3 dhcpv6 snooping typical application, Dhcp, Nooping – PLANET XGS3-24040 User Manual
Page 244: Ypical, Pplication
Chapter 32 DHCPv6 Snooping Configuration
32-5
32.3 DHCPv6 Snooping Typical Application
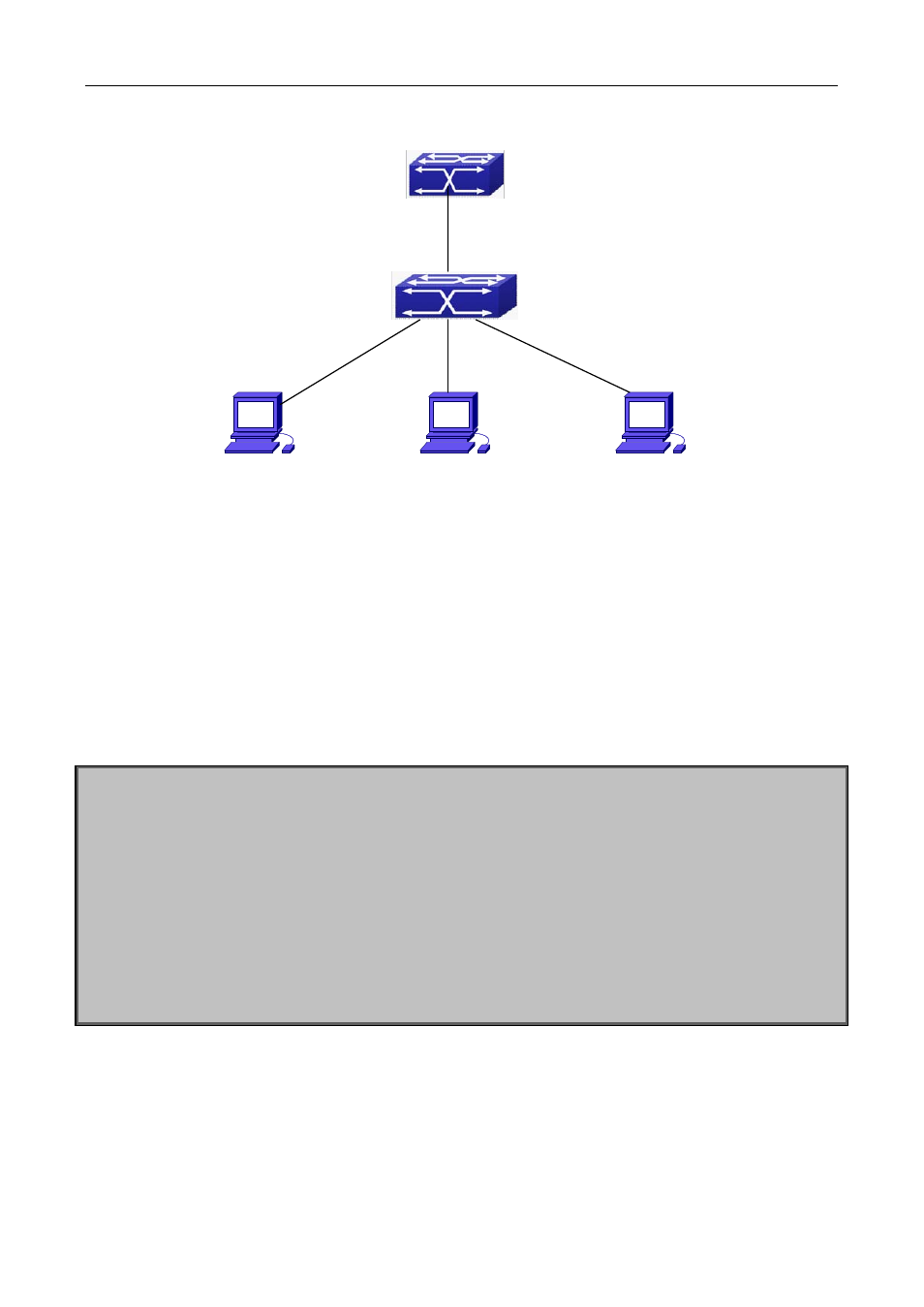
Figure 4-1 Sketch Map of preventing lawless DHCPv6 Server
As showed in the above chart, MAC-AA and MAC-BB devices are normal users, they are connected to the
non-trusted ports 1/2 and 1/3 of the switch, and obtain IP 2010::3 and IP 2010::4 through DHCPv6 Client;
DHCPv6 Server are connected to the trust port 1/1 of the switch; the malicious user Mac-CC is connected to
the non-trusted port1/4, it tries to fake DHCPv6 Server. Setting DHCPv6 Snooping on the switch will
effectively detect and prevent this kind of network attack.
Configuration sequence is:
switch#
switch#config
switch(config)#ipv6 dhcp snooping enable
switch(config)#ipv6 dhcp snooping binding enable
switch(config)#interface ethernet 1/1
switch(Config-Ethernet 1/1)#ipv6 dhcp snooping trust
switch(Config-Ethernet1/1)#exit
switch(config)#interface ethernet 1/4-10
switch(Config-Port-Range)#ipv6 dhcp snooping action shutdown
switch(Config-Port-Range)#
DHCPv6 Server
Interface E1/1
Interface E1/2
Interface E1/3
Interface E1/4
MAC-AA
MAC-BB
MAC-CC
Virtual DHCPv6 Server
