The built-in administrator, About manual logon – Grass Valley iTX System v.2.6 User Manual
Page 75
Security in an iTX system
The Security Tool simplifies the task of registering users and groups by enabling you to import
the details from a Windows NT network.
There is no need to manually register workstations or applications; this happens automatically.
See later in this section, "About the Security Tool".
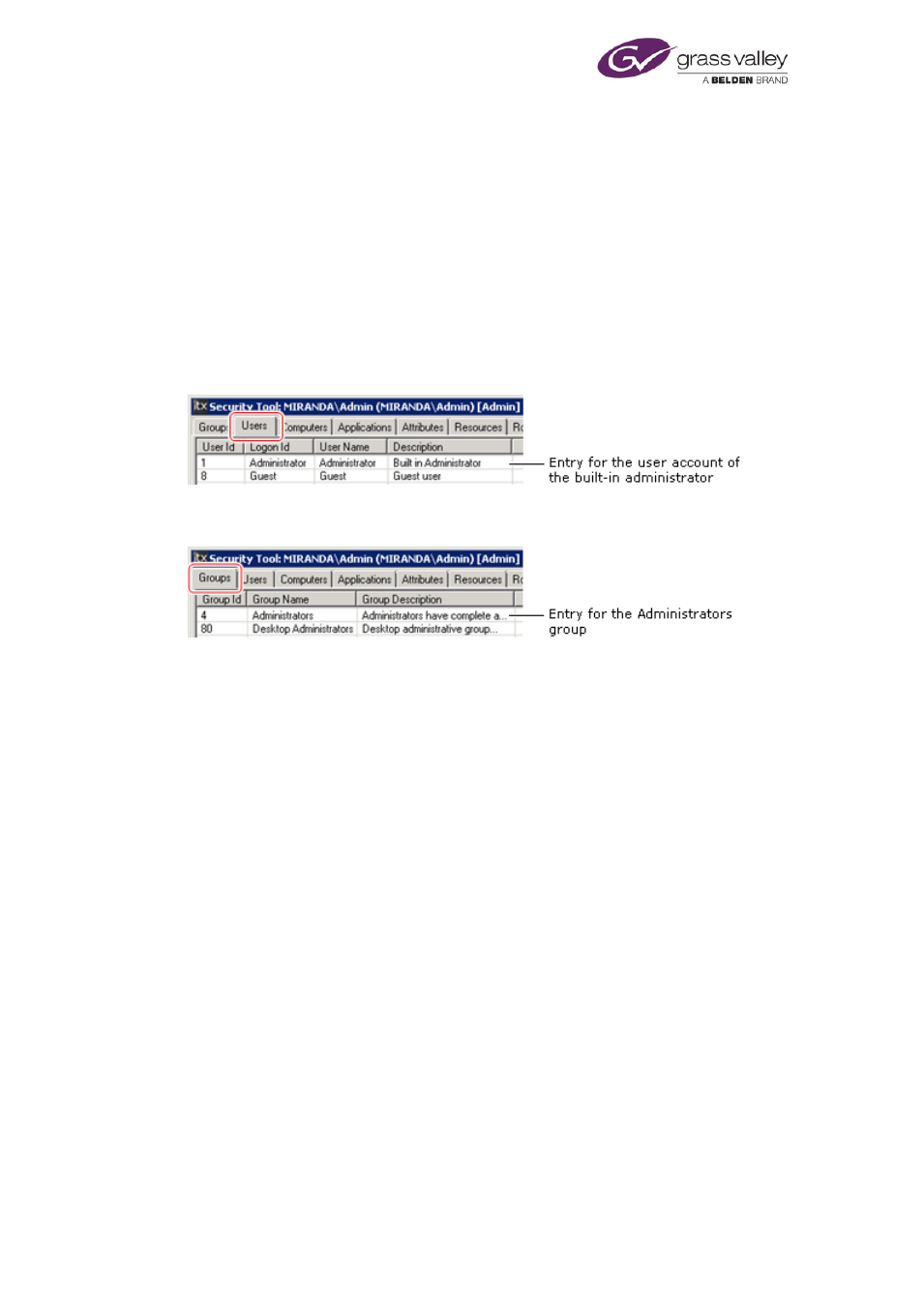
The built-in administrator
For its own configuration, the security system includes a built-in user account that has full
administrative rights in the system; this account has the user name "Administrator". You can
use it to configure different aspects of the security system.
An entry for the account appears under the Users tab of the Security Tool:
The built-in administrator is a member of the Administrators group. An entry for this appears
under the Groups tab:
Any user you add to this group gets the same rights for configuring the security system as the
built-in administrator. No other user can change the security-system configuration.
Note:
•
There are other types of administrator in an iTX system – for instance, an iTX Desktop
administrator and a resource-type administrator. The built-in administrator for the
security system does not necessarily have the rights that these have for different parts
of the wider iTX system. Where you want the built-in administrator to be able to
perform other administrator roles, you should use the Security Tool to add the
necessary rights to the built-in administrator account.
About Manual Logon
Any user with the Manual Logon security attribute can log onto certain iTX services and
Desktop components with their own user rights.
The attribute is particularly useful when it is necessary to temporarily override restrictions that
apply to an operator who is logged onto an iTX Desktop; for instance, to allow a supervisor to
perform an action that the operator does not have the right to perform.
By default, only the built-in administrator has the Manual Logon attribute.
You may use the Security Tool to assign the attribute to other users. When you do this, you
should set passwords in the security system for these users. Not doing so weakens the security
system: it makes it possible for anyone who knows or can successfully guess a user name to
change the configuration without having to enter a password.
March 2015
System Administrator Guide
Page 75 of 404
