Interlogix NS3550-2T-8S User Manual User Manual
Page 270
IFS NS3552-8P-2S AND NS3550-2T-8S User Manual
270
the end-host, and if such frames are not seen within the next Aging Period, the
end-host is assumed to be disconnected, and the corresponding resources are
freed on the switch.
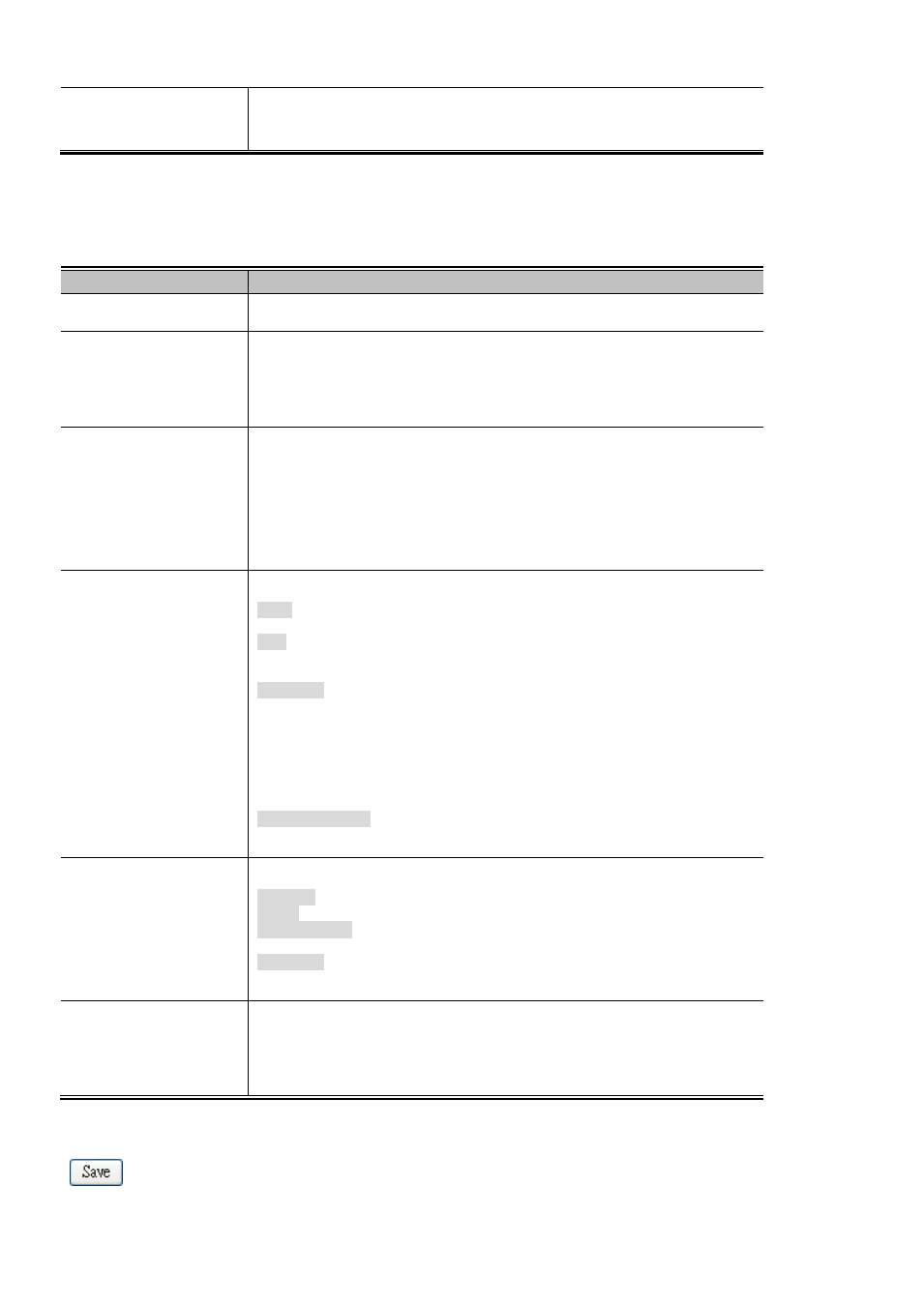
Port Configuration
The table has one row for each port on the selected switch in the stack and a number of columns, which are:
Object
Description
• Port
The port number for which the configuration below applies.
• Mode
The Configuration All with available options will assign to whole ports.
Controls whether Limit Control is enabled on this port. Both this and tmust be set to Enabled for Limit Control to be in effect. Notice that other
modules may still use the underlying port security features without enabling Limit
Control on a given port.
• Limit
The maximum number of MAC addresses that can be secured on this port. This
number cannot exceed 1024. If the limit is exceeded, the correspondiis
taken.
The stack switch is "born" with a total number of MAC addresses from which all
ports draw whenever a new MAC address is seen on a Port Security-enabled
port. Since all ports draw from the same pool, it may happen that a configured
maximum cannot be granted, if the remaining ports have already used all
available MAC addresses.
• Action
The Configuration All with available options will assign to whole ports.
is reached, the switch can take one of the following actions:
None: Do not allow more thaMAC addresses on the port, but take no
further action.
Trap: 1 MAC address is seen on the port send an SNMP trap. If Aging is
disabled, only one SNMP trap will be sent, but with Aging enabled, new SNMP
traps will be sent every time the limit gets exceeded.
Shutdown+ 1 MAC addresses is seen on the port, shut down the port.
This implies that all secured MAC addresses will be removed from the port, and
no new will be learned. Even if the link is physically disconnected and
reconnected on the port (by disconnecting the cable), the port will remain shut
down. There are three ways to re-open the port:
1) Boot the stack or elect a new master the switch,
2) Disable and re-enable Limit Control on the port or the stack switch,
3) Click tbutton.
Trap & Shutdown+ 1 MAC addresses is seen on the port, both the "Trap"
and the "Shutdown" actions described above will be taken.
• State
This column shows the current state of the port as seen from the Limit Control's
point of view. The state takes one of four values:
Disabled: Limit Control is either globally disabled or disabled on the port.
Ready: The limit is not yet reached. This can be shown for all
Limit Reached: Indicates that the limit is reached on this port. This state can only
be shown iis set to None or Trap.
Shutdown: Indicates that the port is shut down by the Limit Control module. This
state can only be shown iis set to Shut down or Trap & Shutdown.
• Reopen Button
If a port is shut down by this module, you may reopen it by clicking this button,
which will only be enabled if this is the case. For other methods, refer to Shut
down in tsection.
Note, that clicking the reopen button causes the page to be refreshed, so
non-committed changes will be lost.
Buttons
: Click to save changes.
