N in, Figure 64 – H3C Technologies H3C SecPath F1000-E User Manual
Page 75
65
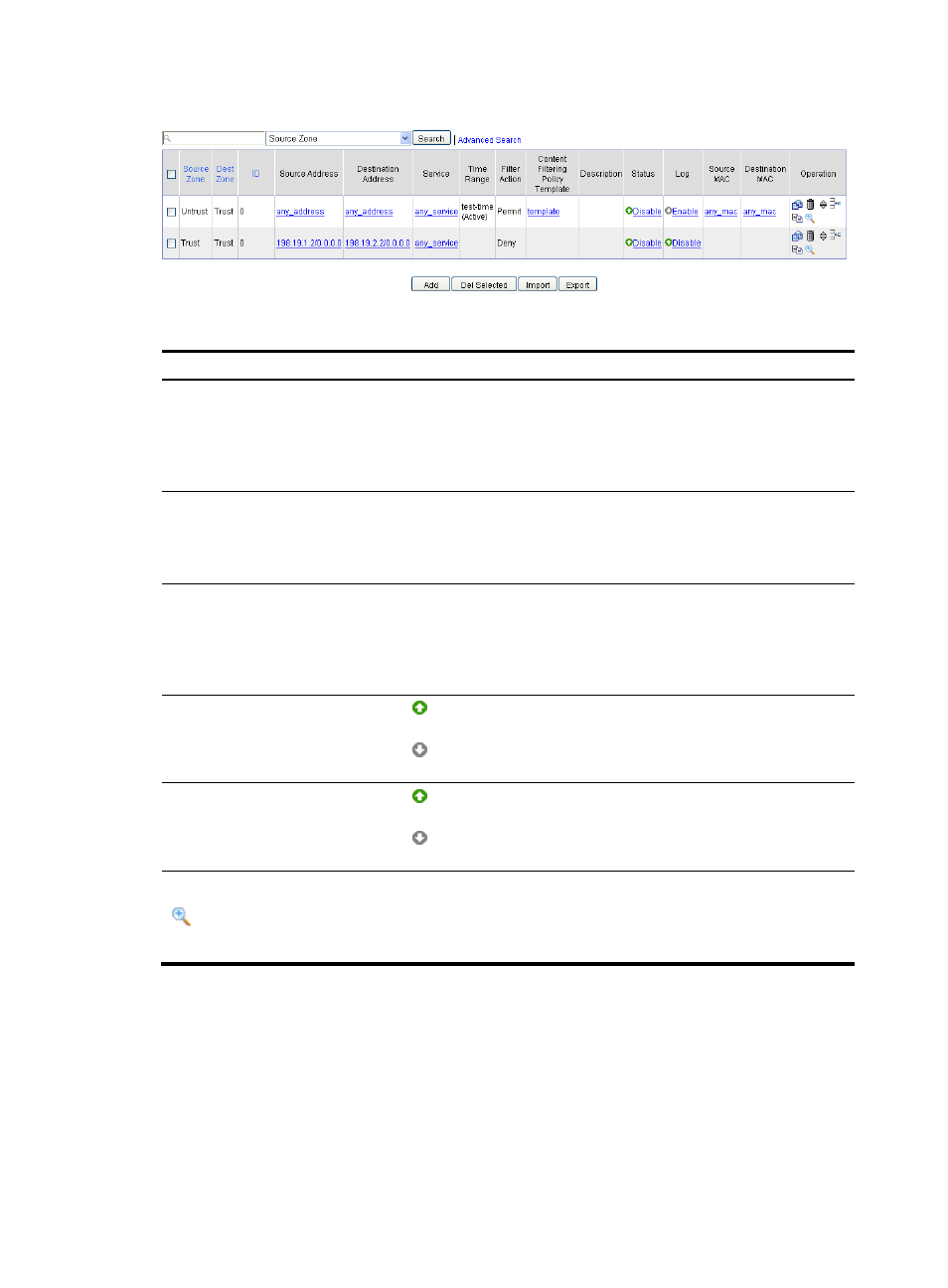
Figure 64 List of interzone policy rule list
Table 21 Operations you can perform on the list
Field Operation
Source Address/Destination
Address/Source
MAC/Destination MAC
Click an address (except any_address and any_mac) to enter the address
resource configuration page, where you can view and modify the address
resource configuration.
For information about address resources, see "Address resource
configuration."
Service
Click a service name (except any_service) to enter the service configuration
page, where you can view and modify the service configuration.
For information about service resources, see "Service resource
configuration."
Content Filtering Policy Template
Click a template name to enter the content filtering policy template
configuration page, where you can view and modify the template
configuration.
For information about content filtering template, see Attack Protection
Configuration Guide.
Status
•
shows that the interzone policy rule is enabled. You can click Disable
to disable the interzone policy rule.
•
shows that the interzone policy rule is disabled. You can click Enable
to enable the interzone policy rule.
Log
•
shows that logging is enabled for the interzone policy rule. You can
click Disable to disable the logging function.
•
shows that logging is disabled for the interzone policy rule. You can
click Enable to enable the logging function.
in the Operation column
Click the icon of an interzone policy rule to view the logs for traffic that
matches the interzone policy rule.
For information about interzone policy logs, see System Management and
Maintenance Configuration Guide.
- H3C SecPath F5000-A5 Firewall H3C SecPath F1000-A-EI H3C SecPath F1000-E-SI H3C SecPath F1000-S-AI H3C SecPath F5000-S Firewall H3C SecPath F5000-C Firewall H3C SecPath F100-C-SI H3C SecPath F1000-C-SI H3C SecPath F100-A-SI H3C SecBlade FW Cards H3C SecBlade FW Enhanced Cards H3C SecPath U200-A U200-M U200-S H3C SecPath U200-CA U200-CM U200-CS
