3 network access server configuration – Interlogix NS3550-2T-8S User Manual User Manual
Page 238
IFS NS3552-8P-2S AND NS3550-2T-8S User Manual
238
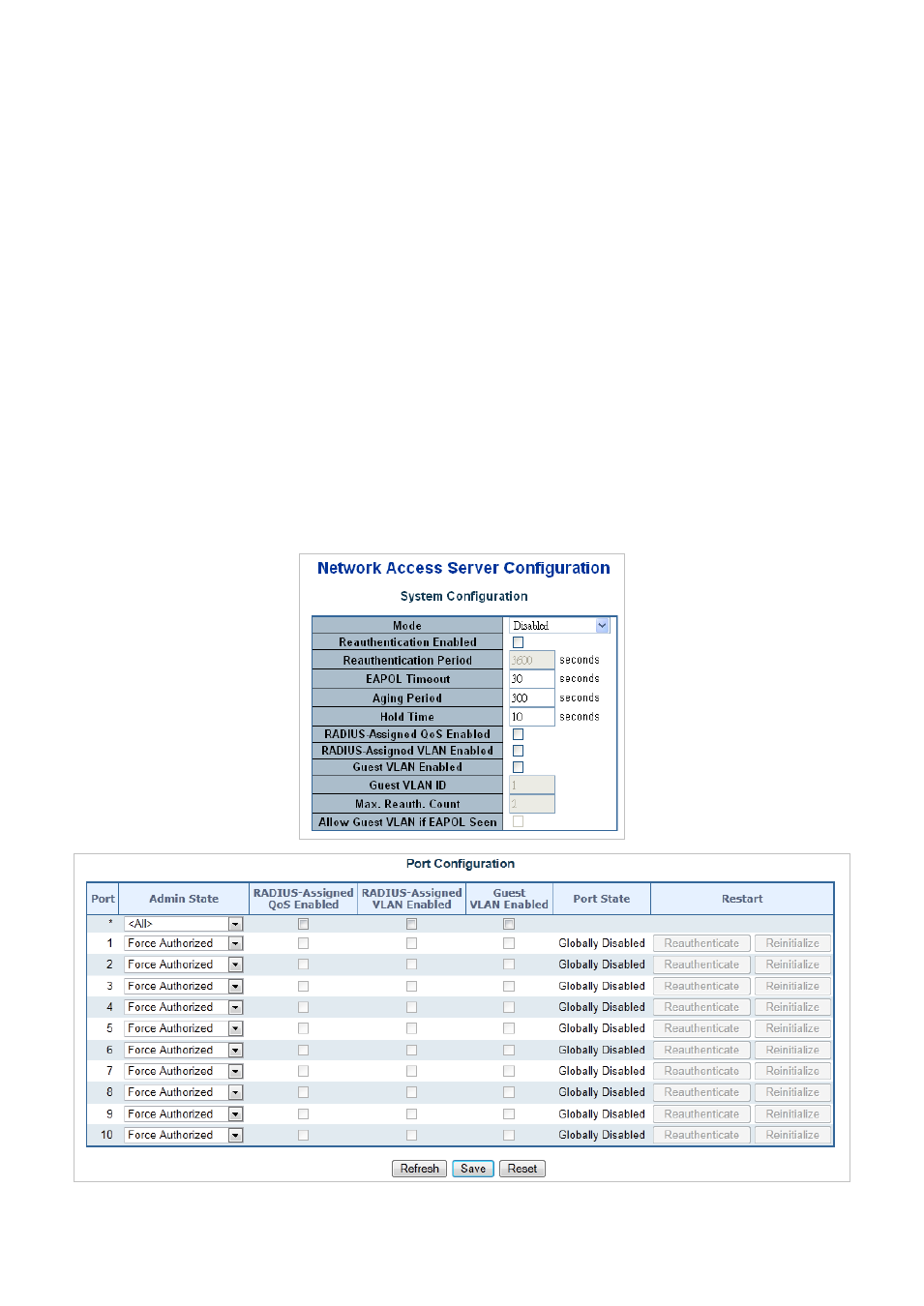
4.11.3 Network Access Server Configuration
This page allows you to configure theand MAC-based authentication system and port settings.
The IEEE 802.1X standard defines a port-based access control procedure that prevents unauthorized access to a network by
requiring users to first submit credentials for authentication. One or more central servers, the backend servers, determine
whether the user is allowed access to the network. These backend (RADIUS) servers are configured on the
"Configuration
→Security→AAA" page. The IEEE802.1X standard defines port-based operation, but non-standard variants
overcome security limitations as shall be explored below.
MAC-based authentication allows for authentication of more than one user on the same port, and doesn't require the user to have
special 802.1X supplicant software installed on his system. The switch uses the user's MAC address to authenticate against the
backend server. Intruders can create counterfeit MAC addresses, which makes MAC-based authentication less secure than
802.1 X authentications. The NAS configuration consists of two sections, a system- and a port-wide. The Network Access Server
Configuration screen in
Figure 4-11-4
appears.
Figure 4-11-4: Network Access Server Configuration Page Screenshot
