Traffic redirecting, Vlan mapping, 10 vlan mapping – H3C Technologies H3C WX3000 Series Unified Switches User Manual
Page 354
37-10
z
Forwarding the conforming packets or nonconforming packets.
z
Marking the conforming packets or nonconforming packets with 802.1p precedence and then
forwarding the packets.
z
Marking the conforming packets or nonconforming packets with DSCP precedence and forwarding
the packets.
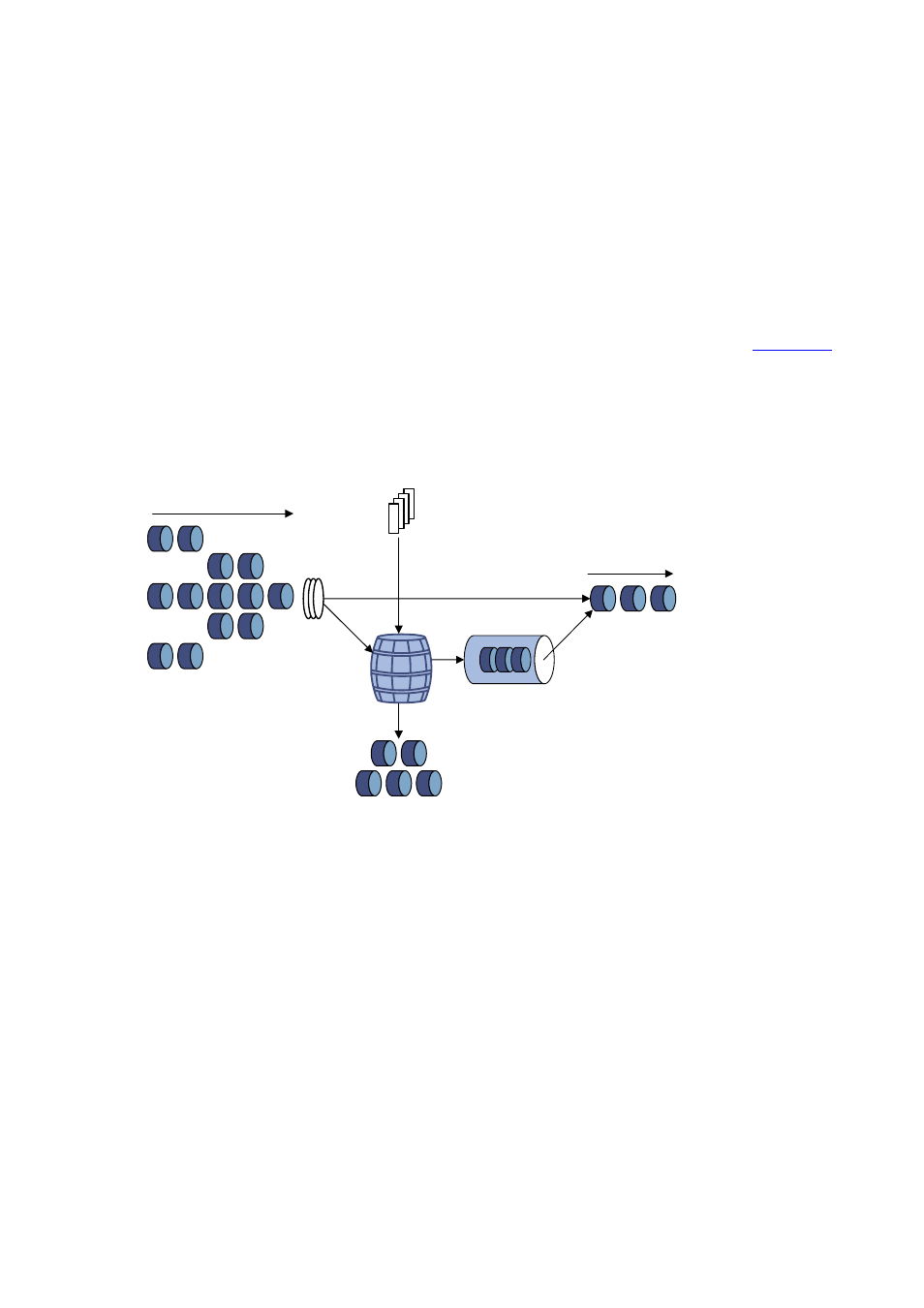
Traffic shaping
Traffic shaping is a measure to regulate the output rate of traffic actively. Its typical application is to
control local traffic output based on the traffic policing indexes of downstream network nodes.
The major difference between traffic shaping and traffic policing is that the packets to be dropped in
traffic policing are cached in traffic shaping——usually in buffers or queues, as shown in
.
When there are enough tokens in the token bucket, the cached packets are sent out evenly. Another
difference between traffic policing and traffic shaping is that traffic shaping may increase the delay while
traffic policing hardly increases the delay.
Figure 37-6
Diagram for traffic shaping
Token bucket
Drop
Packet
classification
Packets to be sent
through this port
Continue to send
Put tokens in the bucket at the set rate
Queue
For example, if the device A sends packets to the device B. The device B will perform traffic policing on
packets from the device A to drop the packets beyond the specification.
In order to avoid meaningless packet loss, you can perform traffic shaping on the packets on the egress
of the device A and cache the packets beyond the traffic policing specification in the device A. When the
next packets can be sent, the packets cached in the buffer queues will be taken out and sent. In this way,
all the packets sent to the device B conforms to the traffic specification of the device B.
Traffic Redirecting
Traffic redirecting identifies traffic using ACLs and redirects the matched packets to specific ports. By
traffic redirecting, you can change the way in which a packet is forwarded to achieve specific purposes.
VLAN Mapping
VLAN mapping identifies traffics using ACLs and maps the VLAN tags carrier in matched packets to
specific VLAN tags. By employing VLAN mapping on a device connecting user networks to the carrier
