Configuring rsh, Rsh overview, Configuration procedure – H3C Technologies H3C SecPath F1000-E User Manual
Page 158: Rsh configuration example, Network requirements
147
Configuring RSH
The RSH configuration is available only at the CLI.
RSH overview
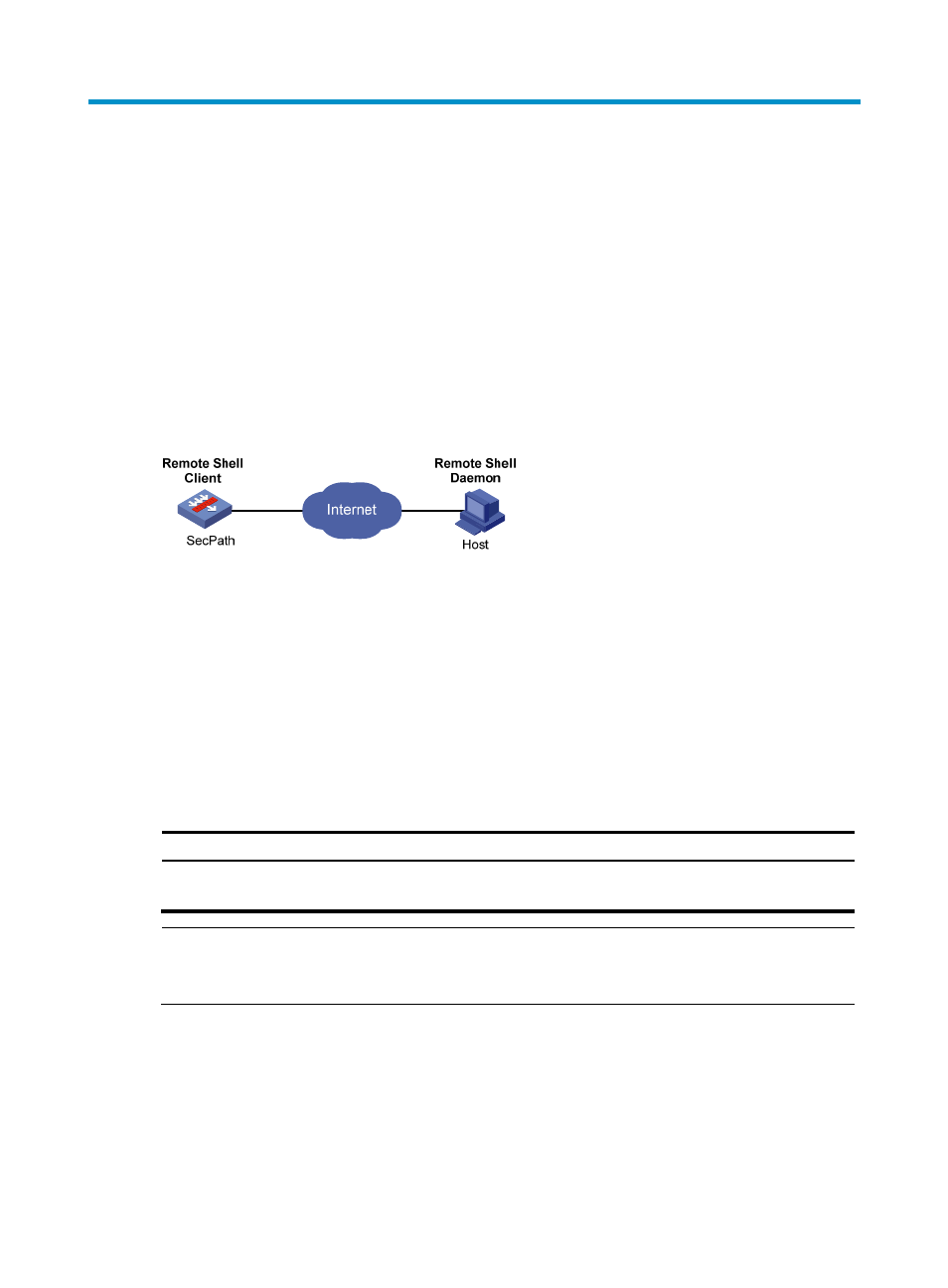
Remote shell (RSH) allows you to execute the commands provided by the operating system (OS) on a
remote host. The remote host must run the RSH daemon.
The firewall can serve as an RSH client and provides the rsh command as the tool for the RSH
feature.
shows a typical application scenario.
Figure 66 RSH application
The RSH daemon supports authentication of an RSH client by the username. To enable or disable the RSH
daemon on Windows NT, 2000, XP, or 2003, use the Services component.
Configuration procedure
Complete the following tasks before you configure RSH:
•
Run RSH daemon on the remote host.
•
Make sure that the firewall and the remote host have IP connectivity between them.
Execute a remote host’s OS command from the firewall by executing the following command:
Task Command
Remarks
Execute an OS command of a
remote host.
rsh host [ user username ]
command remote-command
Available in user view
NOTE:
If RSH daemon authentication is enabled on the remote host, you must provide the username configured
on the remote host in advance.
RSH configuration example
Network requirements
As shown in
, run Windows 2000 on the remote host and start the RSH daemon service on it.
Use the router to set the time of the remote host remotely.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
