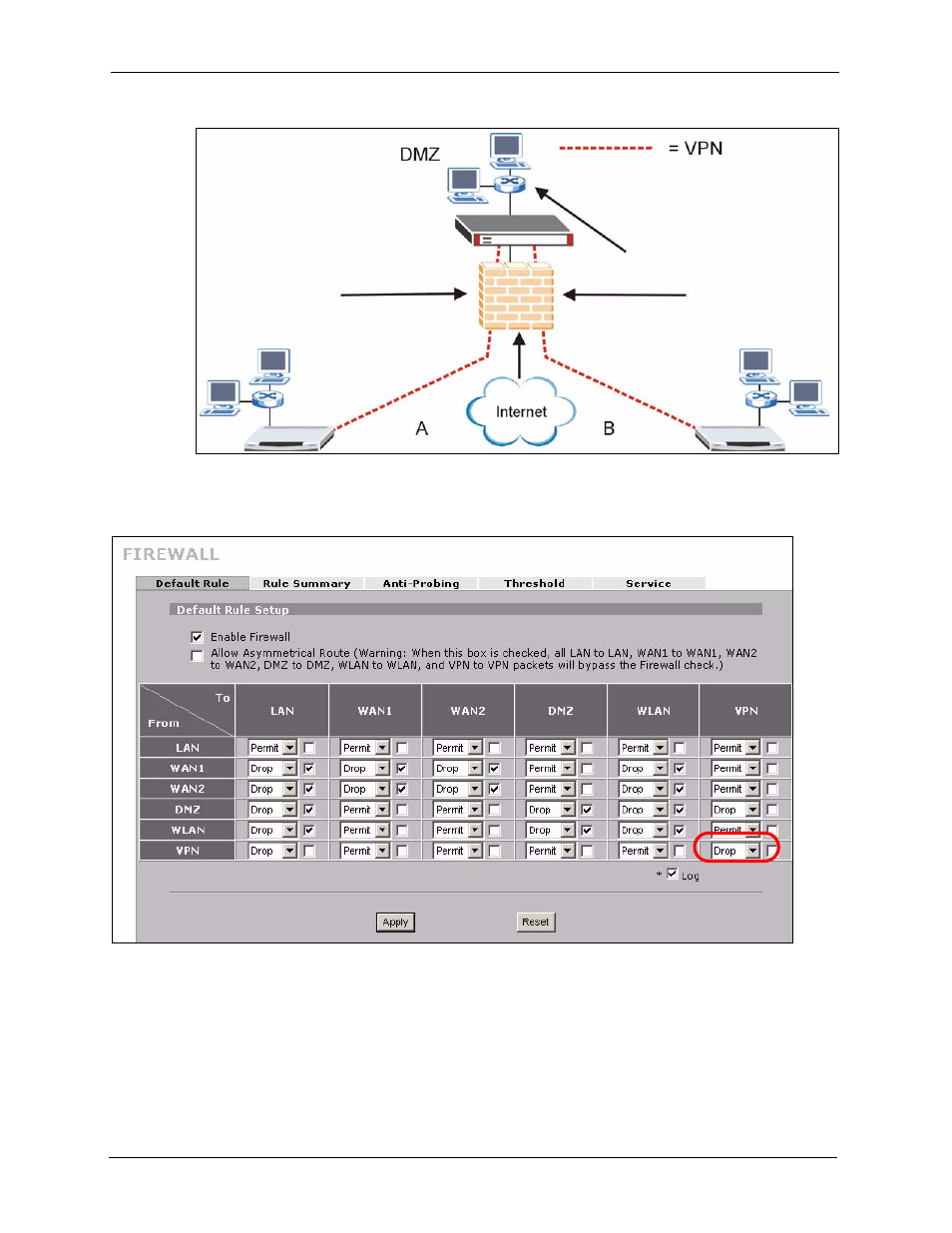
4 security considerations, Figure 110 from vpn to vpn example – ZyXEL Communications 5 Series User Manual
Page 226
See also other documents in the category ZyXEL Communications Hardware:
- ISDN Terminal Adapter Omni.Net Lite (84 pages)
- ZYAIR G-360 V2 (2 pages)
- DMA-1000 Series (192 pages)
- PLA-450 (2 pages)
- EXT-108 (2 pages)
- P-2602HWLNI (496 pages)
- ZyXEL ZyWALL 2WG (730 pages)
- P841C (41 pages)
- Network Device P-2302 (359 pages)
- P-870M-I (2 pages)
- P-661HW Series (383 pages)
- Prestige 310 (161 pages)
- 802.11g Wireless Access Point ZyXEL G-560 (144 pages)
- P-2602HW (2 pages)
- Prestige 2602R Series (450 pages)
- Prestige 623ME-T (253 pages)
- omni.net LCD series (53 pages)
- ZyXEL ZyAIR B-1000 (231 pages)
- P-2302HWUDL-P1 Series (368 pages)
- ZyXEL ZyWALL 5 (667 pages)
- Prestige 645R (180 pages)
- ZYWALL IDP 10 (42 pages)
- 802.11g Wireless Firewall Router P-320W (215 pages)
- PRESTIGE 660R-6XC (6 pages)
- 56K Plus II (88 pages)
- P-2802HW-i (2 pages)
- ZYAIR AG-200 (2 pages)
- POWERLINE PL-100 (33 pages)
- HomePlug AV DMA-1100P (198 pages)
- Access Router P-660R-T (9 pages)
- omni.net LCD+M (186 pages)
- G-162 (85 pages)
- PL-100 (33 pages)
- ZyXEL ZyAIR A-6000 (46 pages)
- ZyXEL ZyAIR AG-225H (14 pages)
- 2304R-P1 (124 pages)
- XTREMEMIMO M-302 (2 pages)
- nbg334s (2 pages)
- P-793H 601156 (1 page)
- Ethernet Extension Card EEC1020 (8 pages)
- P-871M (26 pages)
- Prestige 128L (114 pages)
- P-2812HNU-51c (2 pages)
- ZyWALL SSL 10 (64 pages)