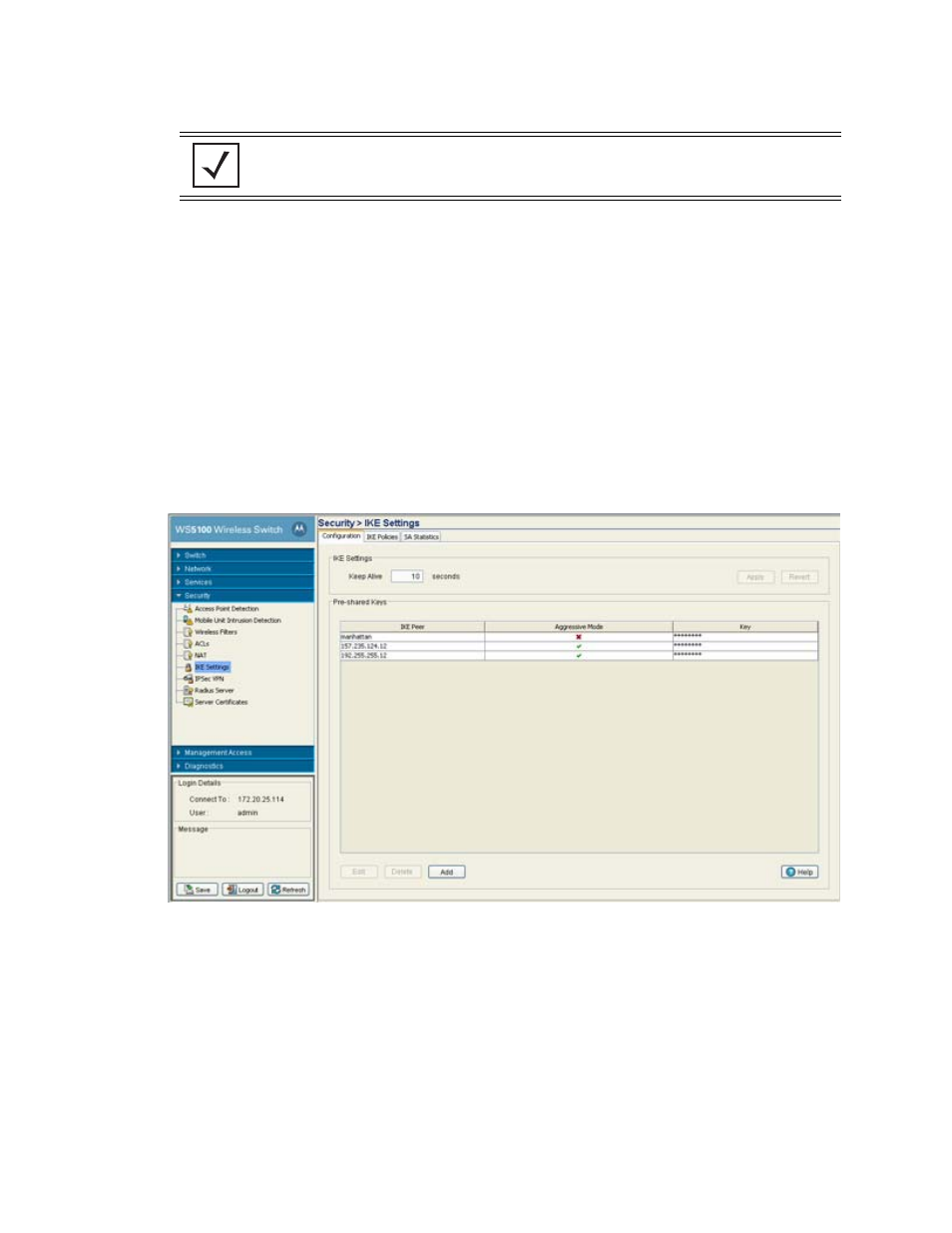
6.7.1 Defining the IKE Configuration
Refer to the
Configuration
tab to enable (or disable) IKE and define the IKE identity (for exchanging
identities) and aggressive mode. Aggressive mode enables you to configure Internet Key Exchange (IKE) pre-
shared keys as IPSec tunnel attributes for IP Security (IPSec) peers.
Use IKE to specify IPSec tunnel attributes for an IPSec peer and initiate an IKE aggressive mode negotiation
with the tunnel attributes. This feature is best implemented in a crypto hub scenario. Users initiate IKE
aggressive mode negotiation with the switch using pre-shared keys specified as tunnel attributes and stored
on the Radius server. This scenario is scalable since the keys are kept at a central repository (the Radius
server) and more than one switch and application can use the information.
To view the current set of IKE configurations:
1. Select
Security
>
IKE Settings
from the main menu tree.
2. Click the
Configurations
tab.
During IKE negotiations, peers must identify themselves to one another. Thus, the configuration you define is
the identification medium for device recognition.
3. Set a
Keep Alive
interval (in seconds) the switch uses for monitoring the continued presence of a peer
and report of the client's continued presence to the peer. The client notifies you when the peer is no
longer present.
4. Click the
Apply
button (within the IKE Settings field) to save the configuration.
5. Click the
Revert
(within the IKE Settings field) to rollback to the previous configuration.
NOTE: By default, the IKE feature is enabled on the switch. Motorola does not support
disabling the IKE server.
