Aaa configuration examples, Remote radius authentication of telnet/ssh users – H3C Technologies H3C WX3000 Series Unified Switches User Manual
Page 276
25-24
To do…
Use the command…
Remarks
Clear HWTACACS message
statistics
reset hwtacacs statistics
{ accounting |
authentication
| authorization | all }
Delete buffered non-response
stop-accounting requests
reset stop-accounting-buffer
hwtacacs-scheme
hwtacacs-scheme-name
Available in user view.
AAA Configuration Examples
Remote RADIUS Authentication of Telnet/SSH Users
The configuration procedure for remote authentication of SSH users by RADIUS server is similar to that
for Telnet users. The following text only takes Telnet users as example to describe the configuration
procedure for remote authentication.
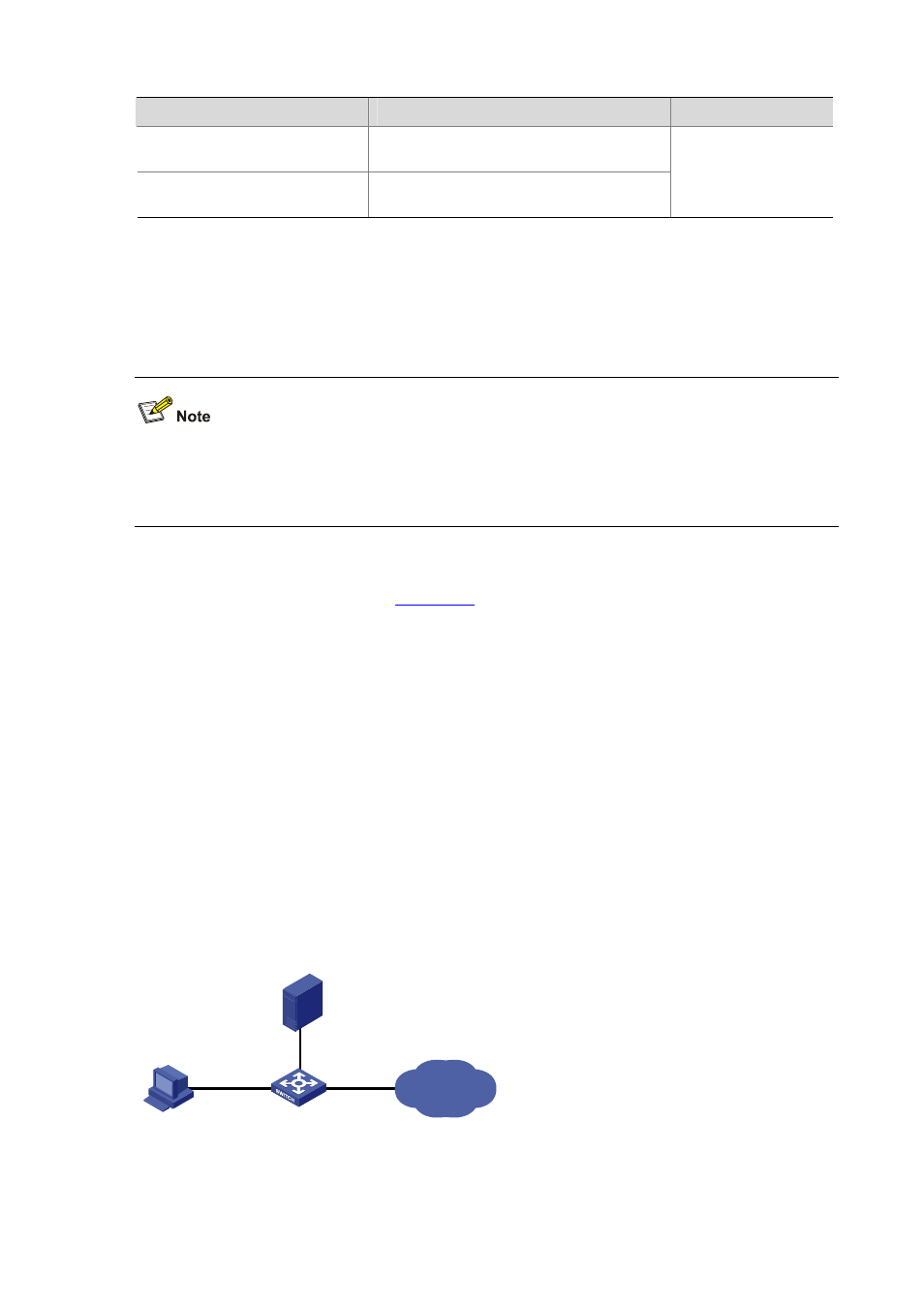
Network requirements
In the network environment shown in
, you are required to configure the device so that the
Telnet users logging into the switching engine are authenticated by the RADIUS server.
z
A RADIUS authentication server with IP address 10.110.91.164 is connected to the device.
z
On the device, set the shared key it uses to exchange messages with the authentication RADIUS
server to "aabbcc".
z
A CAMS server is used as the RADIUS server. You can select extended as the server-type in a
RADIUS scheme.
z
On the RADIUS server, set the shared key it uses to exchange messages with the device to
"aabbcc," set the authentication port number, and add Telnet user names and login passwords.
The Telnet user names added to the RADIUS server must be in the format of userid@isp-name if you
have configured the device to include domain names in the user names to be sent to the RADIUS
server in the RADIUS scheme.
Figure 27-1
Remote RADIUS authentication of Telnet users
Internet
Telnet user
Authentication server
10. 110.91. 164
