3 timed-access protects watchdog, Timed-access protection, Rotected – Maxim Integrated High-Speed Microcontroller User Manual
Page 154: Rotection, Cheme
High-Speed Microcontroller User’s Guide
Rev: 062210
154 of 176
whether any bits were modified.
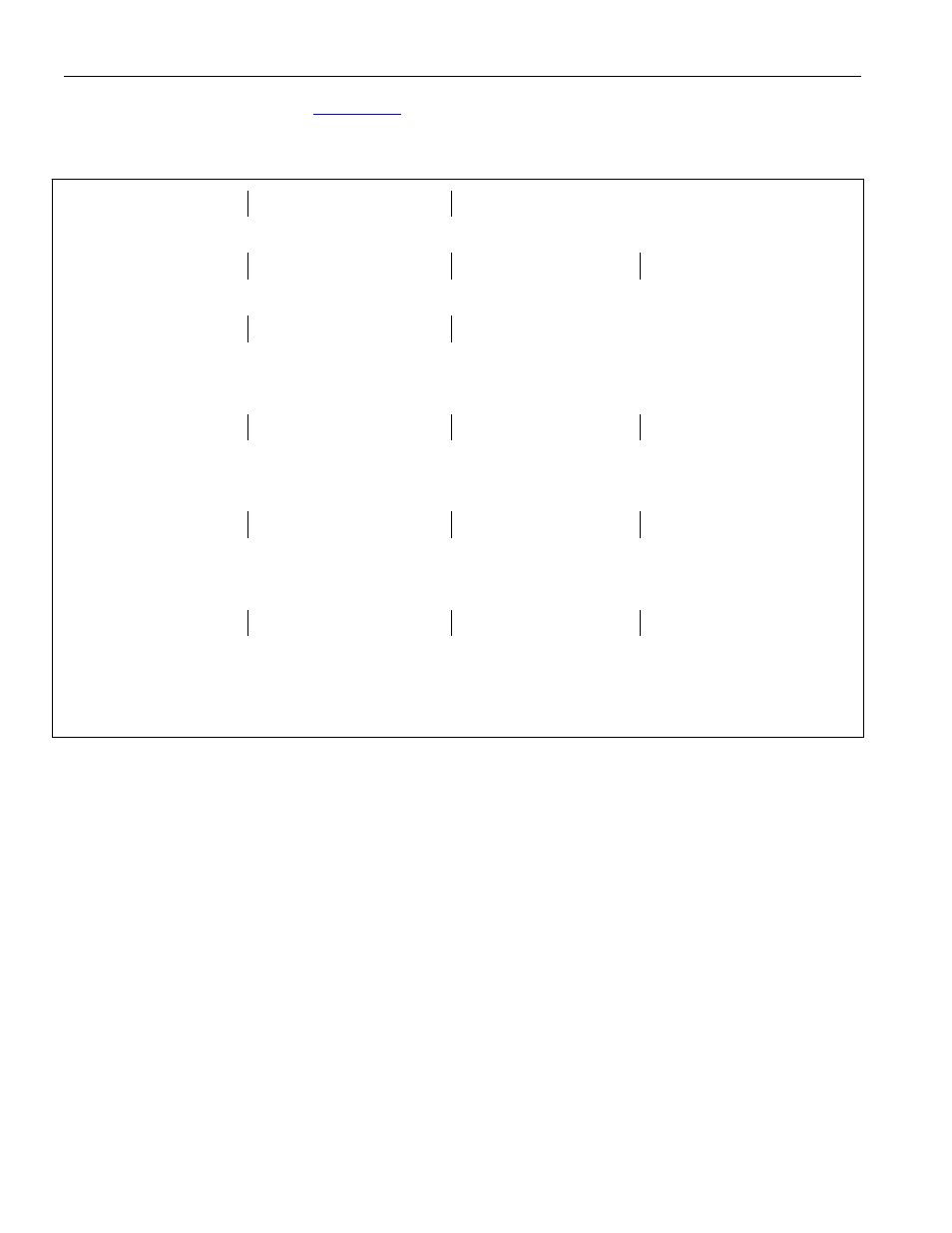
illustrates a number of examples of correct and incorrect use
of the timed-access procedure.
Figure 13-1. Timed-Access Examples
three machine cycles
three machine cycles
three machine cycles
MOV 0C7h, #0AAh
MOV 0C7h, #55h
SETB EWT
three machine cycles
three machine cycles
one machine cycle
two machine cycles
MOV 0C7h, #0AAh
MOV 0C7h, #55h
NOP
SETB EWT
three machine cycles
three machine cycles
three machine cycles
MOV 0C7h, #0AAh
MOV 0C7h, #55h
MOV WDCON, #02h
VALID TIMED-ACCESS PROCEDURES
three machine cycles
one machine cycles
three machine cycle
two machine cycles
MOV 0C7h, #0AAh
NOP
MOV 0C7h, #55H
SETB EWT
*Second write to TA register does not occur within 3 cycles of first write.
three machine cycles
three machine cycles
one machine cycle
three machine cycles
MOV 0C7h, #0AAh
MOV 0C7h, #55H
NOP
MOV WDCON, #02h
*Modification of protected bit did not occur with 3 cycles of second write to TA register.
three machine cycles
three machine cycles
two machine cycle
two machine cycles
MOV 0C7h, #0AAh
MOV 0C7h, #55h
SETB EWT
SETB EWT
*Modification of second protected bit did not complete within 3 cycles of second write to TA register.
INVALID TIMED-ACCESS PROCEDURES
13.3 Timed-Access Protects Watchdog
Any microcontroller-based system can be faced with environmental conditions that are beyond its
designed abilities. These include external signal transients due to component failure, fluctuating power
conditions, massive electrostatic discharge (ESD), and other unexpected system events. When a
microcontroller is exposed to such conditions, program execution can become corrupted. Members of the
high-speed microcontroller family that incorporate a watchdog timer can initiate a reset to recover from
these conditions. The primary function of the timed-access feature is to protect against accidental
disabling of the watchdog timer by an “out-of-control” device. This allows the watchdog timer to reset
the system in the event of program execution failure.
The following hypothetical example demonstrates how a single bit change can corrupt program
execution. The timed-access procedure protects against an accidental write to the EWT bit by the errant
code, allowing the watchdog timer reset function to reset the device. While this is a purely fictitious
example, it illustrates how the watchdog timer and timed-access feature make the high-speed
microcontroller minimize the effect of accidental code corruption. Note: Timed access is not optional and
must be supported if the protected bits are used. This example simply helps explain the category of
problem that the timed access prevents.
